
Tamzid Ahmed | Security and Compliance Writer
April 11, 2025
Cybersecurity vs Network Security – 12 Key Differences
Cybersecurity and network security often get tossed around like they mean the same thing, but they don’t. Sure, both aim to protect systems and data, but the scope, tools, and focus areas are very different.
In this blog, we break down 12 key differences that separate the two, so you know exactly where each one fits and why both are critical right now.
What is Cybersecurity?
Cybersecurity is the practice of protecting computer networks, servers, and digital systems from cyber threats such as malicious software, unauthorized access, and data breaches. It makes sure that the security infrastructure remains intact so systems run smoothly without being compromised. Whether for individuals or enterprises, cyber and network security is now essential, not optional.
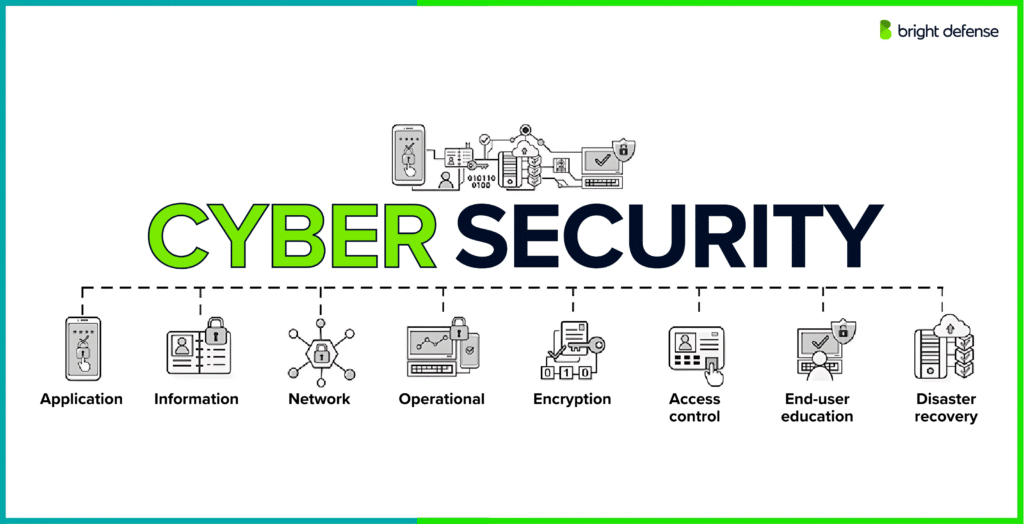
The field involves a mix of security measures, tools, and strategies that defend against a range of security threats, including:
- Malware (viruses, ransomware, spyware)
- Phishing scams
- Data breaches
- DDoS attacks
- Insider threats
The scope ranges from simple antivirus software and strong passwords to large-scale cloud services and hardened network infrastructure. A cyber security professional must constantly update defenses to counter evolving threats, especially those posed by advanced persistent threats and internal threats.
Whether you’re guarding your private photos or securing corporate data integrity, protecting networks and information is at the heart of cyber security focuses. This is the line of defense between your data and the bad guys trying to gain access to it.
What is Network Security?
Network security is the practice of protecting computer networks from unauthorized access, cyber threats, and security breaches. It involves using hardware, software, and security measures to safeguard sensitive data and maintain data integrity.
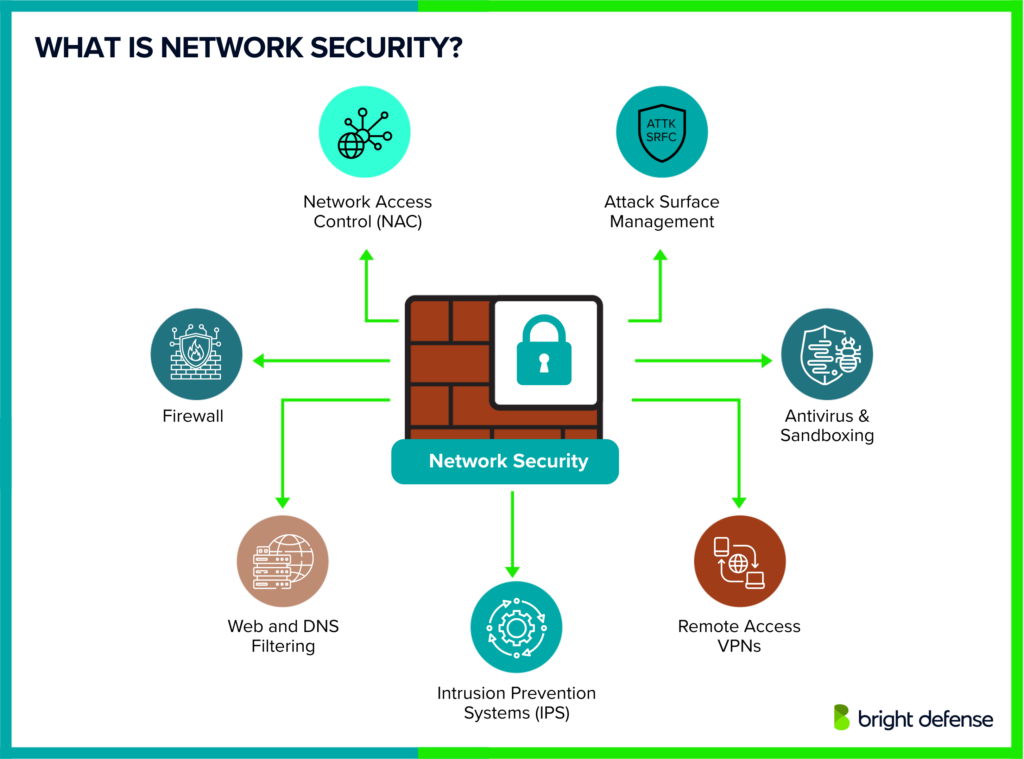
This includes setting up intrusion detection systems, access controls, firewalls, and data encryption to block malicious software and reduce network vulnerabilities. Focusing on both internal threats and external threats, network security focuses on keeping systems secure and operations uninterrupted.
Cybersecurity vs. Network Security: In-Depth Comparison Table
| Aspect | Cybersecurity | Network Security |
| 1. Definition | Protects entire digital systems including networks, endpoints, applications, cloud environments, and data from cyber threats | Secures the networking infrastructure, ensuring safe transmission of data across routers, switches, and access points |
| 2. Scope | Broad coverage across the entire digital landscape. Includes user devices, software, operating systems, and internet-facing systems | Focused on protecting the physical and virtual pathways data travels through. Limited to network-related assets |
| 3. Primary Focus | Safeguards data, devices, apps, and user activities from exploitation or unauthorized access | Secures network hardware and data in motion, preventing breaches through network-based vulnerabilities |
| 4. Hierarchy | A subset of Information Security focused exclusively on digital (cyber) assets and threats | A subset of Cybersecurity concerned specifically with network-level defense |
| 5. Data Protection | Secures data at rest stored in databases, servers, cloud platforms, and user devices | Protects data in transit as it flows across networks internally and externally |
| 6. Attack Vectors | Malware, phishing, ransomware, SQL injection, DNS tunneling, zero-day exploits, social engineering | Denial-of-service (DoS/DDoS), man-in-the-middle attacks, spoofing, ARP poisoning, unauthorized access |
| 7. Tools and Technologies | Antivirus software, encryption tools, EDR, SIEM, IAM systems, AI-based threat detection, cloud workload protection | Firewalls, VPNs, intrusion detection and prevention systems (IDS/IPS), access control lists, VLANs, NAC |
| 8. Threat Sources | Both external and internal: hackers, rogue insiders, social engineers, malicious code | Primarily external threats and misconfigurations affecting connectivity and access control |
| 9. Security Approach | Includes preventive, detective, and corrective measures across all endpoints and applications | Primarily preventive and detective, designed to block and alert on unauthorized access attempts |
| 10. Responsibilities | Protect system-wide architecture, enforce compliance (HIPAA, GDPR, PCI), monitor user activity and data handling | Maintain secure network architecture, monitor traffic, control device access, respond to network incidents |
| 11. Roles and Job Titles | Cybersecurity Analyst, Cybersecurity Architect, SOC Analyst, Incident Responder, Threat Intelligence Specialist | Network Security Engineer, Network Architect, Firewall Administrator, Network Security Analyst |
| 12. End Goal | Maintain confidentiality, integrity, and availability of all digital assets both on-premise and in the cloud | Ensure secure and uninterrupted data flow, and protect the infrastructure that supports digital operations |
Key Differences between Cybersecurity and Network Security
Network security protects the systems that connect your devices—like routers, switches, firewalls, and virtual private networks. It keeps sensitive data safe as it moves through computer networks, using access controls, intrusion detection, and network segmentation to stop attacks like DDoS, man-in-the-middle, sniffing, and malicious software. In short, it defends the network’s entry points and makes sure only the right people get through.
Cybersecurity, on the other hand, is the full package. It includes network security but also covers endpoints, applications, cloud systems, and user behavior. It defends against cyber threats like phishing, ransomware, insider threats, and zero-day attacks—protecting digital assets no matter where they are. If network security locks the doors, cybersecurity protects the whole house.
Let’s check out the differences between cybersecurity and networks in a more detailed manner:
1. The Core Objective of Each Approach
Cybersecurity is built to block data breaches, prevent system exploitation, and stop unauthorized access across all devices and services. Network security is designed to prevent breaches through network-based entry points like open ports or unsecured protocols.
2. Where They Fit in the Bigger Picture of Information Security
Cybersecurity is a branch of information security that focuses exclusively on digital assets and threats. Network security is a more specific slice of cybersecurity, concerned only with the integrity of network communication.
3. What Kind of Data Each One Protects
Cybersecurity safeguards data at rest, such as stored files, cloud backups, and local databases. Network security is responsible for data in transit, making sure it gets from one place to another without being intercepted or tampered with.
4. The Types of Threats They Are Designed to Handle
Cybersecurity handles broad, often complex threats: malware, ransomware, phishing, zero-day exploits, and social engineering. Network security fights off threats tied to the network itself—like DDoS attacks, spoofing, ARP poisoning, and unauthorized logins.
5. The Tools and Systems Used in Each Area
Cybersecurity relies on software-based tools: encryption programs, EDR, SIEM systems, threat detection, and identity and access management (IAM). Network security uses hardware-level defenses: firewalls, VPNs, IDS/IPS, VLANs, and NAC.
6. Where the Threats Come From
Cybersecurity tackles both internal and external threats—from hackers to careless employees. Network security focuses mainly on external risks and configuration errors that could let attackers into the system.
Differences in Cybersecurity and Network Security Job Roles
There’s a lot of overlap between cybersecurity and network security, but the job roles are distinct. Here’s how the responsibilities typically break down:
Cybersecurity Analyst
Cybersecurity analysts are frontline defenders of an organization’s digital assets. They protect against cyber threats by simulating cyber attacks, identifying network vulnerabilities, and enforcing security policies that reduce unauthorized access and ensure secure practices across the board.
Core responsibilities:
- Monitoring computer networks for security breaches, suspicious behavior, and intrusion detection
- Installing and managing firewalls, antivirus software, encryption tools, and virtual private networks
- Running vulnerability assessments and penetration tests to expose and exploit network vulnerabilities in a controlled setting
- Creating and updating security measures based on emerging threats and trends
- Preparing detailed reports, documenting security incidents, and supporting post-breach recovery
Network Security Engineer
Network security engineers are the architects and maintainers of a company’s network security architecture. They secure the core network infrastructure, ensuring that network devices like routers, switches, VPNs, and firewalls are hardened against potential threats.
Core responsibilities:
- Identifying and patching network vulnerabilities across systems and devices
- Deploying and maintaining security infrastructure, including intrusion detection systems and access controls
- Documenting network security-defined protocols and establishing security standards
- Monitoring traffic for anomalies and signs of internal threats or external threats
- Managing vendor tools and solutions for cloud services, data encryption, and system defense
What Is the CIA Triad in Cybersecurity vs Network Security?
In the context of cybersecurity vs network security, the CIA Triad—Confidentiality, Integrity, and Availability—is the shared foundation that guides how professionals protect data, systems, and digital assets from cyber threats and security incidents. Both cybersecurity and network security use this model to build defenses that work across different layers of infrastructure.
1. Confidentiality
In network security, confidentiality means protecting computer networks and network infrastructure from unauthorized access. This involves access controls, virtual private networks, data encryption, and network segmentation.
In cybersecurity, confidentiality goes further. It covers endpoints, cloud services, and user identities, guarding sensitive information from internal threats, external threats, and advanced persistent threats.
2. Integrity
Network security ensures the accuracy of data as it moves across network devices by using firewalls, intrusion detection systems, and hardened security infrastructure.
Cybersecurity enforces data integrity more broadly, protecting databases, applications, and connected devices from malicious software, phishing attacks, and unauthorized tampering.
3. Availability
Network security maintains availability by blocking DDoS attacks, monitoring for network vulnerabilities, and ensuring system uptime so authorized users can gain access to services.
Cybersecurity extends this principle to all systems, keeping cloud services, digital assets, and user-facing tools online and functional during cyber attacks and unexpected outages.
FAQs
No, they are not the same. Network security is just one part of cybersecurity. It focuses on protecting the infrastructure that connects devices, like firewalls, routers, and VPNs. Cybersecurity is a broader term that includes network security but also covers applications, data, devices, and users against threats like malware, phishing, and insider attacks.
Cybersecurity pays more. The average salary for a cybersecurity engineer in the US is around $122,890 per year, with most earning between $102,000 and $142,000. Top earners can hit $162,500 or more. In comparison, network engineers average around $103,203 annually. While both fields pay well, cybersecurity typically offers a higher ceiling.
It depends on your career goals. Cybersecurity covers more ground, changes fast, and comes with high demand but also more pressure. Networking is focused on infrastructure and offers a steady career path. If you like solving new challenges every day, cybersecurity fits. If you prefer stability and system-level understanding, networking is a good pick.
A network security specialist focuses on securing the network—monitoring traffic, managing firewalls, and ensuring safe communication. A cybersecurity specialist takes care of the bigger picture, securing everything from apps and data to users and devices. Cybersecurity includes network security as just one part of a wider defense strategy.
Final Thoughts
Cybersecurity and network security aren’t interchangeable, they serve different roles in the fight against digital threats. Network security locks down the infrastructure, keeping unauthorized users out. Cybersecurity goes further, protecting everything from data and devices to apps and users across an entire digital ecosystem. If you’re serious about protecting sensitive information and keeping systems secure, you need both. It’s not about choosing one over the other, it’s about understanding how they work together to defend against today’s evolving threats.
Get In Touch



