Tim Mektrakarn
August 25, 2024
CMMC Readiness Guide
In today’s digital age, cybersecurity is not just a technical requirement. It’s a competitive advantage. This has never been truer for businesses in the Defense Industrial Base (DIB). The Cybersecurity Maturity Model Certification (CMMC) is a testament to this shift, ensuring contractors have the necessary cyber hygiene to protect our nation’s sensitive data. CMMC readiness is critical for ensuring you meet the requirements for future contracts.
You’ll likely be ahead of the curve if you work as a prime DoD Contractor. This article is geared towards sub-contractors (subs), many new to CMMC. Join us as we help get your organization ready for CMMC!
Brief Overview of CMMC (Cybersecurity Maturity Model Certification)
The Cybersecurity Maturity Model Certification or CMMC is undergoing a change commonly referred to as CMMC 2.0, which will have a stringent effective date in 2025. CMMC 2.0 consolidates the 5 levels of CMMC 1.0 into just 3 levels, all based on NIST 800-171 and NIST 800-172 requirements for protecting Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
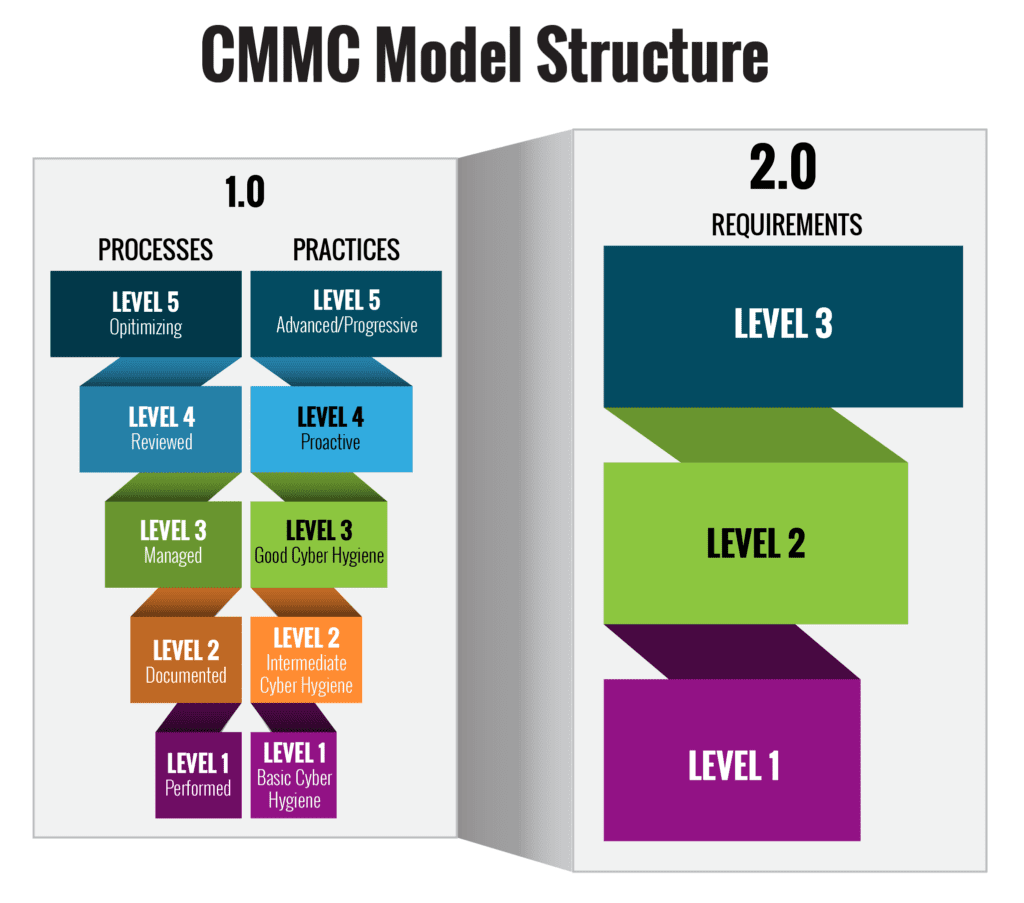
| CMMC 1.0 | CMMC 2.0 |
| • 5 increasingly progressive levels from Basic to Advanced • Levels 2 and 4 intended as transition stages between Levels 1, 3, and 5 | • 3 increasingly progressive levels: ◦ Level 1 (same as previous level 1) ◦ Level 2 (previous level 3) ◦ Level 3 (previous level |
Importance of CMMC for DoD contractors and the Defense Industrial Base (DIB)
With over 300,000 organizations in the Defense Industrial Base (DIB), there is concern by the government to protect the entire Defense Supply Chain (DSC). Adversaries target all DSC levels to ascertain information on the government’s defense initiatives. CMMC is a critical tool to help secure our nation’s secrets. Having a more mature security program also helps protect your organization from the financial and repetitional risks of a cyberattack.
Since May 2016, all Federal contractors had to comply with Federal Acquisition Regulation (FAR) 52.204-21, which outlines 17 best practices and 15 requirements that all contractors must adhere to to protect FCI.
For example, the Dongfeng EQ2050 is a near clone of the Humvee.

The Chinese Shenyang J-31 Gyrfalcon (top) has a high resemblance to the the Lockheed Martine F-35 Lightning.

Understanding CMMC 2.0 Levels
Although the CMMC 2.0 framework has not been completely ratified, here are the basics. CMMC 2.0 consolidates the original five levels of the CMMC framework into three levels. This change aims to reduce the complexity and cost of compliance for contractors, especially small and medium-sized businesses. The new structure still focuses on protecting Controlled Unclassified Information (CUI) and Federal Contract Information (FCI), but it offers a more streamlined approach to achieving compliance.
2. CMMC 2.0 Levels:
- Level 1 – Foundational: This level focuses on basic cybersecurity practices, ensuring contractors have foundational cyber hygiene. It’s designed to protect FCI, information not intended for public release. The practices at this level are equivalent to the cybersecurity best practices specified in FAR 52.204-21.
- Level 2 – Advanced: At this level, contractors must implement advanced cybersecurity practices to protect CUI. CUI is sensitive information that requires enhanced protection. The practices and processes at Level 2 align with the security requirements of NIST SP 800-171, ensuring contractors have a robust cybersecurity framework.
- Level 3 – Expert: This level is designed for a subset of the DIB that handles critical defense information or performs specific critical functions for the DoD. It introduces additional practices and processes beyond NIST SP 800-171 and 800-172 to counter advanced persistent threats (APTs). Achieving this level signifies that a contractor has expert-level cybersecurity practices in place.
Note: We will focus the discussion of this article on CMMC 2.0 Levels 1 and 2.
Importance of CMMC Readiness
Non-compliance with CMMC Level 1 and 2 poses significant risks for contractors within the Defense Industrial Base (DIB). Firstly, without adherence to Level 1’s foundational cyber hygiene practices, contractors risk exposing Federal Contract Information (FCI) to potential breaches, leading to data loss, reputational damage, and potential financial penalties. As Level 2 focuses on advanced cybersecurity measures to protect Controlled Unclassified Information (CUI), non-compliance at this level can result in more severe data breaches involving sensitive defense-related information. This jeopardizes national security and places the contractor at risk of losing current and future contracts with the Department of Defense (DoD).
Furthermore, non-compliant contractors may face legal repercussions and increased scrutiny, potentially losing trust and credibility in the defense marketplace. In essence, failing to meet CMMC Level 1 and 2 standards can have dire consequences for contractors, both in terms of business opportunities and in safeguarding critical information.
Recently, legal precedent has been set in the case of Aerojet Rocketdyne, who settled a $9M claim against the US Government for making false claims on their cyber attestation. Under the False Claims Act, any false claim may result in fines up to three times the program’s loss plus $11,000 per claim filed. These steep penalties will be disastrous for Small and Medium-sized businesses working in the DIB. This is one of the reasons why SMBs need to perform CMMC Readiness assessments. Read more about the case here.
Steps to Achieve CMMC Readiness
Step 1: Understand CMMC Level 1 Requirements:
At Bright Defense, we focus our CMMC readiness audits on evaluating current cybersecurity practices, identifying gaps in compliance, and remediating the gaps until all controls are fully met. We then test the controls continuously to ensure year-round compliance. To get started with CMMC Readiness, organizations should understand the 15 basic safeguarding requirements of FAR 52.204-21 and the 17 CMMC practices required for CMMC Level 1 compliance.
FAR 52.204-21 outlines the basic safeguarding requirements for protecting Federal Contract Information (FCI) in contractor information systems. Here’s a summarized list of the 17 CMMC practices for basic safeguarding.
17 CMMC Best Practices
- Limit Information System Access: Only authorized users can access the system.
- Authenticate Users: Verify the identity of users, processes, or devices before allowing access.
- Sanitize or Destroy Information System Media: Ensure that data is irretrievably deleted before disposal or reuse.
- Monitor and Control Communications: Control information transfers between the system and external systems or networks.
- Limit Physical Access: Restrict authorized individuals’ physical access to information systems, equipment, and operating environments.
- Escort Visitors: Monitor and escort visitors to areas where information systems operate.
- Maintain Audit Logs: Review system activity records, including network usage and user actions.
- Use Session Locks: Implement session locks for system sessions after a defined period of inactivity.
- Regularly Update System: Periodically update system, components, software, and firmware.
- Configure System Properly: Ensure the system is protected from malicious code at appropriate locations.
- Protect and Monitor Boundaries: Monitor and control communications at the system’s external and key internal boundaries.
- Use Strong and Unique Identifiers: Employ strong, unique identifiers for system users.
- Authenticate or Verify Identities: Authenticate the identity of those who receive system information.
- Protect FCI from Public Release: Prevent unauthorized public disclosure of FCI.
- Quickly Report Incidents: Report any security incidents, including potential threats, to the appropriate authorities.
- Use Strong Identifiers: Employ strong, unique identifiers for system users.
- Report Incidents: Report any security incidents to the appropriate authorities on time.
These requirements provide a foundational level of security to safeguard Federal Contract Information within contractor information systems, ensuring that sensitive data remains protected from potential threats.
Step 2: Prepare your Employees

With any cybersecurity program implementation, it’s important that the owners, board of directors, and executive leaders are fully bought into and championing the program for success. Employees are the biggest risk when it comes to cybersecurity. It is crucial that employees follow regular and consistent Cybersecurity Awareness Training along with understanding what CMMC is, why they should care, and how to follow the new policies and procedures that will be implemented for the organization to meet compliance. Be sure to provide employees with additional resources or point them in the right direction if they want to learn more beyond your training.
Step 3: Documentation and Policies

Documentation and policies play a pivotal role in CMMC readiness. They are the backbone of an organization’s cybersecurity posture, providing a clear roadmap for implementing, maintaining, and improving security practices. Well-documented policies ensure a standardized approach to security, reducing ambiguities and inconsistencies in executing practices. They offer a reference point for training, audits, and assessments, making demonstrating compliance during CMMC evaluations easier. Furthermore, in the event of personnel changes or system upgrades, robust documentation ensures continuity, allowing new team members or systems to align seamlessly with established security protocols.
In essence, while technical measures are crucial for cybersecurity, the documentation and policies ensure these measures are consistently and effectively applied across the organization, solidifying its CMMC readiness. A determination statement must be linked to each objective to ensure the documentation is updated and applies to the correct policy. Policies must be reviewed annually and sent to all employees for acknowledgment.
Step 4: Seeking External Assistance

Seeking External Assistance in the journey toward CMMC readiness can be a game-changer for many organizations. As the cybersecurity landscape evolves, achieving and maintaining compliance can be daunting. Recognizing when to bring in a consultant or external expert is crucial. These professionals offer specialized knowledge, providing insights into best practices, potential vulnerabilities, and tailored solutions that might be overlooked internally. They can help navigate the CMMC framework’s intricacies, ensuring every stone is turned on. Moreover, third-party assessments objectively evaluate an organization’s cybersecurity posture. Such assessments validate the organization’s efforts and identify areas of improvement, ensuring a comprehensive approach to CMMC readiness. While internal efforts lay the foundation, seeking external assistance brings in the expertise and objectivity needed to elevate an organization’s cybersecurity measures to the standards demanded by the CMMC.
If you are interested in exploring further, contact Bright Defense today.
Step 5: Implementing Required Practices
When planning for the implementation of the 17 CMMC Readiness Best Practices, it’s important to consider the following:
1. Access Control and User Authentication:
Central to cybersecurity is ensuring that only authorized individuals have access to your systems. This means setting up robust user authentication protocols. Organizations can significantly reduce the risk of unauthorized access by employing strong, unique identifiers for each user and verifying the identity of users or devices before granting access. Regularly reviewing and updating access permissions ensures that only those who need access have it, and no more than that.
2. Physical Security Measures:
While digital threats are a significant concern, physical security is equally crucial. Limiting physical access to system equipment and operational environments is fundamental. This might involve secure access mechanisms like key cards, biometric access controls, or security personnel. Monitor visitors and escort them in sensitive areas to prevent inadvertent or deliberate physical breaches.
3. System Maintenance and Protection:
Regularly updating systems, components, software, and firmware is essential to protect against vulnerabilities. Staying updated as cyber threats evolve ensures your protection against known threats. Furthermore, proactive measures, such as implementing safeguards against malicious code and using session locks after periods of inactivity, can prevent potential breaches.
4. Monitoring and Reporting:
Maintaining audit logs clearly records system activity. These logs can be invaluable in identifying suspicious activities or in forensic analysis after a security incident. Moreover, having a protocol for reporting security incidents ensures timely response and mitigation, minimizing potential damage.
5. Data Handling and Disposal:
To protect FCI from unauthorized public disclosure, remain vigilant not only in how you access and use data but also in how you dispose of it. Properly sanitizing or destroying information system media ensures that sensitive data doesn’t fall into the wrong hands even at the end of its lifecycle.
Step 6: Preparing for the CMMC Audit

Streamlined Assessments: One of the significant changes in CMMC 2.0 is the introduction of self-assessments for Levels 1 and 2, allowing contractors to self-certify their compliance. However, these self-assessments are subject to random audits by the CMMC Accreditation Body. Level 3 will still require a third-party assessment by C3PAOs to ensure the highest cybersecurity standards.
Preparing for a CMMC Level 1 audit requires a strategic blend of self-assessment, documentation, and proactive measures. At this foundational level, the focus is on ensuring basic cyber hygiene practices are in place to protect Federal Contract Information (FCI). Organizations should begin by conducting a thorough self-assessment to identify gaps in their cybersecurity practices relative to the 17 requirements of Level 1.
Document every security measure, protocol, and procedure meticulously, providing auditors with a clear trail of evidence, as the documentation process is equally crucial. This demonstrates compliance and showcases the organization’s commitment to maintaining a consistent security posture. Additionally, engaging in mock audits or seeking guidance from external experts can be beneficial, offering a fresh perspective and highlighting potential areas of concern. To prepare for a CMMC Level 1 audit, ensure that foundational cybersecurity practices are implemented but also verifiable, consistent, and well-documented.
Step 7: Continuous Monitoring

It is vital that organizations take a continuous monitoring approach towards CMMC Readiness. While the program’s point is to protect FCI and CUI, it’s also vital to improving the organization’s cybersecurity posture. Bright Defense offers ongoing continuous compliance services for CMMC Levels 1 and 2.
About Bright Defense:
Discover the path to CMMC compliance with Bright Defense’s CMMC readiness services. Bright Defense protects our clients from cybersecurity threats through continuous compliance. As the cybersecurity landscape becomes increasingly intricate, our team of CISSP and CISA-certified experts is here to guide you every step of the way.
From comprehensive assessments to documentation support, we ensure that your organization is prepared and primed for success in the CMMC audit. With Bright Defense by your side, you’re not just achieving compliance. You are showcasing your unwavering commitment to cybersecurity excellence. Elevate your defense contracting game and secure your future with Bright Defense’s unparalleled CMMC readiness expertise.
Get started with Bright Defense today!
Contact Us
Facebook
Twitter
Youtube
[crmperks-forms id=5]
Get In Touch



