Tim Mektrakarn
February 20, 2025
NIST vs CIS: Which Cybersecurity Framework Is Right for MSP Compliance?
Introduction NIST vs CIS
Cybersecurity frameworks are like roadmaps that guide us toward better protecting our data and systems. However, choosing between NIST vs CIS can feel like deciding between two equally beneficial plans, each with its own strengths. Let’s take a closer look at NIST CSF vs CIS Controls, explore how you can implement them, and figure out which might be best for your specific needs.
Understanding NIST CSF vs CIS Controls
When discussing NIST vs CIS, it’s important to note that we’re actually talking about two different tools:
- NIST CSF (Cybersecurity Framework)
- High-level and flexible.
- Built around five core functions: Identify, Protect, Detect, Respond, and Recover.
- Often used for compliance with regulations like HIPAA, PCI-DSS, and GDPR.
- CIS Controls (Critical Security Controls)
- Prescriptive and technical.
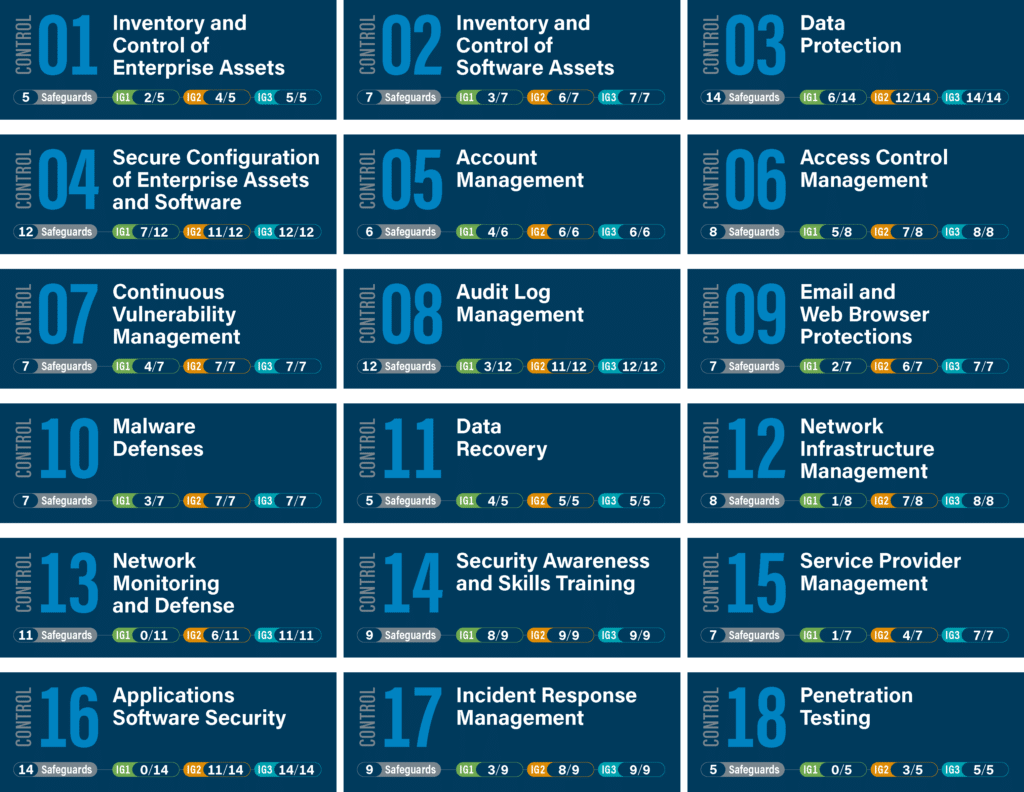
- Prioritized set of security actions (currently 18) that organizations can implement in stages, known as Implementation Groups (IG1, IG2, IG3).
- Strongly focused on practical, day-to-day security tasks.
In the NIST CSF vs CIS Controls comparison, NIST CSF leans toward strategic risk management, while CIS Controls excel at actionable security measures.
Diving Deeper: Implementing NIST CSF
If you’re evaluating NIST vs CIS and decide to go with NIST CSF, here’s a quick rundown on how to implement it:
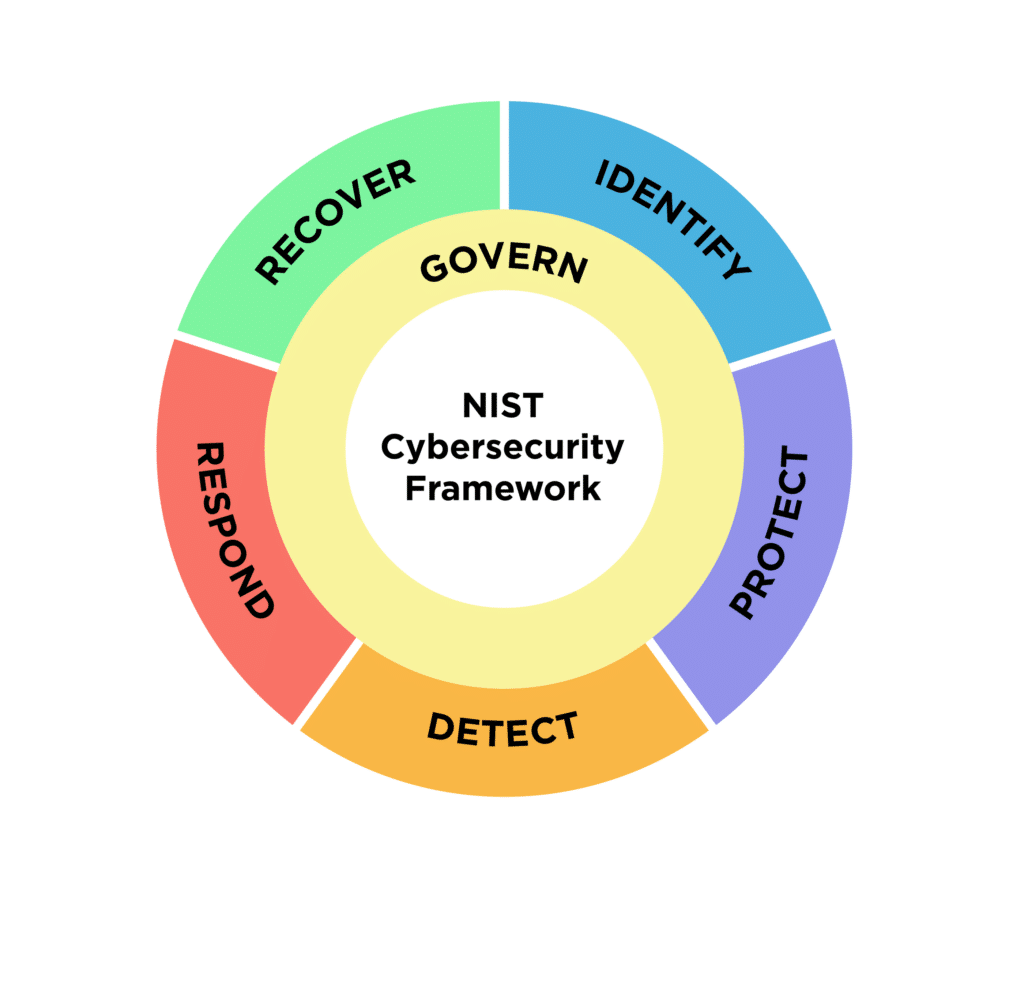
- Identify
- Catalog your assets (hardware, software, data).
- Determine business environment and compliance requirements.
- Conduct a risk assessment to discover vulnerabilities and potential threats.
- Protect
- Develop and implement access control policies, encryption standards, and endpoint protection solutions.
- Train staff on security awareness and provide ongoing education.
- Create secure configurations for all systems (servers, workstations, network devices).
- Detect
- Set up continuous monitoring with SIEM (Security Information and Event Management) tools.
- Deploy intrusion detection systems (IDS) and intrusion prevention systems (IPS).
- Use threat intelligence to stay updated on emerging risks.
- Respond
- Develop an incident response plan that outlines roles, responsibilities, and communication strategies.
- Conduct tabletop exercises and simulations to test your plan.
- Gather post-incident insights to improve your response capabilities.
- Recover
- Maintain secure backups and test restoration processes.
- Create a business continuity plan so you can quickly resume operations.
- Document lessons learned and update policies to prevent repeat incidents.
- Govern
- Align cybersecurity decisions with risk tolerance and strategic goals through clear policies and defined roles.
- Standardize security practices with robust policies, procedures, and accountability measures.
- Track adherence to policies and regulations, using key metrics to drive ongoing improvements.
When pondering NIST CSF vs CIS Controls, recognize that NIST CSF gives you a strategic blueprint that can guide long-term cybersecurity planning. It’s especially handy for Managed Service Providers (MSPs) who need a universal framework to align different customers’ environments with regulatory obligations.
Delving Into CIS Controls Implementation
On the flip side of NIST vs CIS, you have the CIS Controls. Here’s how to get started implementing these critical security actions:
- Start with Implementation Group 1 (IG1)
- Focus on the most basic yet essential cybersecurity steps.
- Create an accurate inventory of authorized and unauthorized devices.
- Maintain secure configurations and implement strict access controls.
- Establish continuous vulnerability management processes.
- Progress to Implementation Group 2 (IG2)
- Fine-tune logging and monitoring to detect suspicious activities.
- Implement email and web protections (e.g., spam filtering, safe browsing).
- Develop formal incident response procedures with more advanced detection capabilities.
- Enhance encryption practices for data at rest and in transit.
- Reach Implementation Group 3 (IG3)
- This stage is for organizations with mature cybersecurity postures.
- Deploy sophisticated data protection tools (like DLP—Data Loss Prevention).
- Integrate threat intelligence for proactive defense.
- Continuously refine security assessments, penetration testing, and auditing.
In the NIST CSF vs CIS Controls debate, CIS Controls can be a straightforward starting point if you want quick, tangible improvements. Each control is designed to reduce the most common attacks, making it easier to prioritize what to tackle first.
Why MSPs Might Prefer NIST CSF
Now, let’s address a specific scenario: MSPs juggling multiple clients. When considering NIST vs CIS for MSP compliance, NIST CSF often wins out due to its strategic nature:
- Scalable Framework
By using the same high-level structure (Identify, Protect, Detect, Respond, Recover), you create a consistent baseline for all your clients. - Regulatory Coverage
Many MSP clients must comply with regulations. NIST CSF directly maps to standards like HIPAA, PCI-DSS, and GDPR, making it easier to showcase compliance. - Comprehensive Risk Management
NIST CSF guides MSPs in conducting risk assessments and building tailored security programs for each client’s needs.
That’s not to say CIS Controls are off the table. In fact, many MSPs use NIST CSF vs CIS Controls in tandem—NIST CSF for the overarching strategy and CIS Controls for day-to-day, hands-on defenses.
Why MSPs Will Want to Implement CIS Controls for Themselves
While the broader strategic nature of the NIST CSF framework is appealing, many MSPs also choose to implement CIS Controls for their own internal operations. In the ongoing NIST vs CIS discussion, here’s why CIS Controls can be a game-changer for MSPs directly:
- Operational Efficiency
By adopting CIS Controls, MSPs can streamline their internal security processes—such as secure configuration baselines, patch management, and continuous vulnerability scanning. This efficiency not only protects the MSP itself but also provides a solid template for client implementations. - Demonstrating Expertise
Clients trust MSPs that practice what they preach. If you use CIS Controls internally, you can show hands-on experience in implementing tangible security measures, reinforcing your credibility. - Actionable Roadmap
CIS Controls offer a clear, step-by-step guide that MSPs can follow. For instance, an MSP might start with IG1 to secure its own endpoints and network devices, then level up to IG2 for more advanced monitoring and incident response. - Quick Wins
CIS Controls are known for their prioritization. MSPs can rapidly address the most critical security gaps in their own environment, reducing risk and providing a blueprint for clients to follow. - Continuous Improvement
Because CIS Controls are regularly updated in response to emerging threats, MSPs can stay current with best practices. This enables them to serve as a real-time security partner for their clients, combining the benefits of NIST CSF vs CIS Controls under one roof.
Implementing CIS Controls in-house helps MSPs not only protect their own data but also sets an example for clients who might be weighing NIST CSF vs CIS Controls themselves.
Using NIST CSF vs CIS Controls Together
You might be wondering: Do I really have to choose between NIST vs CIS? The good news is, you can actually combine both:
- Map the Two Frameworks
- Align each of the five NIST CSF functions with relevant CIS Controls. For instance, under “Identify,” you’d incorporate asset inventory and software inventory controls from CIS.
- Strategic Meets Tactical
- Use NIST CSF to develop a solid, policy-level strategy that resonates with management and complies with regulations.
- Deploy CIS Controls for the nitty-gritty actions like patch management and secure configuration.
- Continuous Improvement
- Perform periodic assessments to see how well your tactical controls support your overarching strategy.
- Update your CIS Controls implementation as new threats emerge and as your organization’s risk landscape changes.
When balancing NIST CSF vs CIS Controls, remember that these frameworks can support one another. Think of it like having a high-level map (NIST CSF) plus a detailed GPS route (CIS Controls) to get you exactly where you need to be.
Challenges in the NIST vs CIS Journey
Naturally, both frameworks come with some hurdles:
- NIST CSF
- Can be overwhelming if you don’t have dedicated cybersecurity staff to navigate its flexibility.
- Requires careful mapping to specific controls and technologies.
- CIS Controls
- Highly technical and mostly focused on IT operations—may not cover broader organizational risk management needs.
- Might need customization if you have unique compliance demands beyond standard best practices.
Still, in the NIST vs CIS discussion, these challenges don’t negate the value of either framework. They just underscore the importance of choosing (and tailoring) the framework that fits best.
Conclusion on NIST CSF vs CIS Controls
Now that we’ve dug into the technical details, you can see how NIST CSF vs CIS Controls isn’t a competition with a single winner. Instead, it’s about picking the right tool—or combination of tools—for your organization’s risk profile, budget, and compliance needs.
- Go with NIST CSF if you need a strategic, risk-based framework that aligns with multiple regulations. This is often the best path for MSPs managing diverse client portfolios.
- Adopt CIS Controls if you’re looking for a highly actionable, technical checklist to tackle the most common attacks. MSPs can also benefit significantly from using CIS Controls internally.
Ultimately, your choice in the NIST vs CIS debate should reflect your organization’s current maturity, resources, and compliance obligations. And remember, you don’t necessarily have to pick just one—blending NIST CSF vs CIS Controls can give you the perfect mix of strategy and execution.
Ready to Fortify Your Cybersecurity Strategy?
Partner with Bright Defense to implement either the NIST CSF or CIS Controls—or both. Our expert team will tailor each framework to your unique environment, ensuring a robust, compliant, and forward-thinking security posture. From initial assessments to hands-on deployment and continuous improvement, Bright Defense is committed to providing a comprehensive approach to your organization’s cybersecurity needs.
Get Started Today
- Expert Guidance: Our seasoned consultants bring deep experience in both NIST CSF and CIS Controls implementation.
- Tailored Solutions: We adapt proven best practices to fit your specific industry, size, and risk profile.
- Ongoing Support: Beyond initial setup, we offer continuous monitoring, training, and updates to keep you ahead of evolving threats.
Secure your organization’s future with Bright Defense. Contact us now to schedule a consultation and take the first step toward a more resilient cybersecurity strategy.
Get In Touch



