Jean Santiago
February 25, 2025
What is Security as a Service? A 2025 Guide to SECaaS
Do you ever find that maintaining your business’s security feels overwhelmingly complex? Between navigating threats and fulfilling compliance demands, cybersecurity can seem like a daunting task.
This is precisely where Security as a Service (SECaaS) proves invaluable. Imagine having an expert team dedicated to managing all aspects of your cybersecurity—from data loss prevention and continuous monitoring to network security—freeing you to concentrate entirely on your business operations.
As the global SECaaS market is projected to exceed $19 billion by 2025, there has never been a better time to discover the benefits this service can offer your business.
What Is Security as a Service?
Security as a Service (SECaaS) is a cloud-delivered model that provides businesses with scalable, cloud-based security solutions to protect their systems, data, and users.
Instead of relying solely on existing infrastructure, organizations use SECaaS to access the latest security tools and expert support to address emerging threats in real time.
How Cloud Computing Powers Security as a Service
SECaaS integrates seamlessly into a cloud computing environment, making it easy to scale and manage.
Here’s a quick look at how it works:
- Connect to the cloud infrastructure. Businesses link their systems and data to the SECaaS provider’s cloud services.
- Deploy advanced threat protection. The provider’s tools deliver threat detection and protection across your network.
- Monitor and analyze user behavior. Through user behavior analytics, SECaaS identifies unusual activity that may signal advanced persistent threats or insider risks.
- Enable disaster recovery planning. The platform supports data protection and rapid recovery if an attack occurs.
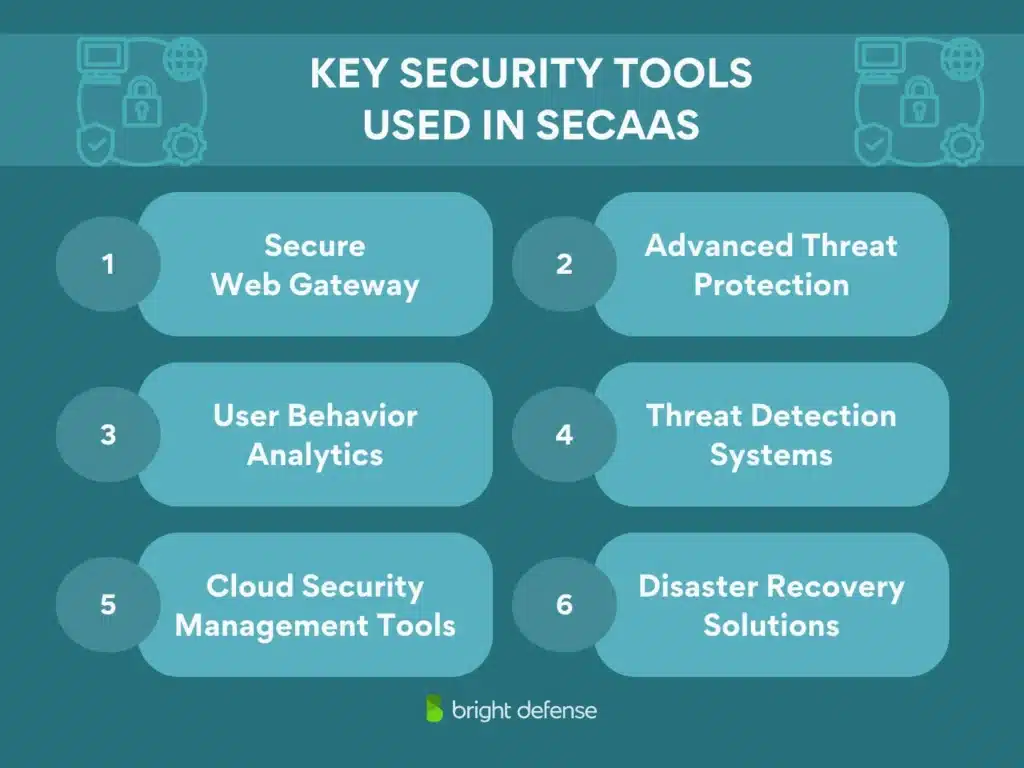
Key Security Tools Used in SECaaS
By combining a cloud-based model with cutting-edge security management, SECaaS offers businesses the flexibility and power to keep their environments safe from constantly evolving threats.
Here are some frequently used tools:
- Secure Web Gateway. Filters and monitors web traffic to block threats like malware and phishing.
- Advanced Threat Protection. Guards against sophisticated attacks, including zero-day exploits.
- User Behavior Analytics. Detects anomalies by analyzing patterns in employee activity.
- Threat Detection Systems. Monitors network activity for suspicious behaviors.
- Cloud Security Management Tools. Provides centralized control over cloud infrastructure and policies.
- Disaster Recovery Solutions. Helps restore systems and data after an incident
Who Needs Security as a Service?
Contrary to popular belief, Security as a Service isn’t just for large organizations with endless resources.
Managed Security Service Provider for Small Businesses
Small businesses often face tight budgets and limited IT expertise.
A managed security service provider offering SECaaS allows them to access tools like threat detection, data protection, and cloud-based security solutions without needing expensive hardware or full-time CISO specialists. It’s a practical way to keep your business secure while staying focused on growth.
But SECaaS doesn’t stop there. Big businesses can benefit just as much – if not more.
Integrated Security Services for Enterprises
Enterprises deal with larger networks, more data, and higher risks.
SECaaS helps simplify security management by connecting cloud services to their existing infrastructure, giving them access to features like user behavior analytics, advanced threat protection, and disaster recovery planning. These tools make it easier to manage threats while staying flexible and efficient.
No matter the size of your business, SECaaS provides the tools you need to stay ahead of cybersecurity risks in a way that fits your resources and goals.
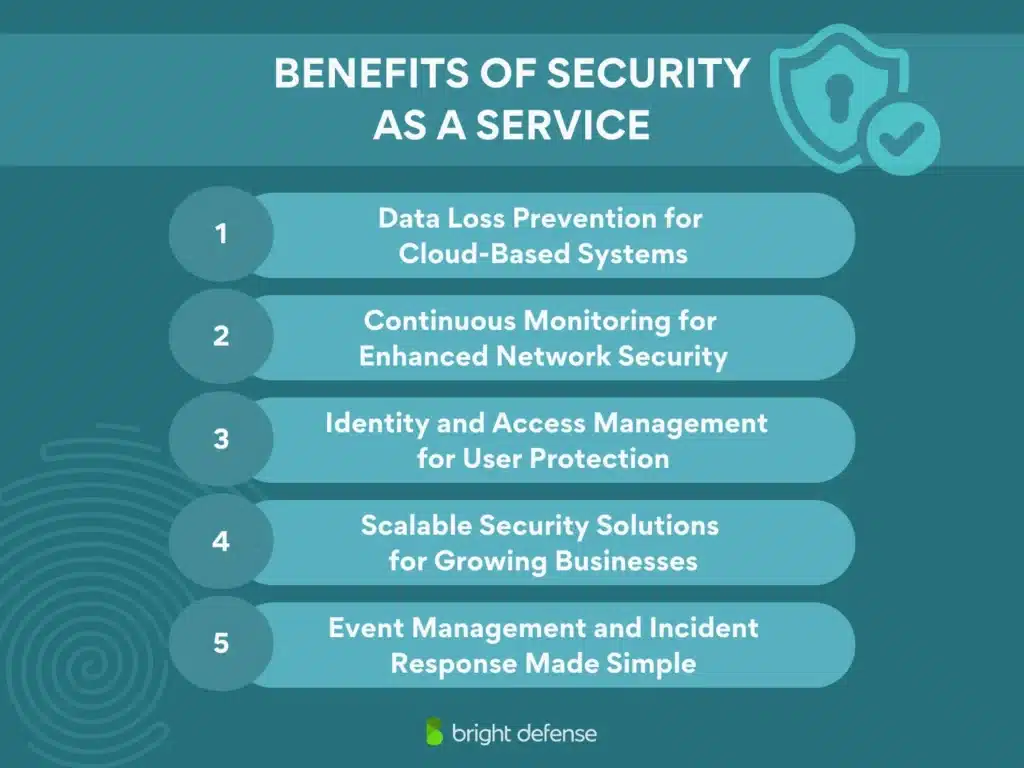
5 Benefits of Security as a Service
Security as a Service is a powerful way to enhance cybersecurity, reduce costs, and streamline operations. Here’s why SECaaS is becoming the go-to choice for organizations of all sizes.
1. Data Loss Prevention for Cloud-Based Systems
Data breaches are one of the biggest threats to businesses today, and losing sensitive information can have serious financial and reputational consequences.
SECaaS provides data loss prevention (DLP) solutions designed for cloud-based systems, helping businesses protect critical data and comply with frameworks like SOC 2, ISO 27001, and HIPAA.
- Real-time data monitoring. SECaaS tools track how data is accessed, shared, or stored, reducing the risk of accidental or malicious exposure.
- Cloud-friendly policies. DLP systems enforce rules tailored for cloud services, ensuring compliance while safeguarding sensitive files.
- Automated alerts. Get instant notifications about unusual data activity so you can address risks before they escalate.
2. Continuous Monitoring for Enhanced Network Security

Cyber threats don’t sleep, and neither should your security strategy.
The growing need for advanced security solutions is evident in market trends, with threat intelligence security services expected to register a CAGR of 9.5% from 2023 to 2030.
Continuous monitoring is a core feature of SECaaS, giving businesses 24/7 protection against vulnerabilities across their networks. This proactive approach helps you meet compliance requirements while reducing risk.
- Threat detection in real-time. SECaaS identifies suspicious activity, such as unauthorized access or malware attempts, as soon as they occur.
- Centralized dashboards. Monitor all aspects of your network security from one easy-to-use platform, streamlining compliance reporting.
- Preventive insights. Continuous monitoring detects weak spots in your systems, helping you strengthen defenses before attackers can exploit them.
3. Identity and Access Management for User Protection
Who has access to what? This question can make or break your security. That’s why identity and access management (IAM) tools protect your business. They control user access to sensitive systems and data – a requirement for compliance with frameworks like HIPAA and ISO 27001.
- Role-based access control. Assign permissions according to roles to restrict access to sensitive systems and block unauthorized actions.
- Multi-factor authentication (MFA). Require multiple verification methods for access to add an extra layer of security with multi-factor authentication (MFA).
- User behavior analytics. Monitor user activity to detect and block suspicious behavior, like unauthorized login attempts.
4. Scalable Security Solutions for Growing Businesses

As your business grows, so do your security needs. Even the industry itself is still growing. From 2014 to 2022, the outsourced security services market grew by 50%, from $22 billion to $33 billion.
This is proof of the rising demand for security solutions like SECaaS, which offers scalable solutions that adapt to your company’s expansion without requiring costly infrastructure upgrades. This flexibility is especially important for maintaining compliance as new users, systems, or markets are added.
- Flexible cloud infrastructure. Quickly add or remove services without investing in new hardware or hiring extra staff.
- Seamless onboarding. Integrate new users and systems into your security framework with minimal disruption to daily operations.
- Cost-efficient scalability. Only pay for the services you need, keeping costs manageable as your security requirements evolve.
5. Event Management and Incident Response Made Simple
When a cybersecurity event happens, the speed and effectiveness of your response can determine the outcome. SECaaS simplifies event management and incident response, helping businesses recover quickly while staying compliant with frameworks like SOC 2 and CMMC.
- Automated incident response. SECaaS platforms use pre-set protocols to contain and resolve threats in minutes, minimizing damage.
- Disaster recovery planning. Be prepared for worst-case scenarios with step-by-step recovery plans that protect your data and operations.
- Compliance-ready reporting. Event logs and post-incident reports are automatically generated, making it easy to prove compliance after a breach.
Challenges With Security as a Service
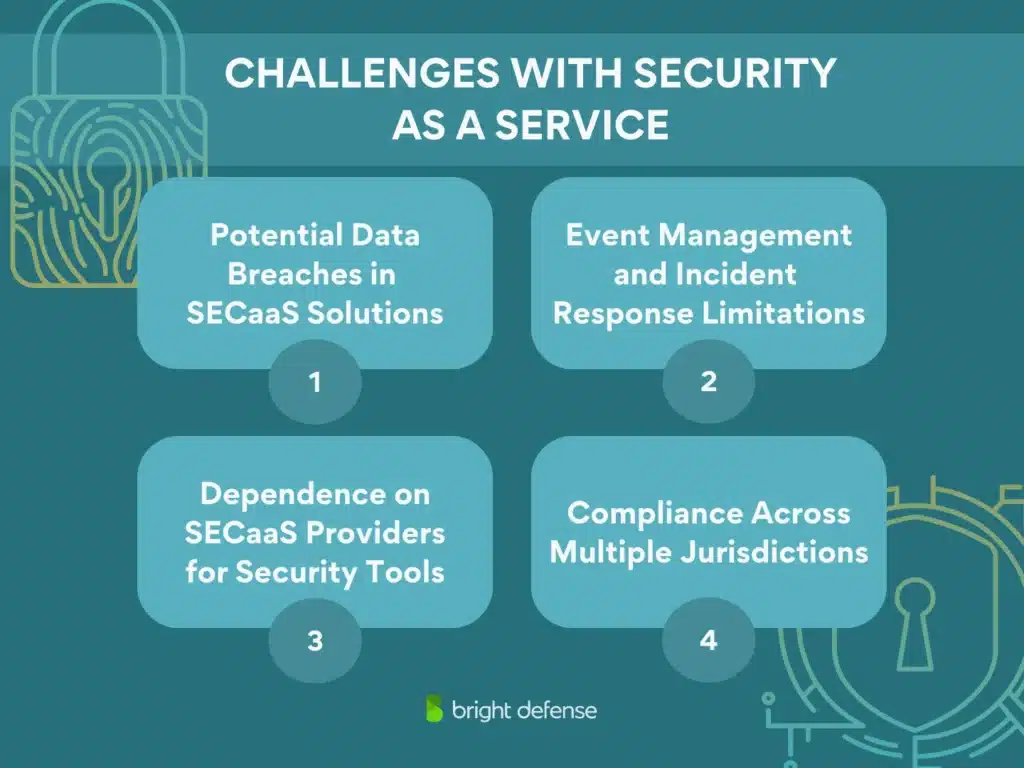
SECaaS is far from perfect. It solves many cybersecurity headaches, but it’s not without its own challenges. Businesses relying on cloud-based security solutions must weigh different risks with the benefits.
Here’s where SECaaS gets tricky – and how businesses can stay ahead.
Potential Data Breaches in SECaaS Solutions
Outsourcing security doesn’t eliminate the risk of data breaches.
In fact, SECaaS providers are high-value targets for attackers. So, you need to verify that your chosen provider has strong data loss prevention measures and clear protocols for handling advanced persistent threats.
- Visibility into provider security. Some providers don’t disclose how they secure their own systems. Ask about threat detection methods, incident response plans, and encryption standards before signing any agreement.
- Multi-tenant risks. Many SECaaS platforms host multiple clients on shared infrastructure, raising the risk of data leakage between accounts. Providers should prove they maintain strict isolation between tenants.
- Compliance exposure. A data breach could result in legal penalties if security logs, access records, or compliance documentation aren’t readily available. Businesses should confirm they’ll have full access to security data when needed.
Event Management and Incident Response Limitations
Quick response times are key in cybersecurity. While SECaaS providers offer event management tools, businesses still need to know how incidents will be handled, who takes responsibility, and how quickly threats are addressed.
- Service-level agreements (SLAs) matter. Some providers take hours—or even days—to respond to incidents. Businesses should negotiate SLAs that guarantee fast remediation times.
- Incident data access. Some providers limit how much security data customers can see, which can cause problems during audits or forensic investigations. Ask upfront about security assessment and forensic logging capabilities.
- Disaster recovery planning gaps. A provider outage shouldn’t put your entire business at risk. Look for SECaaS vendors that integrate disaster recovery planning into their services.
Dependence on SECaaS Providers for Security Tools
Handing off security functions to a third party makes sense for cost and efficiency, but it also introduces risks. Businesses must vet providers carefully to avoid vendor lock-in and unexpected disruptions.
- Limited customization. Many SECaaS platforms offer standardized security tools that may not fit a company’s specific needs. Before signing a contract, confirm if the provider allows custom security configurations.
- Vendor lock-in concerns. Switching SECaaS providers can be difficult, especially if they control access to cloud infrastructure, logs, or compliance records. Businesses should clarify exit strategies before committing.
- Provider downtime risks. A SECaaS provider going offline—whether due to a cyberattack or an internal failure—could leave your systems exposed. Ask how they handle redundancy and uptime guarantees.
Compliance Across Multiple Jurisdictions
One of the biggest compliance headaches with SECaaS is managing regulatory requirements in different regions. Cloud computing environments don’t always respect geographical boundaries, and some laws restrict where security data can be stored or processed.
- Data residency laws. Regulations like GDPR require that certain data remain within specific countries. Businesses using SECaaS must verify that their provider meets these storage requirements.
- Employee monitoring restrictions. Some regions, like the EU, have strict rules about tracking employee behavior. Businesses should check how user behavior analytics and other monitoring tools comply with regional laws.
- Cross-border legal conflicts. If a SECaaS provider operates in multiple jurisdictions, data access rules could vary. This could lead to complications if security logs or audit trails are needed for investigations.
Balancing the Risks With the Benefits
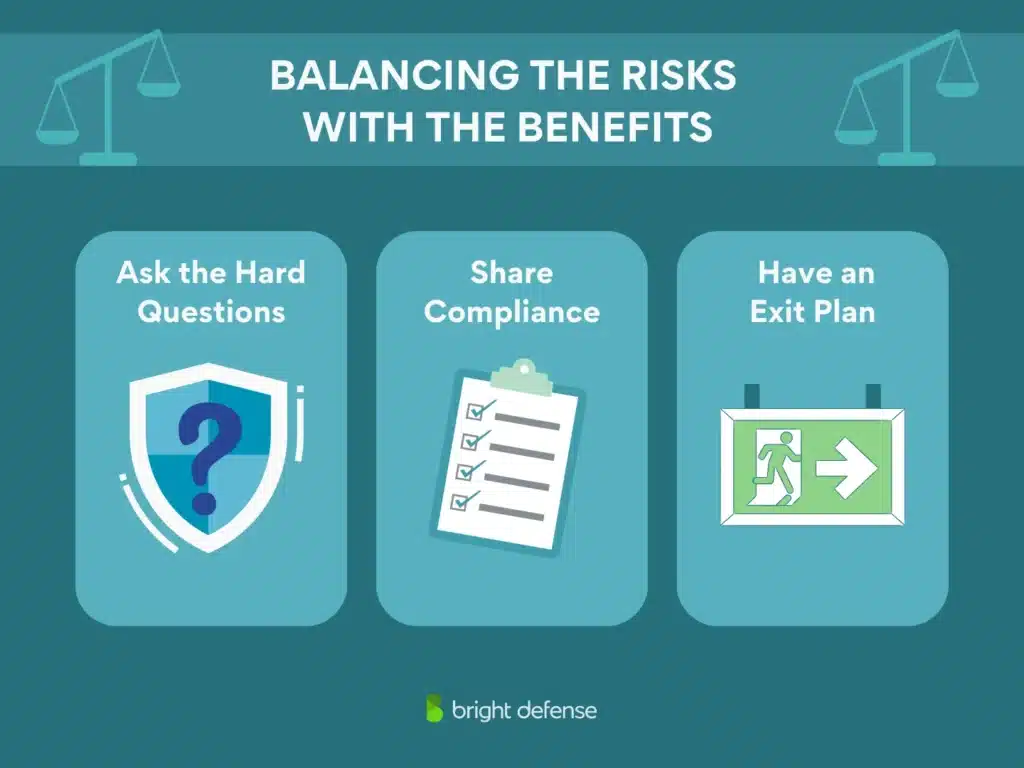
SECaaS isn’t a plug-and-play solution – it requires careful planning.
Businesses must treat their SECaaS provider as an extension of their own security team, holding them accountable for transparency, compliance, and security effectiveness.
- Ask the hard questions. Before signing a contract, demand visibility into security management, breach response plans, and compliance documentation.
- Treat compliance as a shared responsibility. While a SECaaS provider can help with security, businesses remain responsible for meeting industry regulations like SOC 2, ISO 27001, and HIPAA.
- Have an exit plan. Avoid vendor lock-in by ensuring you can retain access to logs, compliance records, and security tools if you need to switch providers.
With the right strategy, businesses can use SECaaS to strengthen security while staying compliant. But skipping the due diligence? That’s a risk no company should take.
12 Examples of Security as a Service Solutions
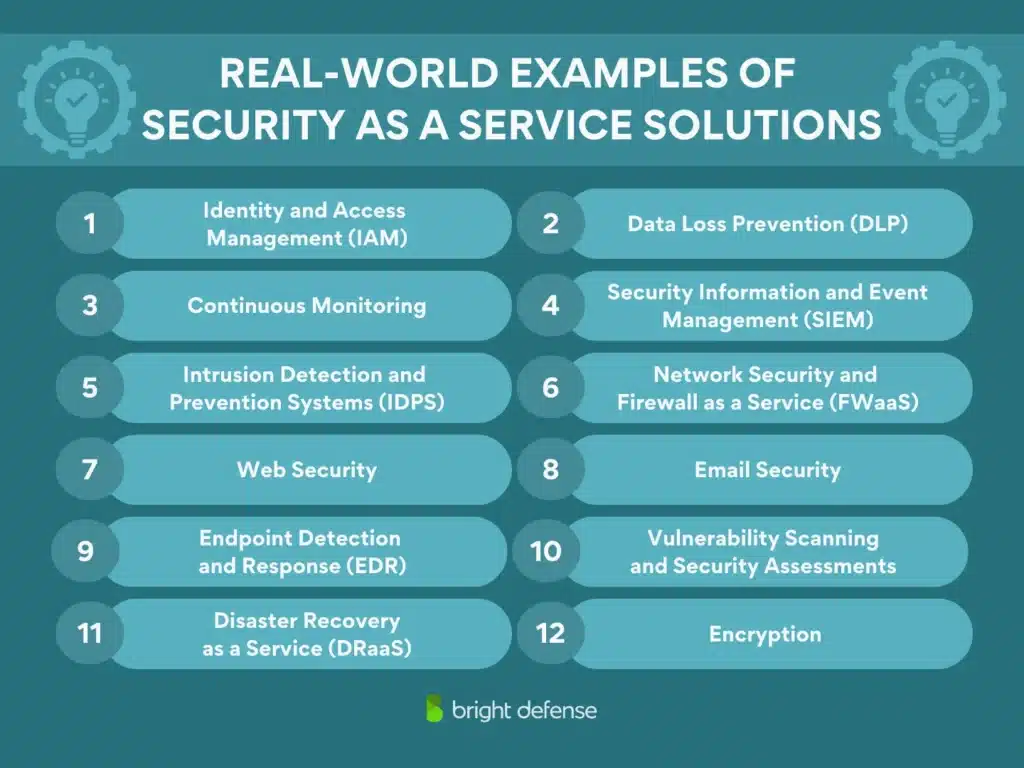
SECaaS isn’t just about theoretical security concepts. From preventing data leaks to securing cloud networks, SECaaS provides the tools and expertise needed to protect sensitive information and maintain compliance.
Here’s a look at the most commonly used SECaaS solutions and how they keep businesses secure.
- Identity and Access Management (IAM). Controlling who can access your systems is a foundational security measure. Identity and Access Management (IAM) solutions help businesses manage user permissions, enforce strong authentication, and reduce the risk of unauthorized access.
- Data Loss Prevention (DLP). Losing sensitive data – whether through a cyberattack, human error, or insider threat – can lead to compliance violations and financial losses. DLP solutions monitor and control data movement across your network, ensuring confidential information doesn’t end up in the wrong hands.
- Continuous Monitoring for Threat Detection. Cyber threats evolve daily. Continuous monitoring solutions scan networks 24/7 to detect advanced persistent threats, malware, and suspicious user activity before they escalate.
- Security Information and Event Management (SIEM). A SIEM platform collects and analyzes security data across an organization, helping detect and respond to threats faster. It’s a key tool for compliance, as it provides a full audit trail of security events.
- Intrusion Detection and Prevention Systems (IDPS). Businesses need real-time defense against cyberattacks. Intrusion Detection and Prevention Systems (IDPS) monitor network traffic for suspicious activity and take action to block threats.
- Network Security and Firewall as a Service (FWaaS). A firewall as a service (FWaaS) provides network security without requiring businesses to maintain on-premise hardware. These cloud-based solutions filter traffic, prevent intrusions, and secure connections.
- Web Security for Safe Internet Access. The internet is full of risks. Web security solutions protect users from malicious websites, phishing scams, and malware downloads.
- Email Security. Email is still the most common entry point for cyberattacks. Email security solutions protect businesses from phishing, spam, and malware.
- Endpoint Detection and Response (EDR). Endpoints – like employee laptops, desktops, and mobile devices – are frequent targets for cyberattacks. EDR solutions continuously monitor and respond to threats on these devices.
- Vulnerability Scanning and Security Assessments. Proactive security starts with identifying weak spots. Vulnerability scanning and security assessments help businesses find and fix security flaws before attackers exploit them.
- Disaster Recovery as a Service (DRaaS). A cyberattack, power outage, or natural disaster can disrupt business operations. Disaster recovery as a service (DRaaS) helps businesses recover quickly with minimal downtime.
- Encryption for Data Protection. Encryption scrambles data so only authorized users can read it. SECaaS solutions apply encryption to data at rest, in transit, and in use to prevent unauthorized access.
How to Choose the Right Security as a Service Provider
Not all SECaaS providers are created equal.
Some offer better response times, more advanced security tools, or stronger compliance support. Others might leave you dealing with hidden gaps, unreliable availability, or vendor lock-in.
To avoid these potential problems down the road, ask the right questions before choosing a provider.
Is the security team available 24/7?
A SECaaS provider should be more than just a software vendor – they need to be a real security partner. That’s the keyword right there: partner.
Automated processes are good, but if they rely too heavily on it or have limited human support, it could leave your business exposed when it matters most.
How fast do they respond to incidents?
Response time can mean the difference between a minor security event and a full-blown data breach.
Ask about their mean time to detect (MTTD) and mean time to respond (MTTR). A provider that takes too long to react could leave your data—and your compliance status—at risk.
What security tools and technologies do they use?
Your provider’s security stack matters. Ask what technologies they use for threat detection, intrusion prevention, and network security. Are their tools constantly updated to protect against advanced persistent threats?
The best SECaaS providers always stay ahead of the curve.
Do they offer disaster recovery and business continuity planning?
As much as we’d like to avoid them, cyberattacks, outages, and system failures do happen. A solid SECaaS provider should have a clear disaster recovery strategy in place to get you back online fast.
Also, they should be able to tailor their recovery plans based on your compliance needs (HIPAA, SOC 2, ISO 27001).
How scalable is their service?
Your business isn’t static, is it? A good SECaaS provider can scale security resources up or down based on your needs.
Make sure to ask how they handle onboarding new users, securing remote workforces, and integrating with existing infrastructure, too.
Do they have strong vendor partnerships?
A SECaaS provider is only as good as the security tools they use.
Do they work with industry leaders in firewalls, SIEM, intrusion detection, and encryption? Providers with strong partnerships tend to offer better security integrations and more reliable protection.
How do they handle compliance across multiple jurisdictions?
Regulatory requirements vary by industry and region. If your business operates across different locations, does the provider help you stay compliant with global data protection laws? Do they support automated compliance reporting?
Failing to meet these requirements could mean heavy fines and legal trouble.
Do they provide transparent reporting and visibility?
You can’t manage what you can’t see.
Some SECaaS providers limit access to security logs, real-time threat data, and compliance reports. It’s best to go with a provider that has a user-friendly dashboard to keep you informed.
Are they truly zero-trust?
Zero-trust security is slowly but surely becoming the new standard.
Some providers claim to offer zero-trust solutions but still rely on outdated security models. Ask if their network security and identity and access management solutions follow true zero-trust principles, requiring verification for every access request.
What happens if you need to switch providers?
Vendor lock-in is a real issue with SECaaS. If you decide to leave, can you take your security data and compliance records with you?
Your chosen provider should offer clear exit strategies so you don’t lose critical security data or get stuck with a service that no longer meets your needs.
Evaluating a SECaaS Provider’s Security Assessment Process

As mentioned above, the global SECaaS market is booming.
Sad to say, not all SECaaS providers are worth trusting. Some run half-baked security assessments that barely scratch the surface, while others go deep, identifying risks before they become disasters.
The truth is that there’s no trick to being the best SECaaS provider other than due diligence. They run continuous checks, fix vulnerabilities before attackers can exploit them, and give businesses full visibility into their security posture.
So, let’s talk about how to evaluate SECaaS services based on a study published on the International Journal of Science and Engineering Applications (IJSEA).
Risk Identification and Vulnerability Management
Security assessments should start with hard data, never assumptions. A provider that skips vulnerability scanning or runs it once a year isn’t serious about security.
91% of the study’s participants agreed that vulnerability management is a key factor in adopting SECaaS. Businesses need providers that scan for misconfigurations, weak encryption, and unpatched software every day – not just once a quarter.
Access Controls and Identity Verification
Identity and access management (IAM) isn’t optional. Weak access controls mean attackers can walk right in.
In the study, 89 out of 109 participants agreed that IAM is a must-have for SECaaS standardization. Providers should require multi-factor authentication (MFA), role-based access control (RBAC), and user behavior tracking.
Simply put, if a provider can’t detect when an employee suddenly logs in from five countries in one day, they’re not taking access security seriously.
Data Protection and Compliance Checks
Roughly 84% of the participants in the study said that DLP is essential for cloud security. And data loss prevention (DLP) is what keeps sensitive business information from getting leaked.
A good SECaaS provider should encrypt data at rest and in transit, block unauthorized file transfers, and log every attempt to access restricted information.
Compliance matters too – providers should safely support frameworks like HIPAA, SOC 2, and ISO 27001 without making businesses jump through hoops.

Incident Response and Disaster Recovery
Cyberattacks don’t wait for office hours, so why should SECaaS providers?
In the same study, email security was ranked lowest in participant agreement, with just 79%. This means some businesses still underestimate phishing risks.
Providers need real-time threat detection, automated incident response, and 24/7 monitoring. Disaster recovery isn’t just about backups – it’s about getting businesses running again in minutes, not days.
Transparent Reporting and Ongoing Improvement
Lastly, a SECaaS provider that hides security logs or gives vague compliance reports is a red flag. Clients should have full access to security events, monitoring dashboards, and system reports.
Security information and event management (SIEM) tools should track and correlate threats across the network. If a provider can’t explain how they improve security over time, they’re merely reacting, and that could be too late.
Why You Should Partner With Bright Defense
Cybersecurity isn’t just about blocking threats – it’s about staying compliant, reducing risk, and keeping your business audit-ready at all times.
Here at Bright Defense, we specialize in continuous cybersecurity compliance, offering expert-driven security solutions tailored to frameworks like SOC 2, ISO 27001, HIPAA, PCI DSS, and GDPR. Our CISSP and CISA-certified experts create custom plans to strengthen your security posture and streamline compliance.
Continuous Monitoring and Incident Response
Like we said above, security threats wait for no one.
Our monthly services include risk assessments, business continuity planning, and policy implementation to proactively manage threats.
Also, our managed compliance automation platform helps businesses monitor compliance across multiple frameworks in real time, eliminating manual effort and reducing the risk of non-compliance.
Security Awareness and Human Risk Reduction
Employees can be a business’s biggest vulnerability. That’s why Bright Defense partners with KnowBe4 to deliver managed security awareness and phishing training.
Remember, human error is behind 95% of data breaches, so it’s important to reduce this risk through security awareness training – especially if you’re a small business.
Expert vCISO Services for Strategic Guidance
Need high-level cybersecurity strategy without a full-time team?
Most businesses juggle too many security tools that don’t talk to each other. Bright Defense’s virtual Chief Information Security Officer (vCISO) services provide expert leadership to oversee your security strategy and guide you through evolving threats and regulations.
Automated & Integrated Compliance Solutions
Our compliance-first approach integrates security processes into a single, easy-to-manage system.
Bright Defense solutions align with top industry frameworks like NIST CSF and COBIT. We help you meet your business objectives while staying ahead of regulatory changes.
Bright Defense for Your Cloud Security Compliance Needs
Bright Defense doesn’t just help you with your security – we make compliance simple.
Whether you’re an MSP, SaaS provider, or growing business, Bright Defense offers enterprise-grade security and compliance without the costs of building an in-house team.
With automation, expert support, and continuous compliance monitoring, we keep your business secure, compliant, and audit-ready – every single day!
So, what are you waiting for? Reach out to Bright Defense today!
Security as a Service FAQs
1. How Does a SECaaS Provider Manage Data Breaches?
They monitor for suspicious activity 24/7, isolate breaches to prevent spread, and deploy remediation strategies. Providers also generate detailed reports to meet compliance requirements.
2. What Security Assessment Tools Are Used in SECaaS?
Common tools include vulnerability scanners, penetration testing platforms, and SIEM systems. These tools help identify weak points and monitor security events in real time.
3. How Does Continuous Monitoring Help Prevent Threats?
It catches threats as they happen – before they cause damage. By analyzing network traffic and user behavior continuously, SECaaS reduces response times and strengthens overall security.
4. What Is the Role of Identity and Access Management in SECaaS?
IAM restricts access to sensitive systems, reducing the risk of unauthorized entry. Features like multi-factor authentication (MFA) and role-based access control (RBAC) keep data secure and compliant.
5. How Do Managed Security Service Providers Differ From SECaaS?
MSSPs provide broad IT security services, while SECaaS focuses on cloud-delivered security solutions like DLP, IAM, and continuous threat detection. SECaaS also emphasizes compliance automation.
6. Are Web Security Solutions Included in Most SECaaS Packages?
Yes, web security features are common and include secure web gateways, anti-phishing protection, and traffic filtering to protect against online threats.
Get In Touch



