HITRUST vs. SOC 2 – Key Differences
Deciding between HITRUST and SOC 2 can feel complicated when working with information security and compliance frameworks. Each framework demonstrates an organization’s commitment to data protection, but they differ significantly in purpose and requirements.
SOC 2 provides flexibility for assessing security controls, while HITRUST offers a structured, certifiable approach with a strong emphasis on healthcare compliance.
Knowing these differences helps determine the best fit for your organization. This guide explains the distinctions between HITRUST and SOC 2 to simplify your decision-making process.
Let’s get started!
HITRUST Overview
HITRUST (Health Information Trust Alliance) is a not-for-profit organization that created the HITRUST CSF (Common Security Framework). The CSF unifies multiple security and privacy regulations into a single control set.

It initially focused on healthcare requirements like HIPAA and HITECH but expanded to include mappings to ISO 27001, PCI DSS, SOC 2, and more. This flexibility makes HITRUST valuable for organizations handling sensitive information across industries, though it remains highly adopted in healthcare.
HITRUST certification typically costs between $60,000 and $200,000. The higher cost reflects its larger control set and more extensive audit requirements, which require greater time and resource investment compared to SOC 2.
Why Organizations Use HITRUST
HITRUST offers a recognized approach for managing security and compliance across industries. Its framework helps organizations build trust and handle regulatory challenges more effectively.
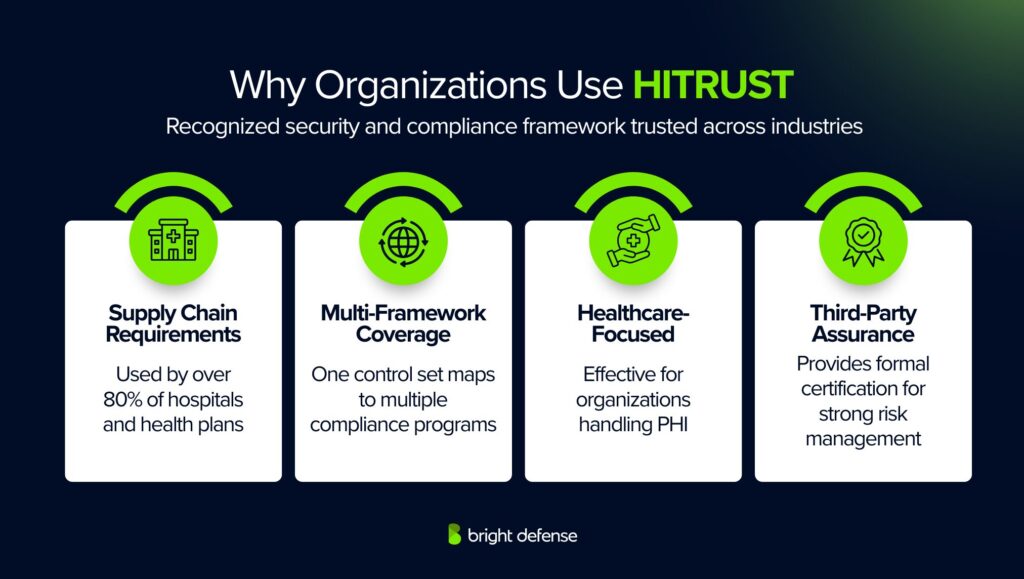
1. Supply Chain Requirements
Over 80% of hospitals, health systems, and health plans require HITRUST CSF for vendors and partners. Meeting this requirement often becomes essential to maintain or win healthcare contracts.
2. Multi-Framework Coverage
HITRUST maps one control set to multiple frameworks such as HIPAA, ISO 27001, and NIST. This reduces the need for separate compliance programs and avoids duplicated effort.
3. Healthcare-Focused
The framework works well for organizations managing Protected Health Information (PHI). It supports strict healthcare regulations like HIPAA while addressing privacy and security needs in the healthcare sector.
4. Third-Party Assurance
HITRUST provides a formal certification instead of a simple attestation. This offers strong evidence of security controls and reduces the need for repeated vendor risk assessments.
Specialties and Strengths of HITRUST
HITRUST provides recognized assurance for security and compliance, offering industry trust, flexible controls, third-party validation, and unified governance for efficient compliance management.

1. Broad Scope
HITRUST covers 19 security and privacy domains, offering significantly more controls than SOC 2. This broad approach helps organizations address detailed regulatory and risk requirements in one framework.
2. Industry Recognition
HITRUST is well known in healthcare and other highly regulated industries. Its certification signals strong security and compliance practices, often required by hospitals, health systems, and large enterprise partners.
3. Integration with SOC 2
HITRUST controls map directly to SOC 2 Trust Service Criteria. This allows organizations to complete a combined SOC 2 + HITRUST CSF audit, reducing redundant effort and producing reports accepted by multiple stakeholders.
SOC 2 Overview
SOC 2 (System and Organization Controls 2) is a security and compliance framework designed by the American Institute of Certified Public Accountants (AICPA).
It focuses on how service organizations manage and protect customer data, emphasizing internal controls and operational practices rather than financial reporting.

SOC 2 applies broadly across industries, especially for companies providing technology services, SaaS platforms, and cloud-based solutions. It is comparatively less expensive, typically costing $20,000 to $100,000, and offers flexibility that makes it easier for startups and mid-sized companies to adopt.
The SOC 2 framework revolves around five Trust Service Criteria (TSC):
- Security – Protection of systems against unauthorized access.
- Availability – Ensuring systems are operational and accessible as agreed.
- Processing Integrity – Assurance that data processing is accurate and reliable.
- Confidentiality – Safeguarding information designated as confidential.
- Privacy – Handling and protecting personal data appropriately.
Why Organizations Use SOC 2
Organizations pursue SOC 2 compliance for several reasons that support their operational and business goals. These are some of the main motivations:
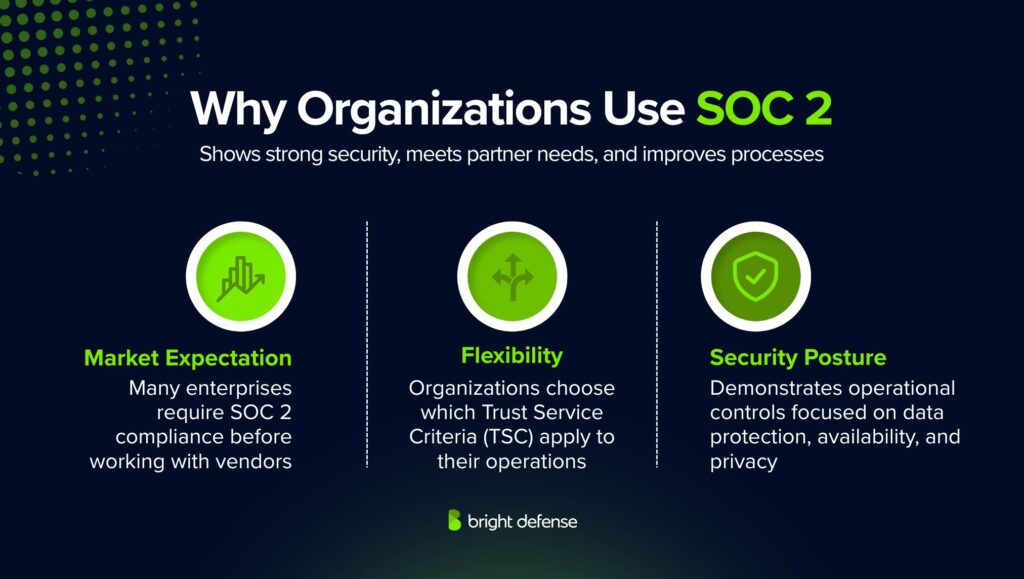
1. Flexibility
SOC 2 allows organizations to select the Trust Service Criteria (TSC) that best fit their operations. This adaptability helps align the audit with specific business models and risk profiles.
2. Market Expectation
Many enterprises, especially in technology and cloud services, require vendors to hold a SOC 2 report before entering into business relationships. This has made SOC 2 a standard expectation in vendor due diligence.
3. Security Posture
A SOC 2 report demonstrates that an organization has effective operational controls focused on data protection, availability, processing integrity, confidentiality, and privacy. This helps build trust with customers and partners.
Specialties and Strengths of SOC 2
SOC 2 stands out as a trusted standard for demonstrating security and compliance practices. It offers flexibility, independent validation, and reporting options suited to various industries and business models.
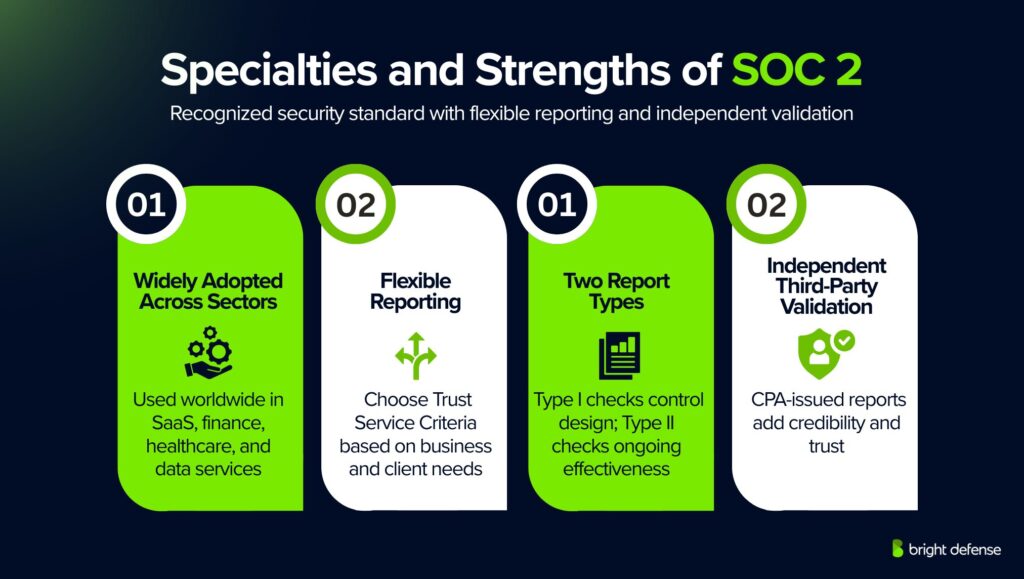
1. Widely Adopted Across Sectors
Initially developed in the U.S., SOC 2 has grown into a globally recognized benchmark. It is commonly expected in SaaS, financial services, healthcare technology, and data processing industries as a prerequisite for vendor partnerships.
2. Flexible Reporting
SOC 2 lets organizations choose which Trust Service Criteria (TSC) best fit their business model and client needs. A SaaS provider might focus on Security and Availability, while a payment processor might add Confidentiality and Privacy.
3. Two Report Types
- Type I evaluates the design of controls at a single point in time, providing insight into readiness.
- Type II measures operating effectiveness over a period, typically 6–12 months, showing sustained control performance.
4. Independent Third-Party Validation
SOC 2 reports are issued by certified public accountants (CPAs) or accounting firms. This independent review adds credibility to an organization’s security and compliance program.
HITRUST vs SOC 2: A Detailed Comparison
Both HITRUST and SOC 2 are widely trusted for improving security and meeting compliance goals. Let’s find out where each one’s strength lies and how they differ.
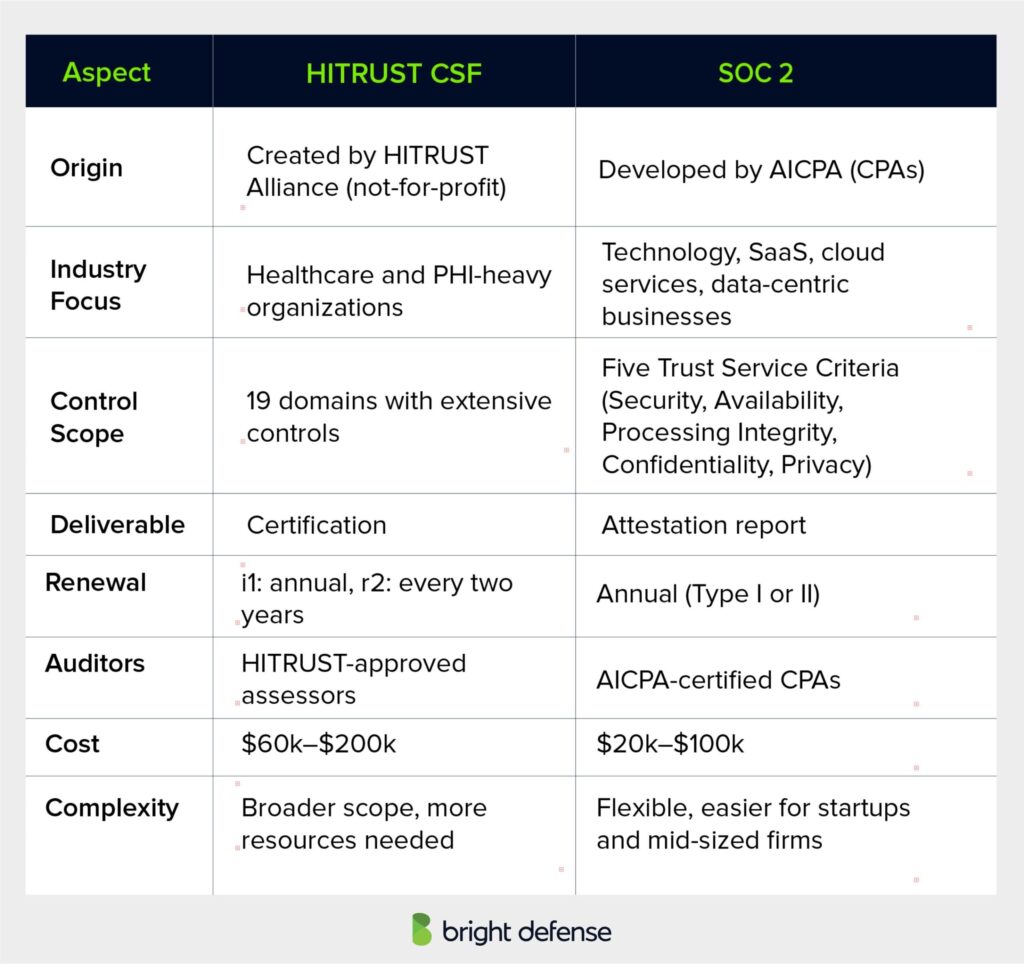
1. Purpose and Scope
HITRUST and SOC 2 are both frameworks designed to strengthen data security and build trust with partners, clients, and regulators. However, their scope and focus differ.
- HITRUST CSF acts as an overarching framework that integrates multiple standards such as HIPAA, ISO 27001, PCI DSS, and even SOC 2 controls. It is structured to support regulated industries, particularly healthcare organizations managing Protected Health Information (PHI).
- SOC 2 focuses on demonstrating how a company’s internal systems protect data through five Trust Service Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. It is widely used by technology companies, SaaS providers, and cloud service operators.
2. Deliverables and Audit Differences
The output from each framework differs:
- HITRUST provides a certification that confirms an organization’s controls meet HITRUST CSF requirements. This certification carries significant weight in healthcare and highly regulated industries.
- SOC 2 delivers an attestation report, confirming an organization has adequate controls in place. It is often required in vendor onboarding processes, particularly in U.S. technology markets.
Audits also differ:
- HITRUST assessments are performed by HITRUST-approved external assessors and can be either i1 (annual) or r2 (every two years) depending on the depth of review.
- SOC 2 audits are performed by AICPA-certified public accountants (CPAs) and result in either a Type I (point-in-time) or Type II (operational period) report.
3. Cost and Complexity
HITRUST certifications are generally more expensive and resource intensive, with costs ranging from $60,000 to $200,000 depending on organization size and assessment type. SOC 2 is comparatively less expensive, typically $20,000 to $100,000, and more flexible, making it easier for startups and mid sized companies to adopt.
HITRUST’s broader scope covering 19 control domains requires a higher maturity level in governance and risk management, while SOC 2 focuses on core operational controls linked to customer data security.
4. Integration and Dual Audits
- SOC 2 + HITRUST CSF (no certification) – Performed by an AICPA CPA firm using HITRUST controls. Organizations do not have to choose one framework exclusively. Because HITRUST CSF maps directly to SOC 2’s Trust Service Criteria, companies can perform combined audits. Two common approaches exist:
- SOC 2 + HITRUST CSF Certification – Requires an AICPA CPA firm that is also a HITRUST-approved assessor, resulting in both a SOC 2 attestation and a HITRUST certification.
HITRUST or SOC 2 – Which One Should I Go For?
Choosing between HITRUST and SOC 2 often depends on your industry, regulatory needs, and customer expectations. Both frameworks demonstrate strong security practices but serve different purposes and audiences.
Choose HITRUST if you:
- Work in healthcare or serve healthcare clients that require strict adherence to HIPAA, HITECH, or other regulated data environments.
- Need a single framework that covers multiple standards like HIPAA, ISO 27001, NIST, and PCI DSS without running separate compliance programs.
- Require a formal certification rather than just an attestation, giving clients and partners stronger assurance.
- Face vendor onboarding requirements from hospitals, health systems, or health plans that specifically request HITRUST CSF certification.
- Have the budget and resources to handle a larger, more detailed control set and higher assessment costs, typically $60,000 to $200,000.
Choose SOC 2 if you:
- Operate in technology, SaaS, or cloud-based services where customers or partners expect SOC 2 reports as part of vendor due diligence.
- Want flexibility in selecting controls based on your business model and risk profile, using the five Trust Service Criteria (Security, Availability, Processing Integrity, Confidentiality, and Privacy).
- Need a lower-cost, faster-to-implement option, with typical costs ranging from $20,000 to $100,000.
- Want to show independent validation of your data security posture without committing to a full certification process.
- Prefer the option of incremental growth, starting with SOC 2 Type I and expanding to SOC 2 Type II for longer-term assurance.
Choose Both HITRUST and SOC 2 if you:
- Serve healthcare clients but also have broader technology or SaaS customers that expect SOC 2 reports.
- Want to consolidate multiple compliance requirements into a single process, using HITRUST mappings to SOC 2 Trust Service Criteria.
- Seek to avoid repeated audits by completing a combined SOC 2 + HITRUST assessment.
- Need both the formal certification of HITRUST and the wide market recognition of SOC 2 to compete across industries.
- Plan to demonstrate the highest possible assurance level for security, privacy, and compliance across diverse client and regulatory needs.
Which One is More Expensive, SOC 2 or HITRUST?
HITRUST is more expensive than SOC 2 in both direct costs and internal effort for most organizations. SOC 2 programs commonly fall in the $10,000 to $150,000 range for audit and preparation combined, with first year internal labor often under 1,000 hours, while HITRUST programs frequently reach six figures due to assessor fees, required platform and QA fees, remediation effort, and longer timelines that drive higher internal staffing costs.
Which is more popular overall, SOC 2 or HITRUST?
SOC 2 is more popular overall, while HITRUST is more popular inside healthcare. SOC 2 is positioned as a widely accepted, cross-industry trust report that many SaaS and enterprise vendors pursue for broad customer due diligence, which drives higher overall adoption across industries. HITRUST is heavily concentrated in healthcare, where a 2018 HIMSS survey is commonly cited as showing 81% of US hospitals and health systems and 83% of health plans using HITRUST CSF, which reflects strong sector-specific uptake even if it does not exceed SOC 2 in total market usage.
Which Framework Has Higher Renewal Friction Year Over Year?
HITRUST has higher renewal friction year over year than SOC 2 because it requires formal recertification, prescriptive control scoring, mandatory QA review, and ongoing platform fees, whereas SOC 2 renewals typically reuse existing controls, focus on incremental evidence collection, and follow a predictable annual audit cycle without centralized approval or certification scoring.
Why Combine HITRUST and SOC 2?
Adopting both HITRUST and SOC 2 creates a stronger foundation for security and compliance. When used together, these frameworks provide a broader perspective on risk management and reduce duplicate assessment efforts, while also signaling a firm commitment to safeguarding data.
Although each framework addresses specific areas, applying them in tandem gives organizations flexibility to meet unique compliance needs. Common approaches include:
1. Parallel SOC 2 and HITRUST Reporting
Some organizations perform assessments under both frameworks to cover all major security and privacy requirements.
- SOC 2: Concentrates on principles such as security, availability, processing integrity, confidentiality, and privacy of data within service environments.
- HITRUST Reporting: Uses the HITRUST Common Security Framework (CSF) for either a full assessment or self-assessment, generating a CSF report based on the results.
2. SOC 2 Audit with HITRUST Certification
A more rigorous path involves pursuing SOC 2 while also completing a certified HITRUST audit.
- HITRUST Certification: Confirms through formal auditing that controls align with HITRUST CSF requirements, resulting in official certification recognized across industries.
- SOC 2: Validates that security and privacy controls meet trusted standards.
Overlapping Areas and Complementary Use
While HITRUST and SOC 2 are designed with different primary focuses and industries in mind, there are several overlapping areas in their security controls and objectives. In some cases, organizations may find it beneficial to leverage both frameworks to achieve comprehensive compliance and robust data protection. Here’s how HITRUST and SOC 2 can complement each other:
1. Common Security Controls
HITRUST and SOC 2 emphasize the importance of strong security controls to protect sensitive information. Some of the common controls and practices include:
- Access Control: Both frameworks require stringent access control measures to ensure that only authorized personnel can access sensitive data.
- Incident Response: Both emphasize the need for a robust incident response plan to quickly identify, manage, and mitigate security incidents.
- Risk Assessment: Regular risk assessments are crucial in both frameworks to identify potential vulnerabilities and implement appropriate safeguards.
- Security Policies and Procedures: Documented security policies and procedures are required to ensure consistent and effective security practices.
2. Dual Compliance Benefits
Organizations operating in the healthcare sector or those providing services to healthcare clients may benefit from achieving both HITRUST and SOC 2 compliance. Dual compliance can offer several advantages:
- Enhanced Trust and Assurance: Demonstrating compliance with both frameworks can provide higher assurance to clients, stakeholders, and regulators about the organization’s commitment to data security.
- Broader Market Reach: By meeting the HITRUST and SOC 2 requirements, organizations can appeal to a wider range of clients, including those in healthcare and other sectors.
- Comprehensive Security Posture: Leveraging the strengths of both frameworks can result in a more comprehensive and resilient security posture, addressing a wider array of potential threats and vulnerabilities.
3. Practical Implementation
To achieve dual compliance, organizations should:
- Conduct a Unified Gap Analysis: Assess the current state of security controls against HITRUST and SOC 2 requirements to identify common gaps and unique requirements.
- Develop Integrated Policies: Create security policies and procedures that address the requirements of both frameworks, ensuring that controls are comprehensive and cohesive.
- Streamline Audit Processes: Coordinate audits and assessments for both frameworks to reduce redundancy and optimize resource use.
Organizations can strategically leverage HITRUST and SOC 2 to enhance their security and compliance efforts by recognizing the overlapping areas and potential for complementary use. This approach not only strengthens data protection but also provides a competitive edge in the marketplace by demonstrating a robust commitment to cybersecurity across multiple standards.
Final Thoughts
Choosing between HITRUST and SOC 2 depends on your industry focus and compliance goals. HITRUST offers a detailed, prescriptive framework suited for healthcare and organizations needing alignment with multiple regulations. SOC 2 provides flexibility for technology and service providers to demonstrate strong security practices relevant to their operations.
These frameworks can also complement each other. A SOC 2 report often supports the journey toward HITRUST certification, and combined reports are available for broader assurance.
The right choice comes from understanding your industry requirements, client expectations, and risk management priorities.

Bright Defense Delivers Continuous Compliance Solutions!
If you are ready to start your compliance journey, Bright Defense is here to help. Our monthly engagement model delivers a security program that meets frameworks including SOC 2, ISO 27001, NIST, HIPAA, PCI, HITRUST, and more. We leverage compliance automation to increase efficiency and lower the cost of compliance.
In addition, we offer vCISO services, penetration testing, vulnerability scanning, security awareness training, mobile device security, and more. Contact Bright Defense today to get started!
Frequently Asked Questions (FAQ)
HITRUST vs. SOC 2: HITRUST is a comprehensive framework specifically designed for the healthcare industry, integrating multiple regulations such as HIPAA into a single, certifiable standard. SOC 2, on the other hand, is a versatile compliance framework applicable across various industries, focusing on five trust service criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
HITRUST certification is a formal recognition that an organization’s security controls meet the rigorous requirements of the HITRUST Common Security Framework (CSF). Achieving this certification demonstrates a strong commitment to protecting sensitive information and adhering to healthcare regulations.
The HITRUST Common Security Framework (CSF) is an integrated and comprehensive set of security controls designed to help organizations manage compliance with various regulations and standards. It harmonizes multiple requirements into a single framework, making it easier for healthcare organizations to achieve compliance.
The trust services criteria are the foundation of the SOC 2 framework. They include Security, Availability, Processing Integrity, Confidentiality, and Privacy. These criteria are used to evaluate and report on the effectiveness of an organization’s security controls and practices.
The HITRUST framework is particularly beneficial for healthcare organizations due to its alignment with healthcare-specific regulations like HIPAA. It offers a comprehensive approach to managing information security and compliance, ensuring that organizations can effectively protect sensitive health information.
A HITRUST report is the result of a HITRUST assessment and certification process. It provides detailed information on an organization’s compliance with the HITRUST CSF, highlighting areas of strength and identifying any gaps that need to be addressed.
The HITRUST Alliance is the organization responsible for developing and maintaining the HITRUST Common Security Framework (CSF). It aims to provide a standardized approach to information security and regulatory compliance, particularly within the healthcare industry.
HITRUST helps improve an organization’s security program by providing a comprehensive and integrated framework that addresses various regulatory requirements. It emphasizes a risk-based approach to security, ensuring that organizations can effectively manage and mitigate risks to their information assets.
The applicable trust service criteria for your organization depend on the nature of your services and the type of data you handle. For example, if your organization processes and stores sensitive customer information, you may need to focus on criteria such as Security, Confidentiality, and Privacy.
HITRUST addresses information security by providing a detailed set of security controls and best practices within the HITRUST CSF. These controls are designed to protect sensitive information from unauthorized access, data breaches, and other security threats.
A compliance program is essential for data security because it ensures that an organization adheres to relevant regulations and standards. By following a structured compliance program, organizations can implement effective security measures to protect sensitive information and reduce the risk of data breaches.
The common security framework provided by HITRUST includes a wide range of security measures, such as access controls, encryption, incident response, and risk management. These measures are designed to ensure comprehensive protection of sensitive information and compliance with regulatory requirements.
Yes, SOC 2 is considered a security audit, focusing on an organization’s controls related to the Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy.
No, SOC 2 is not only for SaaS companies. While it is popular with SaaS and cloud service providers, industries such as healthcare, finance, and data centers also undergo SOC 2 audits because they handle customer data.
SOC 3 is not necessarily better than SOC 2. SOC 2 reports are detailed and restricted, while SOC 3 reports are high-level summaries meant for public distribution. Many organizations use both, depending on their audience.
HITRUST is used to provide a certifiable, prescriptive control framework that helps organizations manage cyber risk and show assurance, especially when they handle sensitive and regulated data like PHI. Many healthcare providers, payers, and health tech buyers use HITRUST certification as a vendor requirement because it offers a standardized way to evaluate third party security controls across many domains.
HIPAA is a U.S. federal healthcare privacy and security law that applies to covered entities and their business associates when they handle protected health information (PHI), and it can lead to regulatory enforcement and penalties if you do not comply. SOC 2 is a voluntary third party attestation report that evaluates whether a service organization’s controls meet the AICPA Trust Services Criteria, most commonly Security, and it is usually driven by customer and vendor risk requirements rather than a law.
NIST frameworks are guidance and control catalogs that organizations use to design and run security programs, and they are typically flexible and non-certifying on their own. HITRUST is a certifiable framework that packages requirements from multiple standards, including NIST, into a structured assessment model with defined scoring and assurance outputs, which makes it easier to use as evidence for customers and partners who want a single, repeatable validation.
Yes, HITRUST certification requires a validated assessment performed by an authorized external assessor, covering a broad range of security and privacy controls.
Yes, HITRUST CSF incorporates multiple standards, including the NIST Cybersecurity Framework (CSF) and NIST SP 800-53, making it aligned with NIST requirements.
Get In Touch



