
List of Recent Data Breaches in 2026
In an increasingly digital world, the threat of data breaches looms larger than ever. From multinational corporations to individual users, no one is immune.
The headlines are filled with stories of compromised personal information, stolen financial data, and disrupted services, painting a stark picture of our vulnerability.
This blog will delve into the recent surge of data breaches, examining the causes, consequences, and crucial steps we can take to protect ourselves.
We’ll explore the latest trends, analyze the impact on businesses and consumers, and discuss the evolving landscape of cybersecurity.
Let’s begin!
Data Breaches that Occurred in January 2026
1. 4,500 ICE Names Leak Triggers Russian DDoS Chaos
Breach Disclosed: 14 Jan, 2026

A reported DHS insider leak exposed details tied to about 4,500 ICE and Border Patrol workers, and the ICE List project said it would publish verified names as it expanded its database from about 2,000 to roughly 6,500. After news of the planned release, the site’s founder said a Russia sourced DDoS campaign began and disrupted access, pushing the team into recovery work and traffic filtering. The leak surfaced amid heightened backlash after ICE agent Jonathan Ross fatally shot Renee Nicole Good on 7 Jan, 2026, and the incident remained active as of 15 Jan, 2026.
(Source: Cybernews)
2. PayPal Confirms 6 Month Breach, Funds Stolen
Breach Disclosed: 10 Feb, 2026

PayPal confirmed a breach tied to its PayPal Working Capital loan application after a threat actor accessed PayPal systems starting July 1, 2025. PayPal said access continued until Dec 12, 2025, when the incident was detected, and the exposure window ran through Dec 12, 2025. Breach letters dated Feb 10, 2026 began reaching impacted PPWC users, and the Feb 22, 2026 update added user reports of unauthorized transactions, transaction refunds, and forced password resets as containment. PayPal advised heightened monitoring for fraud and phishing using exposed personal details.
In regards to funds stolen, no public aggregate dollar total has been disclosed for the PayPal Working Capital incident because PayPal’s notification language and media reporting describe unauthorized transactions and subsequent refunds without stating a total amount. TechRepublic reported that a few customers experienced unauthorized transactions and that PayPal issued refunds, while publishing no figures.
Source: Forbes, TechRepublic
Read the full PayPal Breach story here!
3. Figure Technology Breach – Nearly 1M Records Stolen
Breach Disclosed: 14 Feb, 2026

Figure Technology Solutions confirmed a data breach that was publicly disclosed on 14 Feb, 2026 after a social engineering attack manipulated an employee into providing access to internal systems, allowing hackers to download a limited set of files, with the threat group ShinyHunters claiming responsibility and posting roughly 2.5 GB of stolen customer records online.
The leaked dataset exposed nearly 967,000 user accounts containing names, dates of birth, email and postal addresses, and phone numbers, raising identity theft and phishing risks for affected individuals. Figure stated it is notifying impacted users and offering credit monitoring while investigators examine the full scope of the incident.
Source: Security Week
- Go through the Entire Figure Breach Story Here!
4. 200K Driver’s Licenses Hacked in youX Breach
Breach Disclosed: 18 Feb, 2026

Sydney fintech youX disclosed a breach on 18 Feb, 2026, after detecting unauthorized access to its systems the prior week and later learning a threat actor had posted data it claimed to have taken.
The attacker alleges exfiltration affecting 444,538 borrowers, including government ID details, phone numbers, email addresses, and home addresses, plus 229,226 driver’s license numbers drawn from nearly 800 broker organizations using the platform.
A public disclosure date earlier than 18 Feb, 2026 has been referenced, yet it remains unverified in accessible reporting. youX said monitoring and defensive controls were raised, outside experts were engaged, and the Office of the Australian Information Commissioner was kept informed.
Source: News.com.au
5. Panera Leak Exposes 5.1M Customer Contacts
Breach Disclosed: 02 Feb, 2026

Panera Bread confirmed a cybersecurity incident after ShinyHunters claimed theft in late Jan 2026 and later leaked a roughly 760 MB archive when extortion failed. Analysis from Have I Been Pwned indicates about 5.1M unique accounts were exposed even though the attackers advertised 14M records, a distinction that still leaves millions of customers at risk.
Leaked fields include names, email addresses, phone numbers, and physical addresses, which can fuel targeted phishing and identity fraud. The leaked archive appears limited to contact data, yet the volume enables long term scam campaigns that mimic Panera support. Panera reported notifying authorities while investigating the access path and reviewing what data left its environment.
Source: BleepingComputer
6. Adidas Extranet Scare: 815,000 Rows Exposed
Breach Disclosed: 17 Feb, 2026

Adidas is investigating a suspected breach tied to an independent licensing partner after a threat actor using the name “LAPSUS-GROUP” posted on BreachForums on 16 Feb, 2026, claiming access to the Adidas Extranet.
The actor claims roughly 815,000 rows were taken, listing names, emails, passwords, birthdays, company details, and technical data, and teasing an extra 420GB linked to France.
Researchers reviewing the dump said the content looks tied to reseller firms and may involve about 130 accounts, yet exposed credentials can drive follow-on phishing. Adidas said there is no sign its core IT, e-commerce systems, or consumer datasets were affected while investigation and partner access checks continue.
Source: Cybernews
7. Odido Leak Exposes 6.2M Customer Data
Breach Disclosed: 12 Feb, 2026

Odido disclosed a cyberattack affecting up to 6.2 million customers after investigators found unauthorized access over the 07 Feb, 2026 weekend. Attackers breached a customer contact system and downloaded varying data, which can include names, addresses, email addresses, mobile numbers, customer numbers, IBANs, dates of birth, and passport or driver’s license details.
Odido said passwords, call records, billing data, location data, and ID document scans were not impacted. The company said it ended access quickly, reported the incident to the Dutch Data Protection Authority, and began notifying impacted customers within 48 hours while external responders increased monitoring.
Source: BleepingComputer
8. Canada Computers Breach Hits 1,284 Guests
Breach Disclosed: 04 Feb, 2026

Canada Computers said its investigation indicates 1,284 customers had personal details and payment card data exposed after unauthorized access to systems supporting its retail website. The company tied risk to guest checkout orders placed between 29 Dec, 2025 and 22 Jan, 2026, while member account checkouts and in store purchases were not implicated.
Canada Computers reported detecting the incident on 22 Jan, 2026, notifying affected customers on 25 Jan, 2026, and alerting law enforcement and regulators.
An external forensic firm is reviewing root cause and scope, and the retailer is offering 2 year credit monitoring and identity protection. Some shoppers reported early warnings that were later corrected.
Source: Yahoo News Canada (CBC)
9. Washington Hotel Ransomware: 22:00 Server Hit
Breach Disclosed: 14 Feb, 2026

Japan’s Washington Hotel chain disclosed a ransomware incident on 14 Feb, 2026, after detecting unauthorized access at 22:00 on 13 Feb, 2026 on a limited set of internal servers. The company cut off external network connections, formed an incident task force on 14 Feb, 2026, and contacted police and outside responders while it reviews possible data exposure.
The firm confirmed access to business data on the affected server and said information leakage remains under investigation. Customer data for the “Washington Net” membership program sits on a separate vendor run server with no confirmed intrusion. Some properties reported card terminal outages, yet operations continued.
Source: Tech Radar
10. BTU Billing Outage After Ransomware Hits BridgePay
Breach Disclosed: 09 Feb, 2026
A ransomware attack on third-party payment processor BridgePay on 6 Feb, 2026 disrupted online billing for about 70,000 Bryan Texas Utilities (BTU) customers, forcing the utility to suspend credit and debit card payments and offer alternative in-person payment options.
The incident began when BridgePay’s systems went offline due to ransomware, affecting multiple organizations and municipalities that rely on its payment infrastructure.
BTU confirmed there has been no evidence of customer data compromise or card information exposure, and it is working with partners to restore services, with no firm recovery timeline announced. BTU is waiving late fees, avoiding service disconnections, and communicating updates through its website and status portals.
Source: KBTX News
11. IDMerit Leak: 3B Records Exposed in 1TB DB
Breach Disclosed: 18 Feb, 2026

IDMerit is investigating after researchers found an unsecured MongoDB instance exposing roughly 3 billion records, including about 1 billion entries of sensitive KYC data across 26 countries. The exposed trove totaled about 1 TB and contained names, dates of birth, addresses, emails, phone numbers, national IDs, and telecom metadata, with the United States accounting for over 203 million records.
Researchers said the database was first observed on 11 Nov, 2025 and was locked down on 12 Nov, 2025; Cybernews published the findings on 18 Feb, 2026. The exposure raises risk of SIM swapping, account takeover, and targeted phishing using verified identity attributes.
Source: SC World
- Check Out the Whole ID Merit Data Breach Story!
12. Coinbase Support Leak Shocker: 30 Users Hit
Breach Disclosed: 03 Feb, 2026

Coinbase confirmed an insider breach on 03 Feb, 2026, after leaked screenshots of an internal support tool surfaced online and were later removed. A contractor improperly accessed customer data in Dec, 2025, affecting about 30 people, according to Coinbase.
The screenshots showed visibility into names, email addresses, phone numbers, dates of birth, KYC details, wallet balances, and transactions, raising targeted phishing and account takeover risk.
Coinbase said the contractor no longer works with the firm, impacted users were notified in 2025, regulators were informed, and identity theft protection was offered. Investigators are assessing whether the screenshot leak relates to the same access.
Source: BleepingComputer.
- Read the Entire Coinbase Data Breach Story!
13. Volvo Shock: 17,000 Exposed In Conduent Hack
Breach Disclosed: 10 Feb, 2026

Volvo Group North America disclosed an indirect breach on 10 Feb, 2026 after learning customer and staff data was exposed through Conduent, a business services provider it uses. Conduent said intruders accessed its systems between 21 Oct, 2024 and 13 Jan, 2025, taking files containing full names, Social Security numbers, dates of birth, health insurance policy details, ID numbers, and some medical information.
Conduent publicly disclosed the wider incident in Apr, 2025. Volvo said nearly 17,000 people were impacted, and notices provide identity monitoring for at least 1 year, plus steps such as credit freezes and fraud alerts. Volvo said no misuse has been confirmed so far.
Source: BleepingComputer
14. Eurail Breach: 1.3TB Dump for Sale Now
Breach Disclosed: 10 Jan, 2026

Rail pass provider Eurail said customer data in a cyberattack is offered for sale, with samples shared on Telegram, while investigators work out how many travelers are affected. Eurail first acknowledged the incident around 10 Jan, 2026, the closest verified date, after finding unauthorized access and data copied from its environment.
Eurail said it notified data protection authorities under GDPR and began customer outreach. The exposed set can include names, contact details, travel companion details, and passport information such as numbers and expiry dates, which raises phishing and identity fraud risk. Criminals claim they stole 1.3TB from cloud storage and support systems and threaten wider release if no buyer emerges.
Source: TechRadar.
15. European Commission Staff Data Exposed in Mobile System Breach
Breach Disclosed: 06 Feb, 2026

The European Commission disclosed a staff data breach on 06 Feb, 2026, after its mobile device management infrastructure detected attack traces on 30 Jan, 2026.
Investigators said intruders may have accessed staff names and mobile numbers, with no confirmed compromise of the mobile devices themselves. The Commission contained the incident and cleaned affected systems within 9 hours while internal response teams began a forensic review to scope access, confirm what data was touched, and identify the intrusion path.
Reporting linked the activity to attacks targeting Ivanti Endpoint Manager Mobile, following Ivanti’s advisory on 29 Jan, 2026 and the Commission’s cybersecurity package announcement on 20 Jan, 2026.
Source: BleepingComputer.
16. Senegal ID System Halted After 139TB Hack Claim
Breach Disclosed: 05 Feb, 2026
Senegal temporarily halted national ID card issuance after the Directorate of File Automation confirmed a cyber incident affecting its population database and opened an investigation.
Reporting tied the intrusion to the “Green Blood Group,” which claimed it breached two DAF servers on 19 Jan, 2026 and later posted proof of compromise, alleging theft of 139TB of data that may include biometrics, identity records, and immigration files.
DAF publicly acknowledged the incident on 05 Feb, 2026 and said technical teams are working to restore services while maintaining data integrity. The outage delays new IDs, passports, and related document workflows nationwide.
Source: Dark Reading.
17. Idaho Clinic Alert: Vendor Hack Risks Patient SSNs
Breach Disclosed: 09 Feb, 2026

Terry Reilly Health Services reported a third-party data security incident on 09 Feb, 2026, after TriZetto Provider Solutions notified OCHIN, the electronic medical record vendor that supports Terry Reilly. Investigators say unauthorized access occurred at the vendor level, and Terry Reilly moved to notify law enforcement and outside cybersecurity specialists while the vendor contained and removed the threat.
Potentially exposed data can include patient names, addresses, dates of birth, Social Security numbers, health coverage member numbers, insurer and provider details, dependent information, and certain health and insurance data. Impacted patients will receive mailed notices within about 1 week with free credit monitoring enrollment instructions.
Source: Terry Reilly Health Services.
18. Japan Airlines Luggage System Breach Hits 28K Users
Breach Disclosed: 10 Feb, 2026

Japan Airlines disclosed a breach affecting up to 28,000 customers after detecting unauthorized access to the Same Day Luggage Delivery Service reservation system at about 12:40 a.m. on 09 Feb, 2026. Impacted records relate to reservations made since 10 Jul, 2024.
Exposed fields may include names, email addresses, phone numbers, JMB customer numbers, flight numbers, departure and arrival airports, and destination hotel names, while credit card numbers and passwords were not in scope.
JAL paused the service, brought in external incident responders, and started log review to confirm whether any data left its environment. Customers should expect targeted phishing that references travel details.
Source: Japan Airlines.
19. Flickr Third Party Email Flaw Exposes User Data Fields
Breach Disclosed: 05 Feb, 2026

Flickr disclosed a third party email system security incident on 05 Feb, 2026, after it was alerted to a vulnerability at an email service provider that may have permitted unauthorized access to Flickr member information and Flickr cut off access within hours.
Exposed data can include names, usernames, email addresses, account types, IP addresses, general location, and Flickr activity metadata, while passwords and payment card numbers were not affected. Flickr stated that exposure is possible rather than confirmed theft, and no threat actor has publicly claimed a Flickr dataset so far. User risk centers on targeted phishing that references account details and IP based location context.
Source: SecurityWeek
20. San Diego Eye Bank Ransomware: 2026 Hit
Breach Disclosed: 08 Feb, 2026

San Diego Eye Bank reported a ransomware event after the pear gang listed the organization as a victim on 08 Feb, 2026, the closest verified public disclosure date. Threat intel tracking links the intrusion to activity dated 04 Feb, 2026, with the listing indicating potential data theft alongside encryption.
San Diego Eye Bank supports corneal donation and transplant services, so exposed files could include operational records and sensitive patient or donor data, though no verified dump has been published. Incident response typically involves isolating affected systems, restoring from clean backups, rotating credentials, and monitoring for extortion follow ups tied to the sdeb.org domain.
Source: ransomware.live.
21. Ivanti Bug Exposes Staff Data at 2 Dutch Agencies
Breach Disclosed: 06 Feb, 2026

2 Dutch bodies disclosed that a flaw in Ivanti Endpoint Manager Mobile let unauthorized parties view staff contact data at the Dutch Data Protection Authority and the Council for the Judiciary.
The notice on 06 Feb, 2026 said exposed fields can include names, work email addresses, and phone numbers, while the number of affected employees remains under investigation.
The Council reported the breach to the regulator, and the regulator filed its own report internally, with both organizations notifying staff and coordinating response with the Dutch NCSC. Officials warned that other agencies using Ivanti could face similar exposure until systems are patched and reviewed.
Source: Tweakers.
22. Everest Claims 1.4TB Iron Mountain Leak
Breach Disclosed: 02 Feb, 2026

Iron Mountain acknowledged an alleged extortion event after Everest posted claims of stealing 1.4 TB of files on 02 Feb, 2026. Iron Mountain said the activity did not reach core systems and did not involve customer confidential or sensitive data.
The company attributed access to 1 compromised login credential that opened 1 folder on a public facing file sharing site used for vendor marketing materials. Everest published folder screenshots as proof and set a negotiation deadline of 11 Feb, 2026, yet independent verification of a large scale theft remains unavailable. Iron Mountain disabled the credential and continues forensic review and monitoring.
Source: Iron Mountain.
23. Romania Pipeline Hit: 1TB Leak Claim
Breach Disclosed: 04 Feb, 2026

Romania’s national oil pipeline operator Conpet disclosed a cyber incident on 04 Feb, 2026, after detecting unauthorized access on 03 Feb, 2026 that disrupted parts of its corporate IT network and knocked its public website offline. Oil deliveries were unaffected.
Conpet said operational technology, including SCADA and telecoms, stayed functional, so crude transport across roughly 3,800 km continued without interruption. The Qilin ransomware group claimed theft of nearly 1 TB and posted sample files, yet Conpet has not confirmed data loss. The company filed a criminal complaint with DIICOT, engaged national cyber authorities, and is restoring affected business systems while the investigation continues.
Source: AGERPRES.
Check Out the Full Romania Pipeline Data Breach Story
24. Hawk Law Group Hit By Incransom
Breach Disclosed: 01 Feb, 2026

Incransom ransomware operators publicly listed Hawk Law Group as a victim on 01 Feb, 2026, after activity tied to the incident was first observed around 31 Jan, 2026 at roughly 23:11 local time. A confirmed public statement from the firm has not been located, so claims about data theft and the final scope remain unverified.
Law firms tend to store sensitive case material and identity documents, which raises risk of client targeted phishing and extortion threats that reference real matters. The safest response is rapid containment, credential resets, system imaging for forensics, and direct outreach to cyber insurers and law enforcement while notification decisions follow verified findings.
Source: Ransomware.live
25. Conduent Breach Hits 25.9M After February Surge
Breach Disclosed: April 9, 2025
Breach Scope Expanded: February 2026
Conduent disclosed its ransomware breach in an SEC filing on April 9, 2025, confirming attackers accessed systems from October 21, 2024 to January 13, 2025 and stole more than 8 terabytes of data. Initial impact estimates near 4 million surged in February 2026, when Texas officials reported 15.4 million residents affected and Oregon identified 10.5 million, pushing the total to at least 25.9 million people. Exposed data includes Social Security numbers and medical information. State investigations intensified in February 2026 as notifications expanded nationwide and scrutiny grew over the scale of the breach.
Source: TechCrunch
26. RTL Group Leak: 27K Employee Records Exposed
Breach Disclosed: 19 Feb, 2026

RTL Group is investigating attacker claims that its intranet was breached in Feb 2026, exposing data on more than 27,000 employees. A leak forum post shared a sample of 100 records showing names, work emails, job details, office addresses, and in some cases work and personal phone numbers. RTL told reporters on 19 Feb, 2026 that customer data is unlikely to be impacted while the review continues.
Employee contact lists can fuel spearphishing, SIM swap attempts, and impersonation of newsroom staff, which can pressure sources and disrupt reporting. Staff should treat unexpected messages as hostile and verify requests through known channels.
Source: Cybernews.
27. Qilin Claims ABAR S.p.A. Hit On 20 Feb, 2026
Breach Disclosed: 20 Feb, 2026

ABAR S.p.A., an Italy based company, was listed by the Qilin ransomware operation on 20 Feb, 2026, which is the earliest verifiable public disclosure located in current reporting and publicly available leak tracker data. The listing provides no narrative details and no confirmed data types, so theft claims remain unverified beyond a posted screenshot.
No public statement from ABAR has been found as of 21 Feb, 2026. Treat this as an alleged incident pending victim confirmation. Risk typically centers on business email compromise, credential reuse, and follow on extortion, so partners should validate any payment or invoice changes through known contacts.
Source: Ransomware.live.
28. Adelphi UK Breach Claim: 16 Feb Leak Threat
Breach Disclosed: 16 Feb, 2026
Adelphi Group of Companies faced an alleged ransomware incident after DragonForce listed adelphi.uk.com on 16 Feb, 2026, with an estimated intrusion date of 11 Feb, 2026. Public reporting has not shown a victim statement confirming encryption or data theft, so the claim remains unverified.
The UK packaging and processing equipment supplier could face order delays and partner impersonation scams. Ransomware listings often signal data extortion pressure, which can drive spearphishing, fake invoice requests, and credential reuse attacks.
Incident response typically isolates affected endpoints, resets privileged credentials, reviews remote access logs, and monitors for copied files or posted samples while notification decisions follow confirmed findings.
Source: (ransomware.live)
29. ADFSA México Breach Buzz: No Public Proof Yet
Breach Disclosed: 21 Feb, 2026
No verified public data breach disclosure for ADFSA México has been located through 21 Feb, 2026, despite searches across major security news coverage and public ransomware leak trackers. Public references identify ADFSA as Almacenes Distribuidores de la Frontera, yet none of the reviewed sources confirm ransomware, data theft, or customer notification activity in 2026.
This gap means the most defensible timeline is that disclosure remains unconfirmed rather than delayed. Organizations connected to ADFSA should treat unsolicited invoice changes, password reset emails, and broker style outreach as high risk and confirm requests through known phone numbers. Continuous monitoring for 30 days helps catch follow on credential misuse.
Source: Ransomware.live.
30. Qilin Ransomware Claims Saiful Bouquet Leak
Breach Disclosed: 17 Feb, 2026

Saiful Bouquet was publicly listed as a ransomware victim on 17 Feb, 2026, after Qilin posted the name on its leak site, a signal that extortion pressure may follow. A confirmed statement from the organization has not been located, so encryption status, data theft, and impacted parties remain unverified.
The safest assumption is increased phishing and impersonation risk that targets staff and vendors with fake invoices, password reset lures, and document share links. Partners should verify payment changes through known contacts, rotate shared credentials, and watch for new samples or a victim notice. Public leak posts sometimes include a negotiation countdown, yet none is visible in the current listing.
Source: Ransomware.live.
31. Crunchbase Hack Exposes 2M Records via ShinyHunters
Breach Disclosed: 27 Jan, 2026

Crunchbase confirmed a data breach after the ShinyHunters cybercrime group published files allegedly stolen from its corporate network, claiming access to more than 2 million records. The exposed data reportedly includes full names, contact details, addresses, job information, contracts, and internal business documents.
After several days of public claims, Crunchbase acknowledged that a threat actor exfiltrated certain documents but stated no business operations were disrupted and systems were secured. The files were released after Crunchbase refused to pay a ransom. The breach surfaced publicly on 27 Jan, 2026, with ongoing review to determine regulatory notification requirements and potential downstream risks such as fraud and social engineering.
(Source: Cybernews)
- Read the Full Crunchbase Story Here!
32. Hinge, Match, OkCupid Leak Dumps 10M Dating Records
Breach Disclosed: 28 Jan, 2026

Match Group said it is investigating a security incident after ShinyHunters claimed the theft of more than 10 million records tied to Hinge, Match, and OkCupid, with the claim posted on 28 Jan, 2026. Reports describe a social engineering vishing campaign aimed at Okta SSO access and downstream exposure from marketing and analytics tooling, with leaked items said to include user IDs, IP addresses, Hinge subscription transaction IDs, amounts paid, internal employee emails, and corporate contracts. Match Group said it ended the unauthorized access, saw no indication of exposed passwords, financial data, or private communications, and began notifications where appropriate, while timelines may reach back to mid-January 2026.
- Learn More About the Match Group Breach!
(Source: BleepingComputer)
33. Nike Probe After 1.4TB Leak Hits Dark Web
Breach Disclosed: 26 Jan, 2026

Nike said it is investigating a potential cybersecurity incident after the WorldLeaks extortion gang claimed it stole and posted samples of 1.4TB of internal files, described as 188,347 items linked to design and manufacturing workflows.
On 26 Jan, 2026, Nike said it was actively assessing the situation while declining to confirm what was taken or whether payment discussions occurred.
Early reporting indicated the material appeared focused on corporate documents rather than customer databases, which reduces immediate account exposure but raises risks for IP theft, counterfeits, supplier fraud, and targeted phishing against employees and partners. Nike had not reported operational disruption at the time of disclosure.
- Read the Entire Nike Data Breach Story Here!
(Source: The Register)
34. Under Armour Leak: 72M Accounts Dumped Online
Breach Disclosed: 22 Jan, 2026

Under Armour said it is investigating claims that customer data tied to 72 million accounts was posted to a hacker forum. The seller told TechCrunch the files came from a November 2025 intrusion previously claimed by the Everest ransomware gang.
The breach gained wider attention this week after Have I Been Pwned obtained the dataset and notified 72 million people. Reported fields include names, email addresses, genders, dates of birth, ZIP codes or postcodes, and purchase related information, plus employee email addresses. Under Armour said there is no evidence the incident affected UA.com or systems that process payments or store passwords, and it has brought in external forensics support.
(Source: TechCrunch)
35. AT&T Data Breach Settlement Offers Up To $5k in Claims
Latest Update: 15 Jan, 2026

AT&T’s settlement process covers 2 incidents announced on 30 Mar, 2024 and 12 Jul, 2024, one tied to a dark web dataset that could include Social Security numbers and another tied to data downloaded from an AT&T workspace hosted with Snowflake that could include phone numbers and call or text interaction counts. Eligible U.S. class members could request documented loss payments up to $5,000 or $2,500, or choose pro rata tier payments, with tier 1 for Social Security number exposure set at 5 times tier 2. The online claim deadline was 18 Dec, 2025, and the court scheduled a final approval hearing for 15 Jan, 2026.
36. 17.5M Instagram Leak: The Reset Email You Must Avoid
Breach Disclosed: 10 Jan, 2026

A report updated on January 10, 2026 ties a BreachForums post to alleged data from 17.5 million Instagram accounts and a spike of password reset emails that began around January 9, 2026. The messages can come from Instagram, which makes the bait convincing, but a reset request still can be attacker triggered.
Meta has not confirmed an internal breach, and some requests may start from simple typos. If you did not request it, do not click the link. Open Instagram, confirm 2FA is on, change your password, review recent logins, and revoke unknown sessions immediately. Also reset your email password if reused, and watch for new recovery emails.
Source: Forbes
View The Full Instagram Story Here
37. Google Chrome 143 Security Bypass Puts 3 Billion Users At Risk
Breach Disclosed: 06 Jan, 2026

Google disclosed a Stable Channel security update on 06 Jan, 2026, pushing Chrome to 143.0.7499.192/.193 on Windows and macOS and 143.0.7499.192 on Linux. The update addresses 1 High-severity issue, CVE-2026-0628, described as “insufficient policy enforcement” in the WebView tag. Google credits researcher Gal Weizman and lists the report date as 23 Nov, 2025. Public technical detail stays limited until most users receive the patch, so treat this as a priority update. Restart Chrome after updating, then confirm the version across personal devices and managed fleets. (Chrome)
Check out the entire Chrome story here!
38. Oracle E-Business Suite Hack Still Generating Ransom Demands
Breach Disclosed: Started in Oct 2025, Still Ongoing

Executives at many large organizations are getting ransom demands weeks after a zero-day exploit in Oracle’s E-Business Suite was first identified. The criminal group linked to CL0P claimed it accessed sensitive ERP data and emailed leaders from compromised third-party accounts on or before Sept 29, 2025, demanding payment to prevent leaks. Patches were released in Oct 2025, but extortion continues and the number of companies receiving demands has risen past 100, including universities and major corporations. Experts say the attack exploited remote access flaws and emailed executives directly, pressuring them with seven- and eight-figure ransom figures.
Some of the major Oracle breach victim organizations include:
- Harvard University received ransom demands after data tied to its Oracle EBS systems was targeted.
- The Washington Post confirmed it was impacted and had to notify customers about a breach.
- Envoy Air (an American Airlines subsidiary) appeared on lists of targeted organizations.
Cox Enterprises showed up in the victim set reported by investigators. - Logitech was named among affected companies in reports tied to the campaign.
- Schneider Electric, Emerson, Pan American Silver, and LKQ Corporation appeared on leaked victim lists although not all confirmed the breach publicly.
- University of the Witwatersrand was cited on CL0P’s victim blog and various reports. (Wall Street Journal)
Read about the Entire Oracle EBS Breach Story Here!
39. ManageMyHealth Breach Exposes Up to 126K Users
Breach Disclosed: 01 Jan, 2026

ManageMyHealth, New Zealand’s largest patient portal (about 1.8 million registered users), disclosed a cybersecurity incident involving unauthorized access to its application after the company was alerted on Dec 30, 2025. Initial containment actions focused on securing the platform, preserving evidence, and engaging independent cyber and forensic specialists.
ManageMyHealth later stated that approximately 6% to 7% of users may be impacted, roughly 108,000 to 126,000 people, with notifications expected within 48 hours. Authorities including Health New Zealand, Police, and the Privacy Commissioner were notified, while investigations continued with additional public clarification issued on Jan 2, 2026. (Manage My Health)
Get The Full Managemyhealth Breach Story Here!
40. Ledger Leak: Names, Addresses Exposed
Breach Disclosed: 05 Jan, 2026

On 05 Jan, 2026, Ledger confirmed customer order data exposure after unauthorized access inside Global-e, an e-commerce partner used for some Ledger.com purchases. Global-e said an intruder copied personal data that can include names, postal addresses, email addresses, telephone numbers, and order details such as order number, product purchased, and price paid.
Ledger said its own platform, devices, and Ledger Live were not breached, and 24-word recovery phrases, balances, and payment data were not accessed. Global-e reported it contained the activity and started notifying affected people and regulators. Ledger warned customers to expect phishing in the days ahead and never share recovery phrases. (siliconangle.com)
Check out more about the Ledger Leak Here!
41. Brightspeed Breach: Hackers Claim 1M Hit
Breach Disclosed: 05 Jan, 2026

Crimson Collective says it accessed Brightspeed systems and took data on over 1 million customers. Reporting cites a Telegram post on 04 Jan, 2026 and a threat to drop a data sample on Monday night, 05 Jan, 2026, unless Brightspeed replied.
The alleged haul includes names, emails, phone numbers, billing addresses, account details linked to session or user IDs, payment history, partial card information, and appointment or order records.
Brightspeed acknowledged a reported cybersecurity event on 05 Jan, 2026 and said it is investigating, with updates for customers, employees, and authorities as facts firm up. Customers should watch for phishing and account takeover attempts, reset passwords, and review billing activity. (Bleeping Computer)
42. 34,504 Texans Hit In Vida Y Salud Data Breach
Breach Disclosed: 05 Jan, 2026

Vida Y Salud-Health Systems, a Crystal City, Texas FQHC, detected suspicious network activity on 08 Oct, 2025. Forensics found an unauthorized actor accessed systems between 07 Oct, 2025 and 08 Oct, 2025, copying files that could include names, Social Security numbers, driver’s license numbers, addresses, dates of birth, medical information, and account or claim numbers.
A filing with the Texas Attorney General reported 34,504 affected Texans on 05 Jan, 2026. The organization secured its network, brought in outside specialists, notified law enforcement and regulators, and began mailing notices plus credit monitoring. A dedicated help line, 833-792-0594, runs 7 AM to 7 PM CST on weekdays. (claimdepot.com)
Data Breaches that Occurred in December 2025
1. ESA Confirms Cybersecurity Incident After Hacker Claims 200GB Data Theft
Breach Disclosed: 30 Dec, 2025

The European Space Agency (ESA) confirmed a cybersecurity incident involving a small number of external servers located outside its corporate network, after a threat actor claimed to have stolen about 200GB of data and offered it for sale. ESA said the impacted systems supported unclassified collaborative engineering and scientific work, not core mission or classified environments.
The agency launched a forensic investigation, began securing potentially affected devices, and notified relevant stakeholders. Public reporting indicates the actor shared proof samples, including references to private development repositories, though details remain under validation as ESA’s analysis continues. (TechRadar)
2. Pornhub Premium Leak Exposes 201M Data
Breach Disclosed: 12 Dec, 2025

Pornhub says a “select” number of Premium users had viewing behavior and search activity exposed after an unauthorized party accessed Mixpanel analytics data, not Pornhub’s own systems.
Reports indicate ShinyHunters obtained roughly 201M records covering user emails, locations, video URLs, video names, keywords, and event timestamps.
ShinyHunters allegedly issued an extortion demand and sought bitcoin payment to prevent publication. Pornhub stated passwords and payment information were not exposed and emphasized it ended its Mixpanel relationship in 2021, suggesting the dataset is historical.
Sophos said it has not seen the data posted to leak sites yet. (Guardian) Read the whole PornHub story here!
3. SoundCloud Reports Breach Exposing Emails of 20% of Users
Dec 15, 2025

SoundCloud disclosed a data breach after detecting unauthorized activity within an ancillary service dashboard. The company confirmed that attackers exfiltrated email addresses and other information already visible on public user profiles, affecting about 20% of its user base.
Based on third-party estimates of roughly 140 million total users, the incident likely impacts tens of millions of accounts. SoundCloud stated that passwords, financial data, and private content were not accessed.
During remediation, configuration changes caused VPN users to encounter “403 Error” access issues, which the company linked directly to its response efforts. After containment, SoundCloud experienced denial-of-service attacks, with two incidents briefly disrupting web availability.
The company said the threat has been resolved and urged users to remain alert for phishing attempts that often follow large-scale data exposures. (Cybernews) Read the whole Soundcloud story here!
4. 700Credit Breach Exposes SSNs of 5.6 Million People
Dec 22, 2025; Michigan, United States

700Credit disclosed a data breach that exposed highly sensitive personal information belonging to at least 5.6 million individuals. The Michigan-based credit check and identity verification provider said an unidentified attacker accessed data collected from auto dealerships between May and October 2025.
Stolen information includes full names, home addresses, dates of birth, and Social Security numbers, creating a significant risk of identity theft and financial fraud.
The company is notifying affected individuals by mail and offering credit monitoring services. Michigan Attorney General Dana Nessel urged recipients to act quickly, recommending credit freezes or monitoring to reduce the likelihood of misuse of stolen data. (TechCrunch)
Read more about the 700Credit Breach here.
5. GPS Spoofing Cyber Attack Targets 7 Major Indian Airports
Dec 1, 2025; India

India’s central government confirmed that seven major airports were targeted in a cyber attack involving GPS spoofing that affected aircraft navigation during landing procedures.
Flights approaching Runway 10 at Delhi’s Indira Gandhi International Airport reported misleading GPS signals, with similar incidents identified at airports in Mumbai, Kolkata, Hyderabad, and Bengaluru. GPS spoofing transmits false location and altitude data to navigation systems.
Authorities said no flights were cancelled or diverted because air traffic control relied on backup procedures and existing safeguards.
Following the incident, aviation and security agencies increased monitoring, placed affected airports on high cyber alert, and began implementing additional countermeasures. (Financial Express)
6. Nissan Confirms Customer Data Exposure of 21k Customers
Dec 23, 2025

Nissan Motor Co. confirmed that unauthorized access to servers managed by Red Hat exposed personal data linked to approximately 21,000 customers of Nissan Fukuoka Sales.
The incident occurred in September and stemmed from Red Hat’s role in developing customer management systems for Nissan sales operations. Exposed data includes customer names, addresses, phone numbers, email addresses, and sales related records.
Nissan stated that no credit card or financial information was involved and that no additional Nissan data was stored in the affected environment. Red Hat disclosed the breach in early October. Nissan said it has reported the incident to authorities and found no evidence of data misuse. (Data Conomy)
Read the Whole Nissan Breach Story Here!
7. Spotify Investigates Scraping of 256M Tracks & 86M Files
Dec 22, 2025; Stockholm, Sweden

Spotify confirmed it is investigating unauthorized scraping of its music library after a pirate activist group claimed it released metadata covering roughly 256 million tracks and 86 million audio files. The data reportedly spans content added between 2007 and 2025 and represents nearly the full catalog. S
potify said the third party used illicit tactics to bypass DRM and access some audio files. The company stated it disabled involved accounts, added safeguards, and continues monitoring activity. Spotify reported no evidence of non public user data exposure, noting that any user related information involved only public playlists.
Hackers claimed the dataset totals just under 300 TB and could circulate on peer to peer networks. Rights holders raised concerns about potential misuse for large scale AI training, while Spotify reiterated its stance against piracy and support for artists. (Euronews)
Go Through the Entire Spotify Breach Story Here!
8. Marquis Vendor Breach Exposes Data of 400,000+ Bank Customers
Dec 3, 2025
Financial services vendor Marquis disclosed that a ransomware attack exposed sensitive personal and financial data tied to more than 400,000 bank and credit union customers across the US.
The intrusion occurred in August after attackers exploited an unpatched SonicWall firewall vulnerability to access Marquis systems. Exposed data includes names, addresses, dates of birth, Social Security numbers, bank account details, and debit or credit card numbers.
Texas reported the highest number of affected individuals, with additional disclosures filed in several other states. Marquis provides services to over 700 financial institutions, allowing the breach to impact customers across multiple organizations.
The attack has been widely linked to the Akira ransomware group, though Marquis has not publicly named the attackers. (Fox News)
9. Asus Supplier Breach Raises Alarm After Ransomware Gang Claims 1 TB Data Theft
Dec 5 2025, Taiwan
Asus reported that a third party supplier suffered a ransomware intrusion after the Everest group claimed it had taken 1 TB of data tied to Asus, ArcSoft, and Qualcomm. Asus stated that stolen material involved camera source code used in its phone line, and that no internal systems, products, or customer data were affected.
Everest posted screenshots on its leak site and asserted that the haul included binary modules, firmware tools, RAM dumps, AI models, calibration files, test datasets, and debug logs. Asus has not validated those wider claims or clarified whether proprietary assets beyond the camera code were exposed.
The vendor’s disclosure followed recent warnings that about 50,000 Asus routers had been compromised in a separate China linked campaign targeting outdated firmware. Although unrelated, the supplier breach added pressure on the company as investigators assess the resilience of its supply chain and development processes. (The Register)
10. Penn and Phoenix Universities Hit in Oracle EBS Campaign That Exposed Sensitive Records
Oct 2025 to Nov 21 2025, disclosed Dec 3 2025, United States

The University of Pennsylvania and the University of Phoenix confirmed their involvement in the widespread Oracle E-Business Suite hacking campaign disclosed in Dec 2025. Both institutions reported that attackers accessed personal and financial data through compromised Oracle EBS systems used for core business functions. Penn began sending notices after determining that nearly 1500 Maine residents were affected, though the full count remains unknown.
Phoenix detected the intrusion on Nov 21, one day after appearing on the Cl0p leak site. Investigators found that names, contact details, birth dates, Social Security numbers, and bank account information were exposed. While other victims saw hundreds of gigabytes released online, no Phoenix data has surfaced publicly, and Cl0p has not yet listed Penn.
The campaign has touched more than 100 organizations, including Harvard, Dartmouth, Canon, Mazda, Cox, and Logitech. Analysts continue to examine the zero-day flaws and threat actors behind the activity. (Security Week)
11. Renesas Electronics Hit with Ransomware Claim from CoinbaseCartel
Dec 6 2025, Japan

Renesas Electronics was named in a ransomware claim on Dec 6 2025 after the group CoinbaseCartel stated it had attacked the company and would release stolen data unless contact was made through specified channels. Renesas, a key semiconductor manufacturer, is reviewing its systems to determine whether data was removed and how the intrusion occurred.
No technical details have been confirmed, but the threat suggests possible exposure of internal files. Security teams are monitoring dark web activity while investigators check for persistence and assess the impact.
Recommended actions for organizations in similar situations include a rapid compromise assessment, verified offline backups, updated threat intelligence, stronger authentication controls, and early coordination with incident response specialists who can support technical and legal decisions as the investigation continues. (Dexpose)
12. TridentLocker Claims 30 GB Data Theft in Breach Affecting bpost
Dec 3 2025, Belgium

bpost confirmed a data breach after the ransomware group TridentLocker posted 5,140 files totaling more than 30 GB on its leak site. The material was fully downloadable, a sign that bpost did not meet ransom demands. Early reports from Tweakers.net highlighted the exposure, but the authenticity of all files has not been independently verified.
bpost stated that the breach involved a limited set of personal and business information tied to a department that operates through a third party exchange platform not connected to core letter or parcel operations. The company reported that security teams contained the incident, applied corrective measures, and engaged external specialists.
bpost also notified authorities and is preparing direct outreach to affected customers. TridentLocker, a newer ransomware operation, has claimed attacks on several organizations this year. The scale of the posted data suggests at least partial exfiltration despite bpost’s ongoing investigation. (Cybernews)
13. Data Breach Hits Over 22M Aflac Customers
Breach Disclosed: Publicly confirmed Dec 19, 2025

Major U.S. insurance firm Aflac had data from nearly 22.7 million customers, beneficiaries, employees, and agents stolen following a cyberattack in June, reports The Record, a news site by cybersecurity firm Recorded Future.
Unauthorized access to Aflac’s systems has been thwarted “within hours” of the intrusion’s discovery but not before threat actors were able to pilfer documents containing individuals’ insurance claims, Social Security numbers, and health details, according to the Georgia-based insurance giant.
Aflac, which emphasized that it did not experience a ransomware intrusion, offered two years of complimentary identity protection services to individuals affected by the incident. Such an intrusion against Aflac came amid Scattered Spider’s attack spree against multiple insurance companies, including the Philadelphia Insurance Companies, Erie Insurance, and Scania Financial Services.
Aside from having its data leak site dismantled by U.S. and French law enforcement in October, Scattered Spider also had its members apprehended and indicted in the UK. (SC World)
14. Rainbow 6 Siege Breach Hands Out ~2B Credits to Gamers
Breach Disclosed: 27 Dec, 2025

Ubisoft confirmed a major Rainbow Six Siege incident on Saturday, Dec 27, 2025, after widespread player reports showed attackers abusing internal systems to ban and unban accounts, inject fake moderation ticker messages, and grant roughly 2 billion R6 Credits plus Renown alongside unlocking all cosmetics, including developer-only skins. R6 Credits are premium currency, and the injected balance equated to an estimated $13.33 million at Ubisoft’s pricing. Ubisoft took Siege and the in-game Marketplace offline, disabled the ban ticker, and announced a rollback of all transactions since 11:00 AM UTC, while stating players would not be punished for spending the credits. (Bleeping Computer)
15. Hacker Posts 2.3M WIRED Records After Alleged Condé Nast Breach
Breach Disclosed: 20 Dec, 2025

On 20 Dec, 2025, a threat actor named “Lovely” posted an alleged WIRED subscriber database from Condé Nast, offering access for about $2.30 in forum credits and warning that 40+ million more records from other brands could follow. Review of the leak shows 2,366,576 records and 2,366,574 unique email addresses, with timestamps from 26 Apr, 1996 to 9 Sep, 2025. Some entries also include names, phone numbers, physical addresses, gender, and birthdays, though many fields are empty. Condé Nast has not confirmed the incident. Treat it as a phishing risk: change reused passwords tied to your WIRED login and enable MFA. (bleepingcomputer.com)
16. Coupang Breach: Hackers Laptop Dumped in the River, Recovered Anyway
Date: 29 Nov, 2025

Coupang says its insider breach probe took a soggy turn after divers recovered a smashed MacBook Air from a nearby river, allegedly dumped in a brick weighted canvas bag to erase evidence. The South Korean e-commerce giant disclosed that 33.7 million customer accounts were exposed after unauthorized access was detected on Nov 18. Coupang says digital fingerprints and third party forensics teams inventoried the recovered laptop, identified a former employee, and found the person kept data from about 3,000 accounts, then deleted it after media coverage, with no sign of sales or sharing so far. It also announced 1.685 trillion won ($1.18B) in vouchers while scrutiny and lawsuits continue. (The Record)
17. Anubis Claims 30k Patient Records in AllerVie Health
Breach Disclosed: 22 Dec, 2025
AllerVie Health, an allergy and immunology provider based in Frisco, Texas, detected unusual network activity on 2 Nov, 2025 and later confirmed unauthorized access between 24 Oct, 2025 and 3 Nov, 2025. A records review on 24 Nov, 2025 found exposure of names and government identifiers such as Social Security and driver’s license or state ID numbers; reporting also points to possible addresses, dates of birth, insurance details, and health information.
AllerVie mailed notices on 22 Dec, 2025, offered credit monitoring and identity theft protection, and reported the incident to state regulators on 23 Dec, 2025. The Anubis ransomware group claimed responsibility on 26 Nov, 2025 and asserted over 30,000 patient records. (The HIPAA Journal)
18. Petco Breach: 500+ Californians Affected After Files Go Online
Breach Disclosed: 03 Dec, 2025
Petco disclosed a data exposure on Dec 3, 2025, inferred from a report that cited a Wednesday filing with California’s attorney general, after a software application setting left certain files accessible online. The state posted a sample notice saying Petco found the issue during a routine security review, corrected it immediately, and removed the files from online access.
The letter does not list the specific data elements, though Petco said it provided more detail to affected people. California’s 500-resident threshold suggests at least 500 affected customers in the state, plus an unspecified number in Massachusetts and 3 in Montana. I used AI to condense reporting into a clear timeline.(techcrunch.com)
Data Breaches that Occurred in November 2025
1. Coupang Data Breach Exposes 33.7M Accounts
Breach Happened: 24 Jun, 2025
Breach Disclosed: 29 Nov, 2025

Coupang disclosed that 33.7 million customer accounts had personal data exposed after unauthorized access persisted for nearly 5 months. Investigations indicate access began June 24, 2025, via overseas servers and continued until November 8, with unusual activity detected on November 6 and the incident confirmed on November 18. Exposed data reportedly included names, phone numbers, emails, delivery addresses, and purchase history, while payment data and passwords were not accessed. Reporting says a former employee retained authentication keys after leaving, enabling insider credential abuse. Regulators, lawsuits, and major fines remain likely.
2. Hackers Steal Salesforce Data From 200+ Companies
Incident disclosed 14 Nov 2025 Silicon Valley

Hackers stole Salesforce-hosted data linked to more than 200 companies after compromising third-party apps developed by Gainsight. Salesforce reported unauthorized access to customer environments that originated from external application connections rather than flaws in its platform.
Google Threat Intelligence confirmed the scale of exposure, noting hundreds of affected Salesforce instances across multiple sectors.
Soon after the disclosure, Scattered Lapsus Hunters claimed responsibility in a Telegram channel and listed companies that included Atlassian, GitLab, Malwarebytes, SonicWall, Verizon, and others.
Several firms said they were still investigating, while CrowdStrike reported it had dismissed an insider tied to suspicious activity. Early indicators showed the attackers first breached Salesloft customers, stole Drift authentication tokens, then used those tokens to enter connected Salesforce environments and pull stored data.
Salesforce revoked all Gainsight-related tokens as a precaution. Gainsight engaged Mandiant and launched a forensic review while Salesforce began notifying affected customers. (TechCrunch)
3. DoorDash Confirms Breach Exposing Customer Contact Data
Incident occurred Oct. 2025, disclosed 18 Nov 2025 San Francisco
DoorDash confirmed a data breach that occurred in October 2025 after an employee fell victim to a social engineering scam. The attacker gained access to internal systems that held names, phone numbers, physical addresses, and email details for an undisclosed number of customers.
DoorDash said sensitive data such as Social Security numbers, government IDs, driver’s license information, and payment card data were not accessed.
The response team detected the intrusion, cut the attacker’s access, began an internal investigation, and notified law enforcement. The company brought in an external cybersecurity firm to support the review.
DoorDash also rolled out new security controls and issued additional employee training focused on social engineering risks. Wolt and Deliveroo customers under the DoorDash umbrella were not affected. This marks the company’s third breach in six years, following incidents in 2019 and 2022, prompting calls for a deeper security reassessment. (Infosecurity Magazine)
4. Harvard Donor Cybersecurity Data Breach Follows 3 Ivy Attacks in 2025
Cybersecurity Breach discovered Nov. 22, 2025 Cambridge, Massachusetts
Harvard confirmed that information systems used by its Alumni Affairs and Development Office were accessed this week after a phone-based phishing attack.
An attacker used social engineering on the phone to gain credentials, then reached systems holding donor records, event attendance data, and contact details including email, phone, and home addresses.
Administrators say these systems typically do not store Social Security numbers, passwords, or bank account numbers, and they have not yet determined exactly what data the intruder viewed or exfiltrated. Harvard cut off the attacker’s access on Tuesday and engaged external cybersecurity experts and law enforcement.
A new breach information site and FAQ explain that alumni, donors, family members, and some current students and faculty may be affected. The university has not committed to direct notifications. The incident mirrors recent phone-based attacks on development offices at Princeton, Penn, and Columbia that also targeted donor records and contact data. (The Harvard Crimson)
5. Washington Post Confirms Theft of Data on 9,720 Workers in Oracle Zero Day Attack
Oct 27 2025, Washington DC
The Washington Post verified a breach that exposed sensitive records on 9,720 current and former employees and contractors after attackers accessed its Oracle E Business Suite environment. A threat actor contacted the company on Sept 29 claiming access to its Oracle applications. An internal review later confirmed that the intrusion spanned July 10 to Aug 22. The attackers stole names, Social Security numbers, and bank account information.
This incident forms part of Clop’s broader campaign that exploited CVE 2025 61882 and additional Oracle flaws. Dozens of organizations faced similar thefts, and ransom demands reached $50 million. Oracle issued patches on Oct 4, but customers did not recognize the intrusion activity until extortion emails surfaced in late September.
The Washington Post said it continues working with investigators. The company has not publicly explained the delay between the initial alert and the final confirmation of stolen data. (Cyberscoop)
6. GlobalLogic Breach Exposes Data of 10,500 Employees in Oracle Zero Day Campaign
Oct 9 2025, California and Maine
GlobalLogic reported a significant breach tied to the Oracle E Business Suite zero day exploited in Clop’s attack spree. The company confirmed that attackers accessed its Oracle environment from July 10 through Aug 20, with the breach discovered on Oct 9. Nearly 10,500 current and former employees had personal and financial details exposed. The intrusion traced back to a flaw later assigned CVE 2025 61882. Oracle released patches on Oct 4 after months of silent exploitation across dozens of victim organizations.
The attackers stole data sets containing names, contact details, dates of birth, nationality information, passport data, Social Security numbers, salary details, and bank account numbers. Clop paired the zero day with additional Oracle vulnerabilities, then launched extortion attempts with demands reaching $50 million. GlobalLogic activated internal response steps, contacted law enforcement, engaged third party investigators, and applied Oracle’s fixes. The company said its non Oracle systems were not affected. (Cyberscoop)
7. Logitech Confirms Zero Day Breach After Clop Claims Data Theft
Incident revealed Nov. 2025 via SEC filing, reported from Fremont California
Logitech reported a recent breach after hackers exploited a zero day flaw in a third party software platform and copied data from its internal IT system. The company’s SEC filing said the exploited bug was patched once the vendor released an update.
Stolen data likely included limited details tied to employees, consumers, customers, and suppliers. Logitech stated that national ID numbers, credit card information, and other sensitive records were not stored in the affected system.
The attack did not affect hardware, manufacturing, or business operations, and the company expects cyber insurance to cover related expenses.
The disclosure came one week after the Clop group claimed it accessed Logitech through a zero day in Oracle’s E Business Suite. Logitech declined to confirm the link. Security teams at Google and others reported that attackers used several Oracle vulnerabilities in this campaign. Multiple organizations have since confirmed related data theft incidents. (The Record)
8. Somalia eVisa Cybersecurity Breach Exposes Data of 35000 Applicants
Nov 13, 2025 Mogadishu
Somalia confirmed a breach of its electronic visa system after foreign governments warned travelers about exposed personal data. Officials reported that unknown actors accessed records for at least 35000 applicants, including thousands of US citizens.
The first alerts surfaced on Nov 13 when the US Embassy reported unauthorized access and noted the scale of the leak. The UK issued a similar notice the next day and urged travelers to consider the risks before submitting new applications.
Attention grew after users on X shared what appeared to be applicant details. Somali authorities had promoted the eVisa system as a security tool that blocked extremist groups from entering the country. The government moved the portal to a new domain without offering an explanation.
Investigators are working to define the source and scope of the cybersecurity breach. Officials plan to release a public report and notify affected individuals. Political tension with Somaliland increased after its leaders criticized Mogadishu’s response. (Al Jazeera)
9. Allianz UK Targeted in Clop’s Oracle E-Business Suite Attack
Allianz UK confirmed a cyber incident linked to the Clop ransomware group exploiting CVE-2025-61882, a critical Oracle E-Business Suite flaw rated 9.8 CVSS. The breach affected systems managing home, auto, pet, and travel insurance policies.
The insurer reported the attack to the UK Information Commissioner’s Office but declined to comment on ransom demands. The incident is separate from the July 2025 Allianz Life breach in the U.S., which exposed 1.4 million customer records.
Researchers at Google Threat Intelligence Group believe exploitation began in July 2025, giving attackers a months-long advantage. Other confirmed victims include the Washington Post and Envoy Air, with analysts warning that dozens of organizations have been affected.
Clop’s latest campaign reflects its continued targeting of enterprise systems, following its 2023 MOVEit attack that impacted more than 95 million people and 3,000 organizations worldwide. (CyberPress)
10. Swiss Bank Hit by Qilin Ransomware Group in Major Data Theft
On November 5, 2025, the Qilin ransomware group claimed responsibility for attacking Habib Bank AG Zurich. The group alleged it stole over 2.5 terabytes of data and nearly two million files, including customer details, transaction records, and internal source code. Screenshots shared on Qilin’s dark web site appeared to support these claims.
The bank, which operates in Switzerland, the UK, the UAE, Hong Kong, Kenya, South Africa, and Canada, has not yet confirmed the breach. Experts warn that the stolen data could expose customers to financial and identity risks.
Qilin, active since 2022, is known for targeting large organizations and has recently allied with LockBit and DragonForce. The Habib Bank attack adds to a series of major financial breaches this year, showing the growing threat ransomware poses to global banking institutions. (Cybernews)
11. Data Leak Linked to Russian and Chinese Hackers Targets Tisza Party Supporters in Hungary
A political data leak in Hungary has raised concerns after the personal details of about 200,000 Tisza Party sympathizers appeared online. The breach, reported on October 31 on the site LeakBase.la, exposed names, email addresses, home addresses, and phone numbers of users who registered through the Tisza Világ app.
Opposition leader Péter Magyar responded in a recorded statement on November 6, accusing international networks with Russian and Chinese ties of trying to influence Hungarian politics. He said these groups aim to keep Prime Minister Viktor Orbán in power and claimed they were behind the attack on Tisza’s supporter database.
The leaked list was later shared by Prohardver.hu, a major Hungarian IT portal, before being removed. Government-aligned media confirmed its authenticity after an individual recognized their own data. The National Authority for Data Protection and Freedom of Information (NAIH) has opened an investigation into the incident, which could lead to penalties for the Tisza Party.
Magyar announced a new strategy in response to the leak, shifting the Tisza candidate voting process to a separate website, nemzethangja.hu, instead of the compromised app. He also urged supporters to remain calm, alleging that the leak was part of an intimidation effort against opposition voters. (Daily News Hungary)
12. RansomHouse Claims Attack on Japanese Retailer Askul
On November 3, 2025, Japanese retailer Askul confirmed that customer and supplier data was exposed after a ransomware attack earlier in October disrupted its e-commerce operations. The breach affected Askul’s main platforms Askul, Lohaco, and Soloel Arena, revealing user contact details, inquiry records, and supplier information stored on internal servers.
The RansomHouse group took credit for the attack, claiming to have stolen 1.1 terabytes of data. Unlike traditional ransomware operators, RansomHouse focuses on extortion without encrypting files, threatening to release stolen information if victims refuse to pay. The group has been linked to several Russia-aligned threat actors, including Alphv/BlackCat, LockBit 3.0, and RagnarLocker.
Askul’s logistics network supports major Japanese retailers such as Muji and The Loft, whose operations were disrupted, though neither company has confirmed a direct data impact. The company issued an apology and continues to investigate the scope of the breach.
The incident follows a series of cyberattacks against Japanese businesses this year. In October, Asahi Group Holdings and TEIN, an automotive parts manufacturer, both reported ransomware disruptions tied to Russian-speaking gangs, marking an escalating wave of attacks on Japan’s corporate sector. (The Record)
13. French Football Federation Reports Exposure of Data for Millions of Amateur Players
Nov 20 2025, France
The French Football Federation confirmed a breach that exposed personal details for a large population of amateur players across the country. The intrusion took place on Nov 20 through a compromised account tied to the platform used for player registration and administrative tasks across all licensed clubs. The exposed records included names, genders, birth details, nationalities, contact information, postal addresses, and football license ID numbers. The discovery on Nov 26 prompted immediate password resets and shutdown of the compromised account.
The federation contacted law enforcement, reported the incident to CNIL and ANSSI, and committed to notifying every affected person with an email address in the database. Officials also warned license holders to watch for phishing attempts that may follow this breach. Public data from the 2023 to 2024 season showed more than 2.3 million license holders, which gives a sense of the potential scale. This event followed a similar attack on the French Shooting Federation earlier in the month. (Infosecurity Magazine)
Data Breaches that Occurred in October 2025
1. Qantas Data Leak: Hackers Release 5.7 Million Records After Ransom Deadline Cross
Hackers from Scattered Lapsus$ Hunters have reportedly leaked the personal information of 5.7 million Qantas customers after a ransom deadline expired on October 11.
The group, an alliance of Scattered Spider, ShinyHunters, and Lapsus$ members, claimed to have stolen data from 39 companies using Salesforce based systems, affecting over one billion records worldwide. Other victims include Toyota, Disney, McDonald’s, and HBO Max.

The Qantas data, believed to come from a July 2025 breach of a Salesforce hosted customer service platform, includes names, emails, phone numbers, addresses, dates of birth, genders, frequent flyer numbers, status tiers, and points balances.
Despite Salesforce refusing to pay ransom or negotiate, the hackers published Qantas related data on the dark web with the message: “Don’t be the next headline, should have paid the ransom.”
Qantas has launched an investigation into dark web sources to confirm the leak’s extent. The airline also obtained a Supreme Court injunction to block data publication, though this cannot prevent dark web circulation.
Salesforce said it is working with authorities and reiterated that its core systems remain uncompromised, linking the incidents to unauthorized third party apps.
Qantas is offering 24/7 support and identity protection services to affected customers while advising vigilance against potential scams. (news.com.au)
2. Louvre Museum Jewelry Heist Exposes Cybersecurity Weaknesses
On October 19, 2025, the Louvre Museum in Paris suffered a high-profile theft of the French Crown Jewels from the Apollo Gallery. The heist, executed in daylight by a group posing as construction workers, highlighted serious weaknesses in both physical and digital security controls.
Investigations revealed that the museum’s video surveillance systems suffered from outdated software, weak passwords, and network segmentation flaws. Earlier audits found that the CCTV network used credentials such as “LOUVRE” and “THALES”, leaving administrative access open to misuse. These lapses undermined camera coverage and incident response during the theft.
While authorities have no evidence of a live cyberattack disabling alarms or cameras, the museum’s poor digital hygiene combined with blind spots in surveillance amplified the attackers’ advantage. Officials admitted that the museum’s security technology was years behind standard for a site housing national treasures.
Experts warn that such issues show how cybersecurity and physical protection are inseparable for cultural institutions. Default credentials, legacy systems, and weak network boundaries can turn physical theft into a broader digital incident affecting footage integrity and investigative outcomes.
(Sources: Reuters, Independant , AP)
3. Crimson Collective Strikes: Red Hat Hit with Major Data Breach
A cyber extortion group calling itself the Crimson Collective claimed to have breached Red Hat’s private GitHub and GitLab systems, stealing roughly 570GB of compressed data from more than 28,000 internal repositories. The leak allegedly includes about 800 Customer Engagement Reports (CERs) containing infrastructure details, configuration data, and credentials tied to large enterprise clients.
Red Hat confirmed that attackers gained unauthorized access to a GitLab instance used by its consulting team but clarified that it was separate from the company’s main software supply chain. The firm stated that it has taken corrective steps and continues cooperating with authorities.
The group disclosed the breach on October 1, 2025, claiming the intrusion occurred in mid-September and accusing Red Hat of ignoring extortion demands after receiving a standard vulnerability disclosure response.
Leaked directory listings suggest exposure across sectors such as finance, telecom, healthcare, government, and defense. Named clients include Bank of America, AT&T, NASA, IBM, Cisco, Shell, and Boeing.
While the data’s authenticity is unverified, its size points to several years of consulting records. If genuine, it could support future targeting of affected organizations.
The incident coincides with an unrelated OpenShift AI flaw (CVE-2025-10725), though the overlap has intensified concerns about Red Hat’s internal security practices. Impacted entities are advised to audit consulting materials, reset credentials, and review configurations to minimize potential risk. (Anomali)
4. Discord Confirms Data Exposure Linked to Third-Party Vendor Breach
Discord reported a security incident involving its external vendor, 5CA, which manages customer support operations. The event did not compromise Discord’s internal infrastructure but did expose information from users who had interacted with the Customer Support or Trust & Safety teams.
Roughly 70,000 users worldwide were affected, and some of the leaked data included government ID images. Other potentially accessed details included names, usernames, email addresses, limited billing data such as payment type and the last four digits of cards, conversations with support agents, IP addresses, and certain internal training files. Passwords, complete credit card numbers, and user activity within Discord were not impacted.
After detecting the incident, Discord revoked 5CA’s system access, launched an internal investigation, engaged a digital forensics firm, and notified law enforcement and data protection authorities. The company is directly contacting impacted users via [email protected] and has warned the public that it will not reach out by phone or through other channels. The attackers appear to have targeted 5CA in an attempt to extort a ransom from Discord.
The company has since reviewed its security controls, strengthened monitoring of third-party access, and continues to audit external providers. Affected users are advised to stay cautious of phishing attempts and verify any communications about this incident come from official Discord sources only. (Discord)
Phishing remains one of the most common and effective cyber threats. Check out 200+ phishing stats that reveal how these scams evolve, who they target, and their growing global impact.
5. Williams & Connolly Breach Under FBI Investigation Amid China Hacking Claims
On October 7, 2025, the Federal Bureau of Investigation’s Washington field office launched an investigation into a series of cyber intrusions targeting major U.S. law firms, according to The New York Times. Sources familiar with the matter suggested that the attacks may be linked to Chinese threat actors, though the FBI has not yet confirmed attribution.
One of the affected firms, Williams & Connolly, acknowledged that hackers had gained access to portions of its computer systems through a zero-day vulnerability. The firm reported that a small number of attorney email accounts were compromised but emphasized there was no evidence that client files or confidential data stored in other parts of its IT infrastructure had been accessed or extracted.
Williams & Connolly stated that the attack has since been contained, the threat blocked, and no further unauthorized activity detected. The firm is continuing to assess its systems to confirm containment and safeguard sensitive information.
Neither the FBI nor the Chinese embassy in Washington responded to requests for comment. U.S. authorities have long accused China-linked actors of conducting cyber operations to obtain trade secrets and intellectual property from U.S. organizations, and this incident appears to fit that ongoing pattern of suspected espionage activity. (Reuters)
6. SonicWall Confirms Cloud Backup Breach Affected All Users of Service
SonicWall announced that every customer using its cloud backup service was affected by the breach. Attackers gained access to firewall configuration backup files stored in MySonicWall accounts, overturning earlier statements that suggested only part of the user base had been compromised.
MySonicWall, the portal used for managing licensing, product registration, firmware updates, and backups, was the main system targeted. On September 17, SonicWall advised customers to reset their credentials and strengthen defenses after discovering the intrusion.
A subsequent investigation with Mandiant confirmed that all cloud backup users were impacted. The exposed files contained AES-256-encrypted credentials and configuration data that could potentially be abused if decrypted.
SonicWall distributed a reset checklist instructing administrators to update passwords, shared secrets, VPN keys, API tokens, authentication servers, TOTP codes, and cloud edge API keys. Customers can check if their devices are listed as affected through MySonicWall under Product Management → Issue List.The company urged administrators to complete all remediation steps promptly, give priority to internet-facing firewalls, and keep monitoring MySonicWall for any new alerts. SonicWall also cautioned that delayed credential resets could continue to present a security threat. (SonicWall)
7. SimonMed Imaging Healthcare Data Breach Report
Date of Breach: October 10, 2025
SimonMed Imaging, one of the largest medical imaging providers in the United States, experienced a ransomware incident linked to the Medusa group. The breach surfaced after a vendor alert on January 27, 2025, followed by detection of unusual activity in SimonMed’s network the next day. Investigators later confirmed that attackers had exfiltrated data between January 21 and February 5. Medusa claimed responsibility, alleging theft of over 200 gigabytes of sensitive data.
The compromised information differs across patients and may include names, addresses, birth dates, service details, medical record numbers, diagnostic and treatment information, prescriptions, insurance data, and driver’s license numbers. The group also asserted access to ID scans, financial records, account balances, medical reports, and raw imaging files. Roughly 1.27 million individuals were affected, creating significant identity and privacy risks.
SimonMed now faces regulatory scrutiny, possible litigation, and heavy response costs. The organization reset credentials, enforced multi-factor authentication, strengthened endpoint monitoring, limited vendor access, reported the breach to authorities, and offered credit and identity protection services.
This case illustrates how weaknesses in third-party systems can lead to major data breaches. Strong access control, real-time exfiltration alerts, and regularly tested response procedures are key to minimizing future exposure. (Source: FOX News)
8. Massive Infostealer Log Exposes 183 Million Email Accounts
Date of Breach: October 21, 2025
A massive dataset known as “Synthient Stealer Log Threat Data” was added to Have I Been Pwned, containing about 183 million unique email accounts with passwords stolen from infected devices. This was not a breach of Google’s systems. Google confirmed there was no Gmail-specific hack and called reports suggesting otherwise inaccurate.

The exposed data includes email addresses, passwords, and login site metadata where the credentials were captured. Around 16.4 million of the exposed accounts had not appeared in previous leaks. Attackers can use these email-password pairs to attempt account takeovers, exploit reused credentials, and access mail or business systems tied to those accounts.
Google highlighted its automated protections and urged users to enable 2-Step Verification or passkeys. The key takeaway is that infostealers compromise data directly from user devices. Using unique passwords and multi-factor authentication remains critical to reducing risk from such leaks.
(Source: Forbes)
9. Volkswagen Confirms Security Incident Following 8Base Ransomware Claims
Volkswagen Group has confirmed a security incident after the 8Base ransomware group claimed to have stolen sensitive company data. The attackers allege they obtained invoices, receipts, accounting files, employee records, contracts, and confidentiality agreements.
According to 8Base, the data was taken in September 2024, suggesting the group had been holding the information for more than a year before making it public. Volkswagen stated that its core IT systems remain unaffected, hinting that the breach may have originated through a supplier or subsidiary rather than direct network access.
8Base, believed to be an offshoot of the Phobos ransomware operation, has been active since 2023 and is known for its double-extortion tactics—encrypting data while threatening to leak it unless a ransom is paid. The group has targeted more than 1,000 organizations, reportedly collecting around $16 million in ransom payments.
Earlier in 2025, authorities in Thailand arrested four Russian nationals linked to 8Base in a multinational law enforcement operation that seized 27 servers tied to the group. If verified, the Volkswagen breach could mark a shift in 8Base’s strategy, as it has typically focused on small and medium-sized businesses.
Volkswagen has not disclosed whether any personal or corporate data was exposed and continues to investigate the extent of the incident. (IT Pro)
10. UK Ministry of Defense Data Leak
The UK Ministry of Defence (MoD) is investigating claims that Russian-linked hackers accessed and leaked hundreds of sensitive military documents online. Reports suggest the stolen files detail eight Royal Air Force and Royal Navy bases, along with names and email addresses of MoD staff.
The breach appears connected to a ransomware attack on Dodd Group, a maintenance and construction contractor working with the MoD. The company confirmed an “unauthorized third party” had temporarily accessed part of its internal systems and that it is working with forensic specialists to assess the impact.

The Mail on Sunday, which first reported the incident, stated that the leaked data includes information on bases such as RAF Lakenheath in Suffolk, home to the U.S. Air Force’s F-35 fighter jets. The MoD said it is “actively investigating” and declined to release further details to protect sensitive operational information.
This incident adds to a string of recent MoD-related data breaches. Earlier in 2025, personal data belonging to Afghans evacuated to the UK was exposed through a subcontractor, and last year, serving military personnel had their information accessed in another significant breach. (BBC)
11. UK Watchdog Fines Capita £14 Million Over 2023 Data Breach
Capita has been ordered to pay £14 million after a major cyber incident exposed the personal details of millions across the UK. The Information Commissioner’s Office (ICO) said the firm’s weak security controls allowed hackers to access sensitive data belonging to around 6.6 million people.
The 2023 breach occurred when large volumes of unprotected files were left online, some of which later appeared on the dark web. The stolen material reportedly included home addresses, passport copies, and financial information.
Capita, which provides outsourcing services for both public agencies and private companies, confirmed that hundreds of pension schemes it manages were affected. The company said it has since reinforced its security systems and cooperated fully with regulators.
The ICO initially planned a £45 million penalty but lowered the amount after Capita took corrective action and supported affected individuals. Commissioner John Edwards said the exposure “could and should have been prevented,” emphasizing the importance of protecting personal data.
The fine follows a wave of high-profile UK breaches this year, underscoring growing pressure on organizations to tighten cybersecurity defenses. (BBC)
12. Kido Nursery Breach by Radiant
A cybercriminal group calling itself Radiant says it has deleted stolen photos and personal data of children after facing widespread condemnation for targeting nursery chain Kido Schools. The hackers had posted profiles and images of children on the dark web in an attempt to extort a ransom reportedly worth £600,000 in Bitcoin.
Public outrage quickly followed the release of the material, prompting the group to first blur the images and then remove all data. They later issued an apology, telling the BBC that “all child data is now being deleted.” Experts, however, doubt the claim, noting that ransomware gangs often promise to erase stolen data but keep or sell it later.
The hackers reportedly obtained access to Kido’s systems through an “initial access broker” who sold compromised employee credentials. Much of the stolen content came from Kido’s account on Famly, an early childhood education platform. Famly confirmed its own systems were not breached.
Kido said it had reported the incident to authorities and is working with cybersecurity specialists to investigate. The Radiant group, believed to be new and inexperienced, appears to have abandoned the extortion attempt entirely, losing the money paid to acquire system access.
Cybersecurity experts described the attack as “a new low,” with one analyst saying the group’s retreat was “driven by fear, not morality.” (BBC)
Data Breaches that Occurred in September 2025
1. Volvo Data Breach Linked to Miljödata Ransomware Attack
Volvo Group confirmed a significant data breach on 25 September 2025, following a ransomware attack on its Swedish HR software provider, Miljödata. The DataCarry ransomware group was identified as the perpetrator behind the incident, which began around 20 August 2025. Miljödata detected suspicious activity three days later and, after forensic analysis, confirmed that sensitive data had been stolen by early September. The breach occurred through the vendor’s systems rather than Volvo’s internal infrastructure.
The exposed information included employee first and last names and Social Security Numbers for some U.S. staff. From Miljödata’s wider client base, additional compromised data consisted of email addresses, government IDs, physical addresses, and dates of birth. Volvo clarified that no financial, payroll, or insurance data were affected.
Approximately 870,000 email records were leaked across Miljödata’s clients, with an undisclosed number of Volvo North America employees impacted. The exposed SSNs increased the risk of identity theft and fraud, raising regulatory and reputational concerns for Volvo.
In response, Volvo offered 18 months of free credit monitoring and identity protection to affected employees. The company reaffirmed that its internal systems remained secure, while Miljödata engaged forensic specialists, enhanced system monitoring, and began a comprehensive security review. Volvo also initiated a reassessment of vendor management practices to reduce third-party exposure in the future.
This breach illustrated a critical truth in cybersecurity: third-party risk is enterprise risk. Even when internal defenses are strong, vendor vulnerabilities can compromise sensitive information. Continuous vendor security assessments, strict access controls, and clear incident response agreements are essential to protect against cascading supply chain attacks. (Security Boulevard)
2. Gucci, Balenciaga, and Alexander McQueen Data Breach
Kering Group disclosed that a cyberattack in September 2025 exposed customer data from its luxury brands Gucci, Balenciaga, and Alexander McQueen. The hackers, known as Shiny Hunters, stole personal details including names, email addresses, phone numbers, home addresses, and spending totals from store transactions worldwide. While no credit card or banking information was taken, the inclusion of “Total Sales” data—showing individual purchases of up to $80,000—sparked concern that high-spending customers could face further targeting from scammers.
Shiny Hunters claimed responsibility for the breach, saying they accessed Kering’s systems months before and reached out in June with ransom demands in Bitcoin. Kering denied any form of negotiation and confirmed it had refused payment, citing long-standing advice from law enforcement. The company reported the breach to regulators and notified affected customers directly but withheld the total number of impacted individuals.
Investigators believe the attackers used stolen Salesforce credentials to gain temporary access to Kering’s systems—a tactic consistent with previous Shiny Hunters campaigns. The breach adds to a growing list of cyberattacks against luxury retailers in September, marking a tense period for the global fashion industry. (BBC)
3. Hackers Contact Harrods After 430,000 Customer Records Stolen in September Breach
Harrods confirmed that hackers reached out to the company after stealing data linked to 430,000 customer records in September 2025. The luxury retailer said the compromised information was obtained through a third-party provider and was limited to names, contact details, and marketing or loyalty card data. The company emphasized that no passwords, payment information, or order histories were exposed.
Harrods stated it refused to engage with the hackers and had reported the breach to authorities while notifying affected customers. The firm described the stolen data as “unlikely to be interpreted accurately” by unauthorized parties and said it continues to cooperate with investigators.
The incident follows an earlier hacking attempt on Harrods’ internal systems in May, which prompted temporary internet restrictions at its stores. Authorities arrested four individuals in July in connection with that earlier attack, which was linked to breaches at Co-op and M&S. The latest incident adds to a growing wave of cyberattacks on major UK businesses in 2025, including those that severely disrupted Co-op, M&S, and Jaguar Land Rover. (BBC)
4. Cyberattack on Collins Aerospace Disrupts Major European Airports
A major cybersecurity incident struck Europe’s aviation sector on 19 September 2025, disrupting operations at several major airports, including Heathrow, Brussels, and Berlin. The outage stemmed from a ransomware attack on Collins Aerospace’s passenger processing system, known as MUSE and vMUSE. Since this system is widely used across multiple airlines and airports, the attack spread quickly across borders and caused large-scale operational failures.
The attackers primarily aimed to disrupt systems rather than steal passenger information, but the compromised vendor network contained sensitive airline and airport data, raising potential exposure risks. Tens of thousands of passengers were stranded, and numerous flights were delayed or canceled as airports reverted to manual check-in and baggage handling.
The financial losses from flight disruptions were substantial, compounded by reputational harm and regulatory scrutiny over the impact on critical infrastructure. In response, airports implemented fallback processes to maintain limited operations while European cybersecurity authorities launched investigations into the attack and the threat actors involved.
This event underscored the dangers of third-party dependencies in aviation, revealing how a single vendor compromise can cripple an entire industry. It also reinforced the need for strong vendor risk management, resilience planning, and well-tested incident response measures. (Security Boulevard)
5. Wealthsimple Confirms September Cybersecurity Data Breach Exposing Client SINs and Financial Details
Wealthsimple confirmed a security breach in early September 2025 that exposed sensitive data belonging to fewer than one percent of its three million clients. The compromised information included Social Insurance Numbers, government-issued IDs, financial account numbers, and IP addresses. The company emphasized that no funds were stolen and all accounts remained secure.
According to Wealthsimple, the incident stemmed from a breach in third-party software used by the platform. The firm contained the issue within hours and launched a detailed investigation with external cybersecurity experts. Affected customers were notified directly by email, and anyone who did not receive communication was not impacted.
Wealthsimple apologized for the cybersecurity breach and announced that it would provide two years of free credit and dark web monitoring, along with insurance and identity theft protection for affected clients. The company said it has since strengthened its security systems to guard against similar incidents in the future. (CBC)
6. RatOn: New Android Trojan Automates Bank Transfers and Device Takeover
A new Android banking trojan called RatOn appeared in mid-July 2025 and is already considered one of the most advanced threats of its kind.
It spreads through adult-themed websites disguised as app installers, mainly targeting users in the Czech Republic and Slovakia. Once installed, it uses a dropper to load additional payloads, requests Accessibility and Device Administrator permissions, and secures full control of the device.

The malware goes beyond ordinary banking trojans. After gaining privileges, it installs a third module known as NFSkate, which was originally designed for NFC relay attacks. This gives attackers the ability to skim card data while also controlling the infected phone remotely. RatOn then automates fraudulent transactions against the Czech banking app George Česko.
It launches the app, simulates user actions like PIN entry, and executes unauthorized transfers. Commands are sent in JSON format, including recipient details, account numbers, and transfer amounts. Stolen PINs, usually gathered through phishing or overlays, allow these transfers to go through without the victim noticing.
Researchers noted that RatOn was written entirely from scratch, with no code borrowed from earlier malware families. Its ability to blend overlay attacks, NFC relay components, and automated transactions makes it highly dangerous. The trojan can also lock devices for ransom if direct fraud attempts fail, showing its operators’ intent to maximize profit from every infection.
7. Windows BitLocker Flaws Allow Privilege Escalation Through Memory Corruption
Microsoft has fixed two significant security flaws in its Windows BitLocker encryption feature. The vulnerabilities, tracked as CVE-2025-54911 and CVE-2025-54912, were disclosed on September 9, 2025, and rated “Important.” Both issues could allow an attacker with existing access to elevate their privileges to the SYSTEM level, giving them full control of the affected device.
The vulnerabilities are classified as Use-After-Free bugs, a type of memory corruption problem that occurs when software attempts to access memory that has already been freed. In this case, a malicious actor could manipulate the freed memory to execute arbitrary code. If successful, this would result in complete privilege escalation, enabling the attacker to install software, modify or delete data, and create accounts with unrestricted access.
Microsoft’s advisory notes that exploitation is considered “less likely,” and no active attacks have been reported. However, an attacker would need low-level access to the system and some form of user interaction to trigger the flaw, making it harder to exploit remotely. Still, the potential consequences remain serious once an attacker gains an initial foothold.
The vulnerabilities were patched as part of the September 2025 Patch Tuesday release. Microsoft strongly recommends that all users and administrators apply updates immediately to reduce risk. The discovery of CVE-2025-54912 was credited to Hussein Alrubaye, who worked with Microsoft’s security team. (Cybersecurity News)
8. Chrome Update Fixes Critical Remote Code Execution Vulnerability
Google has released an urgent security update for Chrome on Windows, Mac, and Linux to address a critical flaw that could allow attackers to run arbitrary code remotely. Users are urged to update immediately, as the fix is rolling out gradually but can also be applied manually through Chrome’s settings.

The patched version numbers include 140.0.7339.127/.128 for Windows, 140.0.7339.132/.133 for Mac, and 140.0.7339.127 for Linux. The most severe issue resolved is CVE-2025-10200, a use-after-free vulnerability in the Serviceworker component, reported on August 22, 2025, by security researcher Looben Yang. Exploiting this flaw could allow a malicious website to execute code on a victim’s system. Google rewarded Yang with a $43,000 bug bounty.
A second issue, CVE-2025-10201, was also patched. This high-severity vulnerability stems from an inappropriate implementation in Mojo, a library set handling inter-process communication. Reported on August 18, 2025, by Sahan Fernando and an anonymous researcher, the flaw carried a $30,000 bounty. Exploitation of this bug could weaken Chrome’s sandbox protections.
Google has withheld full technical details until most users apply the update to reduce the risk of active exploitation. The company advises users not to delay updating their browsers to stay protected against potential attacks. (Cybersecurity News)
9. Elastic Security Incident Tied to Salesloft Drift Cybersecurity Breach Exposes Email Account
Elastic has confirmed a security incident linked to the Salesloft Drift cybersecurity breach disclosed on August 26, 2025. The compromise allowed unauthorized access to one internal email account that contained valid credentials, though the company emphasized that its Salesforce environment was not affected.
An internal investigation revealed that the exposed account was connected through the Drift Email integration. The breach may have given a threat actor read-only access to emails in that inbox. A review of its contents uncovered a small number of messages containing potentially valid credentials. Elastic notified affected customers directly through its support channels, clarifying that those not contacted were not impacted.

Upon learning of the third-party breach, Elastic’s security team disabled all Drift integrations, reviewed logs and network activity, and coordinated with Drift’s security staff. The company also monitored intelligence feeds for indicators of compromise while reaffirming its commitment to protecting customer data.
This incident is part of a wider supply chain attack stemming from Drift, which has impacted several major organizations. Confirmed victims include Palo Alto Networks, Zscaler, Google, Cloudflare, PagerDuty, Tenable, Qualys, and Dynatrace. Each of these companies has reported varying levels of data exposure, often involving business contact details, sales records, or limited customer information. (Cybersecurity News)
10. Stellantis Confirms Customer Data Exposed in Salesforce-Linked Cyberattack
On 24 September 2025, automotive giant Stellantis confirmed a data breach affecting its North American customer service operations. The incident stemmed from a compromise of the company’s Salesforce instance, where attackers gained unauthorized access through a third-party connected app.
According to Stellantis, the hackers obtained customer contact information but did not access financial or highly sensitive personal data. The company stated that it immediately activated its incident response protocols, launched a full investigation, and began notifying affected individuals and authorities. Customers were urged to stay alert for phishing attempts and verify any communications through official channels.
Cyber intelligence sources attribute the attack to the hacking group ShinyHunters, which has recently been linked to similar Salesforce-related cybersecurity breaches impacting Google, Adidas, Allianz Life, and Farmers Insurance. Researchers believe the group exploited stolen OAuth tokens from integrations like Salesloft’s Drift AI chat tool, using them to exfiltrate data from multiple Salesforce environments.
This campaign represents part of a broader wave of attacks using social engineering to trick employees into approving malicious third-party apps within Salesforce. The FBI has issued a flash warning outlining indicators of compromise for organizations that suspect infiltration.
Salesforce has clarified that its core platform remains secure and was not directly compromised. However, experts continue to emphasize that administrators must audit connected apps, restrict user permissions, and regularly monitor integrations to prevent similar attacks. (Salesforceben)
Data Cybersecurity Breaches that Occurred in August 2025
1. Google’s Salesforce Data Breach – Asks 2.5B Users to Update Their Passwords
Google has issued an urgent warning to more than 2.5 billion Gmail users after a breach connected to a Salesforce cloud system exposed account information and fueled a rise in phishing and credential theft attempts. Hackers are using fake login pages and fraudulent calls to trick people into giving up their details, and Google stressed it never contacts users to ask for passwords.

The company urged users to change their Gmail password immediately and to enable two-factor authentication for stronger protection. Passkeys, which replace traditional passwords, were also recommended as a safer login option. Users are advised to watch for suspicious activity in their accounts and to remain cautious of messages or calls pretending to be from Google.
Updating a Gmail password is simple. On desktop, users can sign in, go to “Manage your Google Account,” open the security section, and reset their password under “Signing in to Google.” The Gmail app on mobile devices follows the same process. If a password is forgotten, Google’s recovery flow can send reset instructions to a backup email or phone.
Google also encouraged better security habits, including the use of long, complex, and unique passwords, password managers for storage, and regular reviews of recovery details and connected apps. The alert serves as a reminder that individual action remains essential to defending against large-scale cyber threats. ( Trend Micro)
2. TransUnion Data Breach Exposes 4.4 Million Americans’ Sensitive Information
On 28 July 2025, credit reporting agency TransUnion suffered a major data breach linked to a third-party application, exposing the personal information of 4,461,511 individuals. The incident was discovered on 30 July, and the company began notifying affected customers in late August.
While credit reports and core credit files were not compromised, attackers accessed names, dates of birth, Social Security numbers, billing addresses, phone numbers, and email addresses. Security experts believe the extortion group ShinyHunters carried out the attack, likely through third-party integrations or OAuth-connected apps disguised as Salesforce tools.
This method allowed persistent access to customer records and ties the incident to a broader extortion-as-a-service campaign. Experts note that the exposure of Social Security numbers makes this breach far more damaging than many other recent incidents, heightening the risk of identity theft and financial fraud.
TransUnion, which manages financial data for over 260 million Americans, is offering affected customers two years of free credit monitoring and identity theft protection. At least one law firm has already begun investigating the breach, with the possibility of a class action lawsuit.
3. Connex Credit Union Data Breach Affects 172,000 Individuals
Connex Credit Union, serving more than 70,000 members and managing assets exceeding $1 billion, disclosed a cybersecurity breach that compromised the personal data of 172,000 individuals. The breach was detected on June 3, with investigations showing that attackers accessed Connex systems between June 2 and June 3.
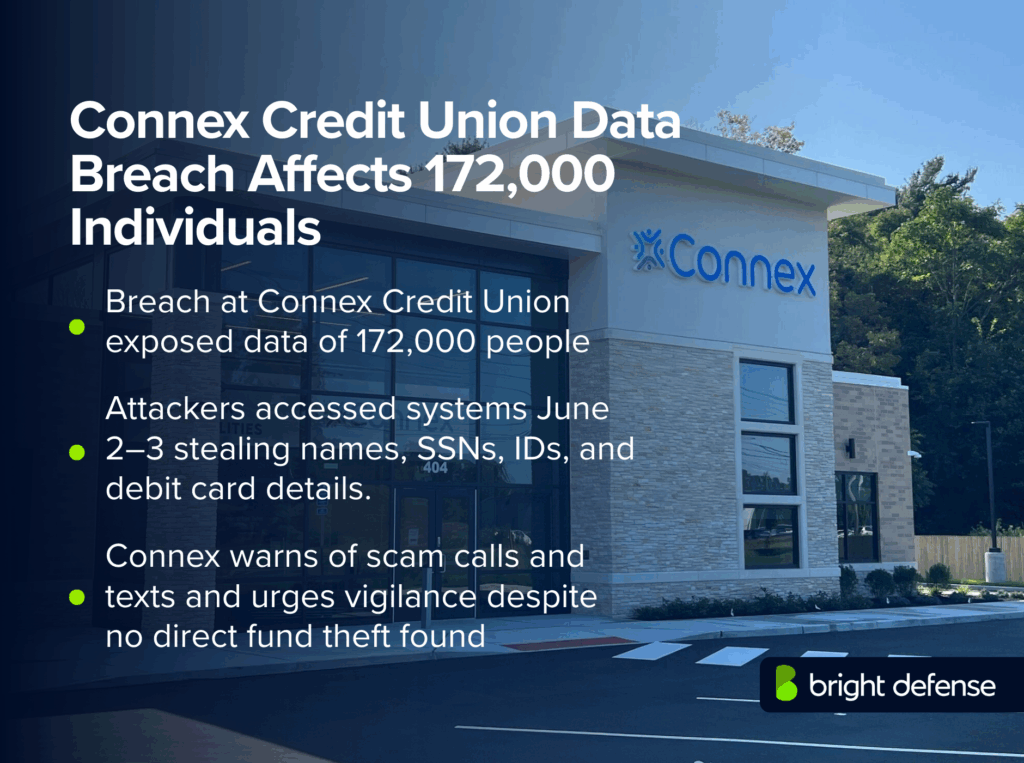
Files potentially stolen during the intrusion contained names, account numbers, debit card details, Social Security numbers, and government-issued IDs used for account openings. Connex stated that there is no evidence of unauthorized access to member accounts or funds at this time.
The Maine Attorney General’s Office confirmed receiving a copy of the notification letter being sent to those affected. In addition, Connex has posted an alert on its website warning customers of scam calls and text messages impersonating employees to obtain PINs, passwords, and account information, though it is unclear whether these scams are directly tied to the breach.
The identity of the attackers remains unknown, and no threat group has publicly claimed responsibility. It also has not been confirmed whether this incident involved ransomware.
4. Manpower Data Breach Linked to Ransomware Impacts 140,000 Individuals
Manpower, a staffing and recruiting firm based in Lansing, Michigan, confirmed that a ransomware attack led to the compromise of personal information belonging to approximately 140,000 individuals. The breach came to light during an investigation into an IT outage on January 20, 2025, which revealed that hackers had accessed the company’s systems between December 29, 2024, and January 12, 2025.
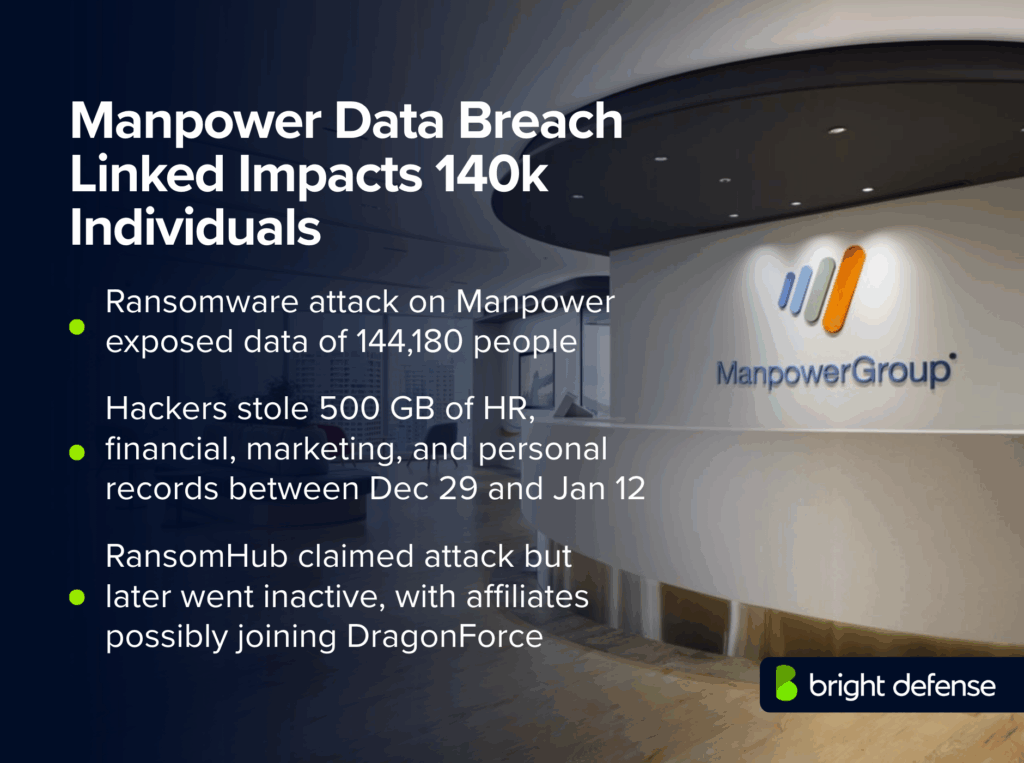
According to a notice filed with the Maine Attorney General, data from 144,180 people was affected. The stolen files contained personal information, and Manpower is offering impacted individuals free credit monitoring and identity theft protection services.
The RansomHub ransomware group claimed responsibility, listing Manpower on its leak site on January 22 and asserting it had stolen 500 GB of data. Samples published by the group included HR, financial, marketing, and corporate documents, along with databases containing sensitive personal details.
RansomHub’s activity has since subsided, with no updates on its leak site after April 2025. Reports suggest that its affiliates may have been absorbed into the DragonForce group, raising concerns about the continuity of stolen data operations under a different banner.
5. Orange Telecom Data Breach Tied to Ransomware, Customer Data Posted Online
French telecommunications giant Orange SA confirmed a ransomware attack that led to the theft and publication of business customer data on the dark web. The incident, reported to national authorities at the end of July, involved ransomware linked to a group calling itself Warlock. About 4 gigabytes of data were released online in mid-August.
According to Orange, the attackers gained only limited access to internal systems and were able to exfiltrate outdated or low-sensitivity data. Affected companies were informed in advance, and Orange stated that it has been working closely with them and relevant authorities since the discovery of the breach. The company declined to comment on the ransomware group itself or on whether other organizations were impacted.
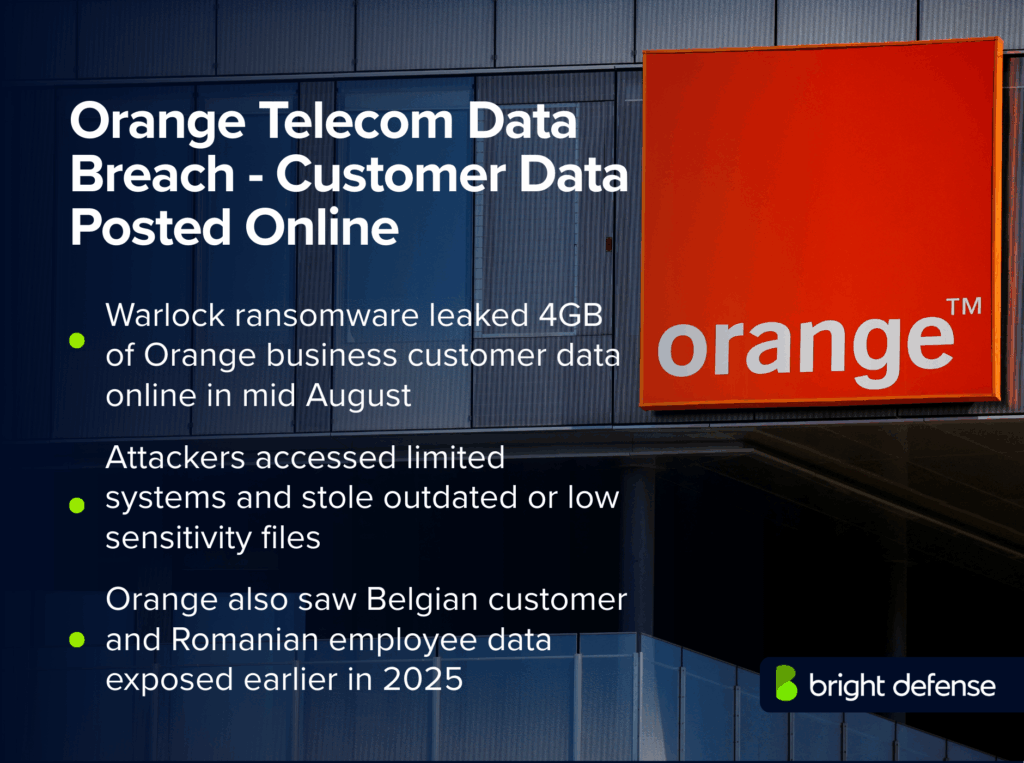
Warlock operates as a ransomware-as-a-service model, leasing its tools to other hacker groups who then lock systems and demand payments. The Orange breach adds to a string of security incidents targeting the telecom provider in 2025. In July, customer data from its Belgian division was exposed in a separate compromise, and earlier in the year, employee data from its Romanian operations surfaced on the dark web.
Telecommunications companies continue to face intense pressure from cybercriminals due to the sensitive nature of the financial, governmental, and business information they handle. Orange’s repeated targeting this year highlights both the scale of the threat and the challenges in protecting critical communications infrastructure.
6. Air France and KLM Report Third-Party Platform Cybersecurity Breach News Impacting Customer Data
On August 7, 2025, Air France and KLM informed customers of a possible security incident connected to a third-party customer support tool both carriers use. The breach could have exposed passenger names, contact details,

Flying Blue loyalty numbers, and the subject lines of service request emails. According to the airlines, no passwords, passport data, payment card details, itineraries, or loyalty point balances were affected.
Travelers have been urged to stay alert for phishing attempts through phone calls or email. Authorities in France and the Netherlands have received official notification of the incident. While the vendor’s name remains undisclosed, early signs suggest the cybersecurity breach is part of a broader series of attacks on external CRM platforms.
Investigations from cybersecurity analysts indicate links to a campaign targeting Salesforce environments. The hacking group ShinyHunters has claimed responsibility, with some intelligence hinting at cooperation between ShinyHunters and Scattered Spider, a group recently focused on airline targets. Their tactics rely heavily on phishing and social engineering schemes, rather than exploiting vulnerabilities in Salesforce technology itself. (Caliber)
Cyber threats keep rising across every sector. Explore 200 cybersecurity stats that highlight attack trends, financial impact, and how organizations are responding to defend against evolving risks.
7. Microsoft Teams Vulnerability Could Let Attackers Access and Alter Messages
On August 12, 2025, Microsoft disclosed a critical security flaw in its Teams collaboration platform during the August Patch Tuesday release. Tracked as CVE-2025-53783, the heap-based buffer overflow vulnerability could allow an attacker to execute code remotely and gain the ability to read, write, and delete messages and other user data.

The flaw carries a CVSS 3.1 score of 7.5 and is rated “Important.” Exploitation would require a complex attack chain and user interaction, such as clicking a malicious link or opening a specially crafted file. Microsoft stated that the vulnerability has not yet been publicly disclosed or exploited, and its exploitability is considered “Less Likely.”
A successful attack could severely impact confidentiality, integrity, and availability of Teams data. The issue was one of 107 vulnerabilities patched in August, which also included a fix for a Windows Kerberos zero-day.
Microsoft has released a security update to address the flaw and urges all Teams users and administrators to apply it promptly. Security experts warn that vulnerabilities in messaging platforms have the potential for large-scale compromise, and organizations should treat this patch as a high priority. (Cybersecurity News)
Cybercrime is expanding faster than ever. Check out 250+ cybercrime stats that reveal how attacks spread, the industries most affected, and the rising costs linked to digital crime.
8. Workday Discloses Data Breach After Salesforce Attack ( 18 August 2025)
HR software provider Workday confirmed a data breach tied to a recent wave of attacks targeting Salesforce CRM systems. The breach, discovered on August 6, exposed business contact information such as names, email addresses, and phone numbers. Workday emphasized that customer tenants and their data were not impacted.

The attack stemmed from a social engineering campaign where threat actors impersonated HR or IT staff, contacting employees by phone or text to trick them into granting access. The attackers gained entry to Workday’s third-party CRM platform, not its core systems.
Although Workday did not directly name the group, security researchers linked the incident to ShinyHunters, which has run similar attacks against major companies including Adidas, Qantas, Allianz Life, Dior, Chanel, and Google. The group tricks employees into connecting malicious OAuth apps to Salesforce, then steals CRM data for extortion.
Workday described the exposed information as commonly available contact details, but acknowledged that it could be abused in further phishing campaigns. (Bleeping Computer)
9. Windows 11 24H2 Update Linked to Drive Failures and Data Loss
The Windows 11 24H2 security update (KB5063878), part of Microsoft’s August Patch Tuesday rollout, is creating serious storage problems.

Reports indicate that after installation, some SSDs and HDDs no longer appear in Windows, and in certain cases files become corrupted. Failures occur most often during heavy write activity, such as large game updates, with one example involving Cyberpunk 2077.
This update included a Defender fix designed to stop the Lamma stealer malware in Windows ISO builds. While Microsoft resolved an installation error tied to the patch (0x80240069), the storage malfunction remains unresolved.
Until an official correction is issued, security experts recommend holding off on KB5063878, maintaining regular backups, and avoiding risky large transfers on systems where the patch has already been applied. ( Cybersecurity News )
10. Apache Tomcat Vulnerabilities Allow DoS Attacks
Researchers disclosed a high-severity flaw in Apache Tomcat’s HTTP/2 implementation (CVE-2025-48989), known as the “Made You Reset” attack. The issue affects Tomcat versions 11.0.0-M1 to 11.0.9, 10.1.0-M1 to 10.1.43, and 9.0.0.M1 to 9.0.107, as well as some older unsupported releases.

The vulnerability lets attackers abuse HTTP/2 stream resets to exhaust server memory, often causing OutOfMemoryErrors and denial-of-service conditions. Thousands of web applications worldwide could be at risk if HTTP/2 is enabled.
The Apache Software Foundation has issued fixed releases: Tomcat 11.0.10, 10.1.44, and 9.0.108. Administrators are urged to upgrade immediately and apply temporary mitigations such as rate limiting and monitoring for abnormal memory use. (Cybersecurity News)
Also read: Data Breach Prevention Tips for Multinational Companies
Cybersecurity Data Breach News for July 2025
1. Allianz Life Data Breach Exposes Most US Customer Records
Hackers accessed a third-party cloud-based CRM system used by Allianz Life Insurance Company of North America on July 16, 2025. The breach exposed personal data for most of Allianz Life’s 1.4 million customers, as well as information on financial professionals and some employees.

The attack used social engineering techniques to gain access. Allianz reported the incident to the FBI and stated there is no evidence of intrusion into its core systems, including its policy administration platform.
Allianz, which serves 125 million customers worldwide, is contacting affected individuals and providing assistance. The breach impacts only Allianz Life in the US. (BBC)
2. Moviynt Data Breach Exposes Personal Information – July 8
Moviynt disclosed a data breach involving unauthorized access to employee email accounts and files between February 27 and March 6, 2025. The breach exposed names and Social Security numbers of affected individuals.

The company launched an investigation with cybersecurity experts and began notifying individuals on July 8, 2025, including filing a notice with the New Hampshire Attorney General.
Law firm Levi & Korsinsky, LLP is investigating potential compensation claims for those impacted. Individuals who received a notice may be eligible for reimbursement related to identity theft or fraud risks caused by the breach. (Source: CNY Homepage)
3. British Spies and SAS Exposed in Afghan Data Breach
A major data breach has exposed the identities of over 100 UK personnel, including MI6 officers and special forces, along with the personal information of nearly 19,000 Afghans who worked with British forces. The breach, which occurred in February 2022 but wasn’t discovered until August 2023, involved a mistaken email from UK Special Forces HQ that shared sensitive data on over 30,000 Afghan relocation applicants.

Among the leaked data were classified case notes, which compromised security service personnel and put Afghan partners at risk of Taliban reprisals. One Afghan individual who obtained the data posted part of it on Facebook and was later granted expedited entry into the UK — a move government sources described as “essentially blackmail.”
The UK Ministry of Defence set up a covert Afghanistan Response Route (ARR) following the breach. The program has since resettled 4,500 people, with another 2,400 expected, at a cost of £850 million.
The breach was kept secret under a super-injunction, which was partially lifted in July 2025, allowing the BBC and others to report the incident. The Ministry of Defence called it a “serious departmental error” but has not confirmed if anyone was harmed due to the leak. Family members of named Afghans said Taliban interest in them intensified after the data surfaced. ( Source: BBC )
4. Dell Data Breach: World Leaks Publishes 1.3 TB of Files
The World Leaks extortion group has leaked 1.3 terabytes of data allegedly stolen from Dell Technologies. The breach impacts Dell’s Customer Solution Centers, which host product demos and internal testing tools.

Dell confirmed that the accessed system is isolated from customer and partner networks and emphasized that the stolen data is “primarily synthetic, publicly available, or Dell systems/test data.” The company says no sensitive customer or corporate data appears to be involved.
What’s in the Leak?
- 416,103 files are now public on the World Leaks site
- File types include employee folders, backup data, software tools, and infrastructure scripts
- Mentions of Dell products (e.g., PowerPath, PowerStore) and VMware tools, with Terraform and automation scripts
- Structured naming patterns suggest real internal systems were involved
Formerly known as Hunters International, World Leaks appears to be dropping traditional ransomware tactics in favor of direct data leaks, bypassing encryption and ransom negotiations.
This incident follows a 2024 Dell breach that exposed personal data from over 10,000 employees. Investigations into the current breach are ongoing, and no ransom demands have been confirmed. (Source: Tech.co)
5. Tea Dating App Data Breach Exposes Over 1 Million Private Messages
The Tea anonymous dating advice app has suffered a data breach far larger than initially reported. The incident involved access to more than 1.1 million private direct messages exchanged between users from February 2023 to July 2025. These messages contained highly sensitive conversations on topics such as divorce, abortion, cheating, and rape. Some chats even included phone numbers and meetup locations.
Previously, Tea confirmed that 72,000 images, including profile photos and driver’s licenses, had been exposed. A security researcher, Kasra Rahjerdi, discovered the messages while investigating the app’s data security. He stated that while Tea’s own API had strong protections, its use of Firebase to store data created vulnerabilities that allowed access to real-time private communications until July 26, 2025.
Tea has since taken the affected systems offline and temporarily disabled its direct messaging feature. The company is working with external cybersecurity experts and the FBI to investigate the incident. It has also informed affected users and will provide free identity protection services.
Despite the breach, Tea remains popular, holding the number two position on the Apple App Store and maintaining a community of over 4.6 million women. The app, which allows anonymous reviews of men, also offers dating advice and tools such as background checks. (Business Insider)
Data Breaches that Occurred in June 2025
1. 16 Billion Passwords Exposed in the Largest Data Breach in the Ever!
A massive data breach has exposed 16 billion login credentials across over 30 separate datasets. The leaked information includes usernames, passwords, tokens, cookies, and metadata linked to services such as Facebook, Google, Apple, GitHub, and Telegram. The data likely came from infostealer malware and is mostly recent.

The datasets ranged from 16 million to more than 3.5 billion records each, averaging around 550 million. Some filenames suggested ties to specific platforms or regions. Researchers noted this is not old data being reused, but fresh credentials that could lead to account takeovers, phishing, or business email compromise.
Some of the leaked session cookies may allow attackers to bypass two-factor authentication. While there’s no evidence of direct hacks into major companies, stolen credentials tied to login pages for major services were present in the datasets.
Users are urged to change passwords, enable multi-factor authentication, and watch for suspicious activity. This breach is among the largest ever recorded and underscores the ongoing threat posed by infostealer malware.
2. Cambodian Hacktivists Target Thai Government Sites – June 2025
A Cambodian hacktivist group calling itself AnonsecKh (also known as Bl4ckCyb3r on Telegram) has claimed responsibility for at least 73 cyberattacks on Thai organizations, following a May 28 border clash that left one Cambodian soldier dead. The campaign escalated tensions in a decades-long territorial dispute over land near the Preah Vihear Temple, a UNESCO site the UN’s International Court of Justice has repeatedly ruled belongs to Cambodia.
According to cybersecurity firm Radware, the group has conducted distributed denial-of-service (DDoS) attacks and website defacements, primarily targeting Thai government and military domains. More than 25% of their targets have been Thai manufacturing firms.
Between June 4 and June 10, the group claimed attacks on Thailand’s Ministry of Defense, Ministry of Foreign Affairs, and Bangkok Metropolitan Administration, according to Hackmanac.
The activity surged after a June 6 statement from the Thai army announcing readiness for “a high-level military operation.” Thai authorities have since confirmed that arrest warrants were issued for two suspected members of the group, as investigations continue. ( The Record )
3. UNFI Cyberattack Disrupts Grocery Supply Chain – June 2025
United Natural Foods Inc. (UNFI), the main distributor for Whole Foods and supplier of over 250,000 grocery products, confirmed a cyberattack in June 2025 that forced a full network shutdown. The incident, disclosed in its Q3 earnings report, continues to disrupt fulfillment and supply operations.
CEO Sandy Douglas said UNFI is “safely bringing systems back online” and shipping to customers “on a limited basis.” The company’s external-facing systems—including supplier web portals and VPN tools—remain offline. UNFI has not shared details on the attack type or responsible party.
A vendor reported their Whole Foods product launch was stalled due to delivery issues and lack of communication. Some stores are seeing empty shelves, though it’s unclear if the cause is directly linked to the breach. Whole Foods said it is restocking quickly and referred all questions to UNFI.
UNFI reported $8.1 billion in net sales for the quarter ending May 3, 2025, and expects a drop in earnings after losing a key regional contract. The financial outlook remains unchanged pending a full review of the attack’s impact. (Sources: TechCrunch )
4. Sepah Bank Cyberattack Linked to Iran-Israel Escalation
Sepah Bank, one of Iran’s major state-owned financial institutions, suffered a cyberattack in June 2025 amid active military and cyber clashes between Iran and Israel following recent strikes and retaliations on both sides.
The Fars news agency reported that the attack targeted the bank’s infrastructure, disrupting online services, though officials expected to restore full service within hours.

An Israel-linked hacking group known as Predatory Sparrow (Gonjeshke Darande) claimed responsibility, stating it had “destroyed” bank data during the incident. Predatory Sparrow has previously conducted destructive operations against Iranian infrastructure.
While officials confirmed the disruptions, they have not disclosed whether sensitive data was permanently lost. Customers faced temporary outages, and authorities have not advised any further action. (Al Jazeera)
5. Cash App Settlement Payment Update
Cash App is distributing payments to users affected by two major data breaches. As part of a $15 million class action settlement approved in January 2024, eligible users could receive up to $2,500 for out-of-pocket losses and an additional $75 for time spent dealing with the aftermath.
The first breach occurred in April 2022 when a former employee accessed sensitive data on over 8 million users. A second breach followed in October 2023 involving unauthorized transactions and failed customer support. The lawsuit accused Cash App and its parent company Block Inc. of negligence and poor data protection.
Claimants needed to submit documentation by November 18, 2024 showing unauthorized access or financial loss between August 2018 and August 2024. Payments are being sent out by direct deposit or check and are expected to be completed before the end of 2025.
If you filed a claim and haven’t received payment or an update, check your email or contact the settlement administrator. This case highlights how quickly data can be exposed and how long recovery takes. (Coaches Database)
Data Breaches that Occurred in May 2025
1. Massive Data Google & Apple Breach Exposes 184 Million Passwords
Over 184 million login credentials tied to Google, Apple, Microsoft, Facebook, Instagram, Snapchat, and other platforms were exposed in a major data breach, according to the New York Post. Cybersecurity researcher Jeremiah Fowler found the database sitting online without encryption or any password protection. Anyone could access it.
The database held exactly 184,162,718 unique usernames and passwords. Fowler believes the data came from infostealer malware, which rips sensitive information from infected devices. That includes browser logins, cookies, autofill details, emails, and messaging apps.

Snapchat claimed it found no signs of a breach on its own systems. But Fowler verified the data by contacting people listed in the dump. Many said the leaked credentials were accurate.
After Fowler reported the issue, the hosting provider took the database offline. No one knows who owned it or whether it was leaked by mistake or dumped intentionally.
Fowler warned that email accounts often store tax documents, contracts, medical records, and other personal files. He recommended deleting old sensitive messages and using encrypted storage for sharing important files.
Bottom line: change your passwords, turn on multi-factor authentication, and don’t trust your inbox to protect your private data. (New York Post)
2. TeleMessage Breach: Private Communications of US Officials Exposed
A covert communication app used by US government officials to archive encrypted messages has been compromised. The app, a customized version of Signal created by Israeli company TeleMessage, was intended to meet federal archiving requirements. However, a hacker gained access to an AWS-hosted server within 20 minutes and exposed unencrypted data intended for archiving.

The breach revealed names, message fragments, and contact information of US government personnel. The attacker also found plaintext credentials for the backend admin panel and accessed a list of registered users, many of whom had .gov email addresses. TeleMessage has since removed public documentation and videos describing the service. The company did not receive a direct vulnerability disclosure from the hacker, who instead contacted 404 Media. (404 Media)
3. SogoTrade Data Breach
SogoTrade, Inc., an online brokerage firm headquartered in Chesterfield, Missouri, announced a data breach affecting its clients. The breach occurred in May 2024 and was publicly disclosed in May 2025. The compromised information includes names, financial account numbers, Social Security numbers, and tax identification numbers. SogoTrade has begun notifying affected individuals about the breach. (GlobeNewswire)
4. SAP NetWeaver Breach: 581 Critical Systems Compromised by China-Linked APTs
Multiple China-based threat groups have exploited a recently disclosed vulnerability in SAP NetWeaver (CVE-2025-31324) to breach at least 581 critical systems globally. The flaw allows unauthenticated file uploads and remote code execution. Targets include infrastructure operators in the UK and US, such as gas, water, and medical manufacturing sectors, as well as Saudi government ministries.

Dutch cybersecurity firm EclecticIQ attributed the attacks to groups UNC5221, UNC5174, and CL-STA-0048. Attackers deployed web shells, reverse shells, and malware such as PlugX, KrustyLoader, SNOWLIGHT, VShell, and GOREVERSE. An exposed server tied to the campaign contained event logs and targeting lists, revealing both compromised assets and future plans.
SAP patched the flaw in May 2025. Security experts urge immediate updates to NetWeaver systems amid ongoing active exploitation and the discovery of an additional vulnerability, CVE-2025-42999, affecting the platform’s Visual Composer Metadata Uploader. (The Hacker News)
5. PowerSchool Breach: Data of 62.4 Million Students Exposed
PowerSchool, a major K-12 education tech provider, suffered a data breach in December 2024 affecting 62.4 million students and 9.5 million educators. The company paid a ransom to prevent the release of sensitive data, but hackers have resumed extortion attempts as of May 2025.
Hackers are now emailing school officials across the U.S. and Canada, demanding bitcoin payments. Exposed data includes Social Security numbers, medical records, and special education information.
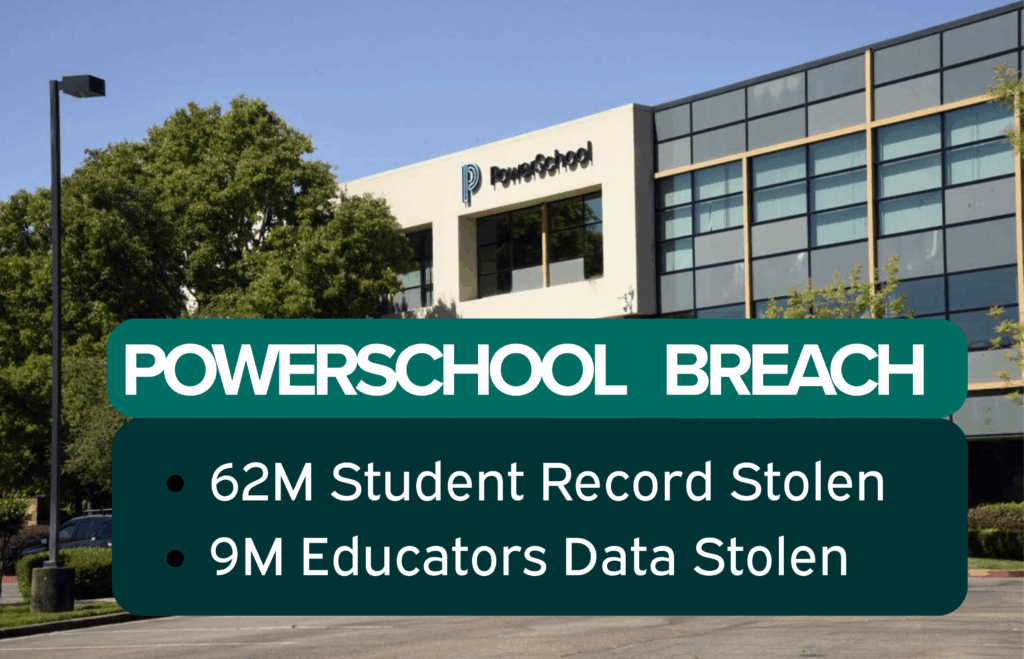
In North Carolina, staff from at least 20 school districts received threats. The state plans to stop using PowerSchool in July and switch to Infinite Campus due to security concerns. PowerSchool confirmed that the attackers did not honor the original agreement to delete stolen data. Law enforcement in the U.S. and Canada is investigating. (The 74 Million)
6. Vastaamo Data Breach: Second Suspect Named
Finland’s National Bureau of Investigation (NBI) has named a second suspect in the 2020 Vastaamo data breach. The suspect, based in Estonia, is accused of helping prepare extortion materials and posting stolen patient data online. They are not charged with targeting victims directly. The NBI worked with Estonian authorities and plans to submit the case to prosecutors on May 19, 2025.
This follows the April 2024 conviction of Aleksanteri Kivimäki, who received a 6-year, 3-month prison sentence. He was arrested in February 2024 in Helsinki. Around 9,000 victims have been contacted. No further action is required from those who already submitted claims during the earlier investigation. The breach exposed sensitive mental health records after Vastaamo’s database was hacked in 2020. The company’s CEO was removed shortly after the incident. (Daily Finland)
7. M&S Data Breach: Customer Information Compromised in April 2025 Cyberattack
Marks and Spencer (M&S) has confirmed a cyberattack that occurred in April 2025, exposing customer data. While payment details were masked and not usable, the breach involved basic contact information, dates of birth, order histories, and possibly reference numbers tied to M&S credit card and Sparks Pay accounts.
Customers have been prompted to reset passwords upon their next login. The attack caused disruptions to online purchases and affected store inventories. M&S joins Harrods and Co-op as part of a broader campaign targeting UK retailers. Scattered Spider has been linked to the attacks, though a group known as DragonForce also claimed responsibility.
The UK’s National Cyber Security Centre is working with impacted companies to assess the intrusions. M&S has advised customers to stay alert for phishing attempts and fraudulent communications. Despite the lack of usable card data, security experts warn that personal information from the breach could be misused. (Cybersecurity Dive)
8. Capital One Data Breach Settlement (2025 UPDATE)
In 2019, Capital One experienced a major data breach that exposed the personal information of more than 100 million U.S. customers and an additional 6 million in Canada. The breach was caused by a misconfigured firewall in their cloud setup, not by a sophisticated cyberattack. The attacker was able to access names, addresses, social security numbers, credit scores, and linked bank account details.
The root cause was a simple configuration error. Capital One failed to restrict access properly, leaving sensitive cloud storage vulnerable. There were no enforced VPN requirements, no static IP allowlisting, and no real-time access monitoring in place at the time of the breach.
The resulting class-action settlement totaled $190 million. It applied to individuals who applied for a Capital One credit card between 2005 and early 2019 and who filed claims before the 2022 deadline. Compensation includes up to $25,000 for documented identity theft expenses, payment for up to 15 hours of time spent dealing with the aftermath, and access to free identity protection services.
The court granted final approval in late 2023. Payouts began in early 2024 and are continuing in waves throughout 2025. The claim portal is now closed, but those who submitted claims can still check their status using their confirmation number.
For businesses, this incident is a clear example of how a single overlooked security measure can lead to massive financial and reputational damage. Capital One could have avoided this breach with stricter access controls, isolated cloud environments, static IP restrictions, and basic logging and alerting practices. (Pure VPN)
Compliance plays a key role in protecting data and reducing risk. Explore 150 compliance stats that show how organizations handle regulations, audits, and the growing pressure to stay secure and compliant.
Data Breaches That Occurred in April 2025
1. Insignia Expand Hack Exposes 100 Accounts
Breach Disclosed: 04 Apr, 2025
Insignia Financial disclosed suspicious login activity against its MLC Expand Wrap Platform on 04 Apr, 2025, after credential stuffing produced an unusual volume of login attempts. The company said about 100 customer accounts showed suspicious access, with no financial loss observed during the review.
Insignia restricted certain platform actions as a precaution, increased monitoring, and began contacting impacted customers and advisers. Some users were prompted to reset passwords at next sign in, and the firm advised use of strong, unique passphrases and avoidance of credential reuse across services. Insignia reported no similar activity on other customer facing platforms.
Public reporting through February 21, 2026 shows no new Insignia Financial data breach disclosure in 2026 and no updated impact figures beyond the April 4, 2025 credential stuffing incident on the MLC Expand Wrap Platform. Insignia’s January 22, 2026 quarterly business update and its February 19, 2026 half year results announcement do not reference a new cybersecurity incident or a revised scope for the 2025 event.
Source: Insignia Financial ASX release.
2. DBS Group and Bank of China (Singapore)
A ransomware attack on Toppan Next Tech (TNT), a third-party data vendor, potentially compromised customer information from Singapore’s DBS Group and the Bank of China (BoC) Singapore branch. DBS reported that approximately 8,200 client statements might have been exposed, mainly affecting its trading platform DBS Vickers and cashline loan accounts.

BoC disclosed that data from around 3,000 customers, used in printed correspondence managed by TNT, were potentially compromised. The leak possibly includes names, addresses, and loan account numbers. Both banks emphasized that their core systems, customer deposits, and monies remain secure. (Reuters )
3. NationsBenefits Holdings Data Leak
NationsBenefits Holdings, a HIPAA business associate, reported a data breach impacting over 3 million individuals.
The breach was part of a data theft and extortion attack by the Clop ransomware group, exploiting vulnerabilities in the Fortra GoAnywhere MFT solution. The compromised data included protected health information (PHI). (HIPAA Journal)
4. Evide
Evide, a data storage company based in Northern Ireland, suffered a ransomware attack that compromised data from approximately 140 organizations, including charities supporting survivors of sexual abuse.
The breach exposed personal data such as phone numbers and email addresses. Investigations were conducted by the Police Service of Northern Ireland and the Garda National Cyber Crime Bureau.( Wikipedia)
5. Consumer Financial Protection Bureau (CFPB)
The CFPB experienced a significant security breach when a former employee transferred confidential information on approximately 256,000 consumers and 45 financial institutions to their personal email account.
The unauthorized transfer involved personally identifiable information (PII) of consumers. The breach was disclosed to the public on April 24, 2023. (Wikipedia)
6. 23andMe
Genetic testing company 23andMe disclosed a data breach that occurred between April and September 2023, affecting nearly 7 million users. Hackers accessed sensitive data, including health reports and genetic information.
The breach particularly targeted individuals of Chinese and Ashkenazi Jewish ancestry. A $30 million settlement was reached, providing affected customers with cash payments and enrollment in a three-year Privacy & Medical Shield and Genetic Monitoring program. (Reuters)
7. Yale New Haven Health System Data Breach
Yale New Haven Health System reported a major data breach that impacted 5.5 million individuals. The incident was discovered on March 8, 2025, and publicly disclosed on April 11, 2025.
The compromised information included names, dates of birth, home addresses, phone numbers, email addresses, race and ethnicity details, Social Security numbers, and medical record numbers. Hackers copied the data on the day of discovery, likely during a ransomware attack. Despite the breach, patient care operations were not disrupted.
There was no unauthorized access to financial accounts, employee HR records, electronic medical record systems, or payment information. Individuals whose Social Security numbers were exposed received credit monitoring services, and formal notifications began on April 14. (TechCrunch)
8. WK Kellogg Data Breach
WK Kellogg disclosed a data breach on April 4, 2025, involving its use of Cleo’s file transfer platform for HR file transfers. The breach occurred on December 7, 2024, and was discovered on February 27, 2025. It was linked to a broader series of attacks by the Clop ransomware group.
Employee and vendor data were affected, with at least one confirmed case involving a Maine employee whose name and Social Security number were compromised. The full scope of the breach remains unknown. WK Kellogg is offering one year of identity theft protection through Kroll.
Security researchers reported that patches for earlier Cleo vulnerabilities failed to fully block exploitation. In December 2024, a second flaw (CVE 2024 55956) was identified, allowing unauthorized users to run arbitrary PowerShell or bash commands. Arctic Wolf researchers also observed attempts to install Java based backdoors in Cleo MFT products.
Clop later claimed responsibility for part of the ransomware activity against Cleo users. Mandiant researchers attributed the malicious activity to a threat group tracked as FIN11. This incident highlights persistent vulnerabilities in third party platforms used for sensitive HR and employee data exchanges. (cybersecurity Dive)
Data Breaches That Occurred in March 2025
1. Oracle Cloud
On March 21, 2025, a threat actor known as “rose87168” was discovered selling 6 million records exfiltrated from Oracle Cloud’s Single Sign-On (SSO) and LDAP systems. The compromised data included Java KeyStore (JKS) files, encrypted SSO passwords, key files, and enterprise manager JPS keys.
This breach affected over 140,000 tenants, highlighting vulnerabilities in cloud infrastructure and the risks associated with third-party service providers. (Strobes)
2. Bank Sepah Data Breach
In early March 2025, Iranian financial institution Bank Sepah suffered a major cyber intrusion by a hacker collective known as “Codebreakers.” The attackers claimed to have accessed over 42 million customer records, including account numbers, passwords, mobile phone numbers, residential addresses, and bank transaction histories.

The breach exposed sensitive financial data, particularly affecting military and government sectors. The bank initially denied the breach but later issued warnings to local media against publishing the leaked data.( Wikipedia)
3. Pennsylvania State Education Association (PSEA)
In March 2025, the Pennsylvania State Education Association (PSEA), a labor union representing public school employees, experienced a significant data breach. The Rhysida ransomware group claimed responsibility for the attack, which resulted in the exposure of highly sensitive personal information of over 500,000 individuals.
The breach underscored vulnerabilities in the cybersecurity measures of educational institutions and the potential risks to personal data.( PKWARE®)
4. Australian Superannuation Funds
Several major Australian superannuation funds, including AustralianSuper, Rest Super, Australian Retirement Trust, Hostplus, and Insignia Financial, were targeted in a coordinated cyber attack affecting thousands of member accounts. The breach primarily involved “credential stuffing,” where hackers used previously stolen passwords to log into accounts.
Four AustralianSuper customers alone lost $500,000. Although some funds reported no stolen money, they confirmed unauthorized login attempts. Australian authorities are investigating the breach and urging financial institutions to enhance their cyber defenses. (ABC)
5. NSW Department of Communities and Justice Data Breach
In March 2025, the New South Wales Department of Communities and Justice (DCJ) experienced a significant data breach involving unauthorized access to the state’s secure online court registry system. An unknown hacker accessed at least 9,000 sensitive court documents, including apprehended violence orders (AVOs).
Authorities, including NSW Police, have been informed and are taking the situation seriously, especially regarding domestic violence survivors who may be at additional risk. The breach was discovered during routine maintenance, and a security patch has been applied to the system to close the vulnerability. (ABC)
Data Breaches That Occurred in February 2025
1. Genea Fertility Clinic (Australia) Information Leak
On February 14, 2025, Genea, an Australian fertility clinic, experienced a ransomware attack by the Termite group. The attackers accessed the clinic’s network from January 31 and extracted approximately 940.7GB of sensitive patient data.
The compromised information included personal contact details, medicare numbers, medical histories, test results, and medications. No financial data was reported as affected. Genea secured a court injunction to prevent further dissemination of the data and is collaborating with cybersecurity authorities to address the incident. (The Guardian)
2. Mars Hydro
In February 2025, Mars Hydro, a company specializing in hydroponic equipment, suffered a significant data breach. The incident resulted in the exposure of approximately 2.7 billion records, including sensitive information such as Wi-Fi passwords, IP addresses, and email addresses.
The breach highlighted vulnerabilities within the Internet of Things (IoT) landscape, emphasizing the need for robust security measures in connected devices. (Infosecurity Magazine)
3. Zapier
On February 27, 2025, Zapier, a workflow automation platform, disclosed unauthorized access to certain code repositories due to a misconfiguration of two-factor authentication on an employee’s account. The breach potentially exposed customer data inadvertently copied to the repositories for debugging purposes.
Upon discovery, Zapier secured the repositories and revoked the unauthorized access. The company is auditing its internal processes to prevent future incidents. (The Verge)
4. Western Sydney University
In February 2025, Western Sydney University experienced a data breach that compromised the personal information of approximately 10,000 current and former students.
The data, accessed through the university’s single sign-on system, included demographic, enrollment, and academic progression details.
Additionally, another set of sensitive information was discovered on a dark web forum, possibly posted in November 2024, and believed to have been accessed between August and October of the same year.

The university detected unauthorized access in January and February 2025 and promptly engaged internal and third-party cyber experts to mitigate the breach.
NSW Police and various national cybersecurity bodies, including the Australian Federal Police and the Australian Cyber Security Centre, are investigating the incident.
The university has taken legal action to prevent the misuse or dissemination of the stolen data and continues to monitor and strengthen its cybersecurity systems. (The Australian)
2025 ByBit Crypto Heist – $300M Stolen
On February 21, 2025, hackers linked to North Korea’s Lazarus Group stole approximately $1.5 billion in digital assets by compromising a supplier to crypto exchange ByBit.
The attackers secretly altered a digital wallet address, redirecting 401,000 Ethereum coins to their own wallet. ByBit unknowingly transferred the funds to the hackers.
Since the theft, around $300 million has already been converted into unrecoverable funds. Elliptic, a crypto investigation firm, confirmed that roughly 20% of the stolen assets have “gone dark.”
Analysts believe the Lazarus Group operates nearly around the clock using automation and a rotating team to evade detection. Their goal likely involves funding North Korea’s military programs.
While ByBit’s CEO Ben Zhou emphasized that no customer funds were affected and the firm has replenished the stolen amount through investor loans, the company launched a Lazarus Bounty program.
This initiative has distributed over $4 million to participants who helped trace $40 million in stolen crypto and prevent further laundering.
One of the main challenges has been inconsistent cooperation across crypto platforms. The exchange eXch allowed over $90 million to be moved through its systems before taking action.
Its owner, Johann Roberts, acknowledged a delayed response, citing a dispute with ByBit and uncertainty about the funds’ origin. He has since agreed to cooperate.
Despite public blockchain visibility, recovery efforts face obstacles due to the Lazarus Group’s experience and North Korea’s insulated economy. Experts consider North Korea uniquely effective in laundering stolen crypto, with few legal or reputational constraints limiting its operations. (BBC)
What Should I Do First After Receiving a Data-Breach Notification?
Below is a practical, step-by-step playbook for the first actions to take after you receive a data-breach notification—optimized to reduce account takeover risk and identity-fraud impact.
1) Confirm the notification is real (before clicking anything)
- Do not click links or open attachments in the email/SMS.
- Go to the company’s official website (type it in yourself) and look for a breach notice in your account dashboard or support page.
- If you must call, use a phone number from the company’s official site—not the message.
2) Identify what was exposed and what account it maps to
From the notice, capture:
- The service/account affected and the date range of exposure
- Data types (e.g., email, password, phone, address, NID/SSN, payment card, bank details, security questions)
- Whether passwords were hashed (still treat it seriously)
Write this down or screenshot it for records.
3) Secure the breached account immediately
- Change the password right away (make it unique and long).
- Turn on MFA/2FA (an authenticator app is typically stronger than SMS).
- Log out of other sessions (most services have “Sign out of all devices”).
- Review: account email/phone, recovery options, connected apps, forwarding rules (email), and any “trusted devices.”
Why this matters: Credential abuse remains a primary path to compromise—Verizon reports compromised credentials were an initial access vector in 22% of breaches reviewed in its 2025 DBIR research. Verizon
4) If you reused that password anywhere, change those next
Attackers often try the same email/password pair across banks, email, social, and shopping sites.
- Prioritize: email, financial accounts, mobile wallet, cloud storage, social media
- Use a password manager if possible to avoid reuse.
5) Watch for “breach follow-on” scams (phishing and fake support)
Expect emails like “confirm your refund,” “verify your identity,” “download your compensation form,” etc.
- Never share OTPs, recovery codes, or remote-access permissions.
- If someone contacts you “from the company,” hang up and call back using the official number.
6) Lock down financial exposure (based on what data was leaked)
- If card data may be exposed: call your bank/card issuer, request a replacement card, and set transaction alerts.
- If bank/mobile wallet access is at risk: change PINs, enable MFA, reduce transfer limits temporarily if available, and monitor transaction history.
7) Take identity-protection steps if sensitive ID data was exposed
If the breach involved government ID numbers, full DOB, or similar:
- Consider a credit freeze or fraud alert where available in your country (in the U.S., this is done via the 3 major credit bureaus).
- Obtain and review your credit report(s) if your jurisdiction supports it.
Context: Identity theft is common at scale—the FTC reported more than 1.1 million identity theft reports via IdentityTheft.gov in 2024. Federal Trade Commission
8) Monitor continuously for the next 30–90 days
- Review bank/credit statements weekly (daily at first if high risk).
- Watch for: password reset emails you didn’t request, new logins/devices, new payees, address changes, SIM-swap symptoms (sudden loss of mobile service).
9) Use any remediation the company offers (but validate it)
If the notice offers free monitoring, ID restoration, or support:
- Confirm it’s legitimate via the company’s official channels.
- Keep a record of enrollment confirmations and case numbers.
10) Document everything
Save:
- The breach notice, timeline, steps you took, receipts/case IDs
This is useful if fraudulent activity appears later.
Fast prioritization (if you only do 3 things today)
- Change password + enable MFA on the breached account (and your email).
- Change reused passwords on financial/mobile wallet accounts.
- Turn on transaction/login alerts and monitor closely.
Data Breaches Table Overview (January 2025 – December 2025)
| Month (2025) | Organization / Incident | Breach Disclosed (or Reported) | Impact (Records / People) | Data Exposed (High-Level) | Attack Vector / Notes |
|---|---|---|---|---|---|
| Dec | Pornhub Premium Mixpanel leak | Dec 12 | 201M | Emails, locations, URLs, keywords, timestamps | Unauthorized access to Mixpanel analytics data |
| Dec | SoundCloud ancillary service breach | Dec 15 | ~20% of users | Emails + public profile data | Ancillary dashboard compromise |
| Dec | 700Credit breach | Dec 22 | 5.6M | Names, addresses, DOBs, SSNs | Dealership-related data access (May–Oct) |
| Dec | Nissan (Red Hat-managed servers) exposure | Dec 23 | 21,000 | Names, addresses, phones, emails, sales records | Unauthorized access to vendor-managed servers |
| Nov | Coupang breach | Nov 29 | 33.7M | Names, phones, emails, delivery addresses, purchase history | Access persisted ~5 months |
| Nov | Salesforce data theft via Gainsight apps | Nov 14 | 200+ companies | Salesforce-hosted customer data | Compromised third-party apps and stolen tokens |
| Nov | DoorDash employee social engineering breach | Nov 18 | Not disclosed | Names, phones, addresses, emails | Social engineering against employee |
| Nov | Somalia eVisa system breach | Nov 13 | 35,000 | Applicant personal data | Unauthorized access to eVisa records |
| Oct | Qantas data leak (Salesforce-linked) | Oct 2025 | 5.7M | Names, emails, phones, addresses, DOB, FF numbers, points balances | Ransom deadline passed; data allegedly released |
| Oct | Red Hat GitLab consulting instance breach | Oct 1 | 570GB (claimed) | Internal repos + customer engagement reports | Extortion group claimed access to GitLab instance |
| Oct | Discord vendor breach (5CA) | Oct 2025 | 70,000 | Names, emails, ID images, support chats, partial billing | Third-party support vendor compromise |
| Oct | SonicWall cloud backup breach | Oct 2025 | All users of service | Encrypted firewall configs + AES-256 creds | MySonicWall compromise; Mandiant confirmed broad scope |
| Sep | Volvo breach via vendor Miljödata | Sep 25 | Unknown; 870,000 emails leaked across vendor clients | Names + SSNs (some US staff) | Vendor ransomware-driven theft |
| Sep | Kering (Gucci, Balenciaga, McQueen) | Sep 2025 | Not disclosed | Names, phones, emails, addresses, spending totals | ShinyHunters claimed; likely Salesforce credential abuse |
| Sep | Harrods breach via third party | Sep 2025 | 430,000 | Names, contact details, loyalty data | Vendor compromise |
| Sep | Wealthsimple breach (fewer than 1%) | Sep 2025 | <1% of 3M clients | SINs, government IDs, financial account numbers, IPs | Third-party software breach |
| Aug | TransUnion breach via third-party app | Late Aug | 4.46M | Names, DOB, SSNs, billing address, phones, emails | Third-party application compromise |
| Aug | Connex Credit Union breach | Aug 2025 | 172,000 | Names, acct numbers, debit card data, SSNs, IDs | Unauthorized access to internal files |
| Aug | Manpower ransomware breach | Aug 2025 | 144,180 | Personal info (HR-focused) | RansomHub claimed; 500GB allegedly stolen |
| Aug | Air France & KLM third-party tool breach | Aug 7 | Not disclosed | Names, contact details, Flying Blue numbers, email subject lines | Third-party customer support platform incident |
| Jul | Allianz Life CRM breach (US) | Jul 16 | 1.4M | Customer records (personal data) | Social engineering + third-party CRM |
| Jul | Tea dating app breach (messages) | Jul 2025 | 1.1M+ messages | Highly sensitive DMs + possible phone/location details | Firebase exposure; messages accessed until Jul 26 |
| Jul | Dell leak (World Leaks) | Jul 2025 | 1.3TB | Files tied to customer solution centers | Extortion leak; mostly demo/test and internal materials |
| Jun | 16B credentials leak (infostealer datasets) | Jun 2025 | 16B | Usernames, passwords, tokens, cookies | Aggregated infostealer-based credential dumps |
| Jun | UNFI cyberattack (supply chain disruption) | Jun 2025 | Not disclosed | Not confirmed (operational impact) | Network shutdown disrupted fulfillment |
| Jun | Sepah Bank cyberattack | Jun 2025 | Not disclosed | Not confirmed | Predatory Sparrow claimed destructive attack |
| May | 184M passwords database exposure | May 2025 | 184,162,718 | Logins and passwords | Publicly accessible database (no auth/encryption) |
| May | TeleMessage breach (US officials comms) | May 2025 | Not disclosed | Names, message fragments, contact info | AWS-hosted archive server compromised quickly |
| May | SAP NetWeaver exploitation wave | May 2025 | 581 systems | System compromise risk (RCE) | CVE-2025-31324 exploited by China-linked groups |
| May | PowerSchool extortion wave update | May 2025 | 62.4M students + 9.5M educators | Student and educator records | Ransom paid; extortion resumed |
| Apr | Yale New Haven Health breach | Apr 11 | 5.5M | Names, DOB, addresses, SSNs, MRNs, ethnicity details | Ransomware-style data copying suspected |
| Apr | NationsBenefits breach | Apr 2025 | 3M+ | PHI and sensitive personal data | Clop extortion activity |
| Apr | DBS Group / Bank of China via TNT vendor | Apr 2025 | 8,200 (DBS statements) + ~3,000 (BoC) | Names, addresses, loan acct info | Third-party print vendor compromise |
| Mar | Oracle Cloud SSO/LDAP records for sale | Mar 21 | 6M records | JKS files, encrypted SSO passwords, keys | Threat actor sale; 140,000+ tenants implicated |
| Mar | PSEA ransomware breach | Mar 2025 | 500,000+ | Sensitive personal data | Rhysida claimed responsibility |
| Feb | Genea fertility clinic ransomware | Feb 14 | 940.7GB stolen | Patient medical and personal data | Termite ransomware group |
| Feb | Western Sydney University breach | Feb 2025 | ~10,000 | Enrollment and academic progression data | SSO-related unauthorized access |
| Jan | Community Health Center (CHC) breach | Jan 2 | 1M+ | Personal + medical info, SSNs, insurance | Skilled intrusion; multi-state impact |
| Jan | TalkTalk data leak claim | Jan 2025 | 18.8M | Names, emails, IPs, phones | Third-party supplier system exposure |
| Jan | Gravy Analytics AWS breach | Jan 2025 | Not disclosed | Precise location data | AWS storage access exposed location intelligence |
FAQ
No, not always. Public disclosure timing depends on the type of organization, the laws that apply, and when the company confirms material facts. The FTC notes that breach notification duties vary across jurisdictions, and public companies may also face SEC disclosure rules for material incidents.
Yes, official sources are the best first check. Good starting points include company notices, regulator portals, and government breach pages such as HHS for HIPAA-covered incidents, Maine AG breach notices, and state attorney general breach notice repositories like California’s sample notice system.
Yes, you can check. Have I Been Pwned offers email checks and breach notifications, and its “Notify Me” feature lets users sign up for alerts when their email appears in new breaches.
Definitely act quickly. Start with the steps listed in the notice, change your password for the affected account, turn on multi factor authentication if available, and review your financial or account activity for unusual changes. The FTC also directs consumers to IdentityTheft.gov/databreach for breach-specific next steps.
Not always. A credit freeze is often more important when sensitive data like Social Security numbers or other identity data was exposed, while a password reset and account monitoring may be enough for lower-risk cases. The FTC guidance points readers to follow-up steps based on the type of information exposed.
Recent widely reported examples include the Abu Dhabi Finance Week (ADFW) document leak reported by Reuters on February 17, 2026 (more than 700 passports and IDs exposed via a third party storage environment), Nike investigating a claimed leak on January 26, 2026, Under Armour investigating a breach report affecting customer email addresses (AP report in January 2026), and the ongoing fallout from the Coupang breach in South Korea, which officials later said affected about 33.7 million customers.
If you mean the biggest data breaches by records compromised, a commonly cited March 2025 TechTarget ranking lists: Yahoo (3B), National Public Data (2.9B), Real Estate Wealth Network (1.5B), Aadhaar (1.1B), Shanghai Police (1B), First American Financial (885M), Indian Council of Medical Research (815M), Onliner spambot (711M), Ticketmaster (560M), and Yahoo 2014 breach (500M). Rankings can change depending on method and source.
Other Relevant Questions Around Data Breaches
Very recent breaches like Allianz Life in July 2025 and Qantas were caused by social engineering targeting third party platforms rather than internal systems. In these cases, attackers tricked staff into granting access, exposing millions of records
Yahoo. In 2013, hackers stole data from 3 billion accounts.
(Source: Wikipedia)
Sony PlayStation Network in 2011. Hackers stole personal data from 77 million users.
(Source: Wikipedia)
Yes. In June 2024, hackers accessed internal Apple tools. In February 2025, a passcode bypass flaw exposed iPhones to attacks.
(Sources: Forbes, New York Post)
Start with the organization’s official notice (and your account dashboard). For email exposure checks, services like Have I Been Pwned let you see whether an email address appears in known breach datasets. Some nonprofits also offer breach-alert subscriptions when an organization you use issues a public notice.
OpenAI has experienced security incidents, but whether it was “hacked” depends on definition. In March 2023, a bug exposed some users’ chat history titles and limited billing details for a small subset of Plus users. In November 2025, OpenAI disclosed a third-party analytics incident affecting some developer and API data, not ChatGPT passwords or payment details. Reuters also reported a 2023 intrusion into OpenAI’s internal messaging systems.
There is no confirmed single leaker. Reporting indicates that researchers identified multiple exposed datasets totaling roughly 16 billion credential records. These appear to be aggregated from many prior breaches and info-stealer malware logs, with significant duplication expected. This is best understood as a massive compilation of previously compromised data that became exposed, not one new breach of major platforms.
Generally, yes, if you use the official site. Have I Been Pwned is a well-known breach notification service and does not ask for your password to check an email address. Its Pwned Passwords feature uses privacy-preserving k-anonymity, meaning you do not submit a full password. As with any service, verify the domain and avoid look-alike links.
“Pwned” usually means your data, such as an email address or other attributes, appeared in a breach or leak. It does not automatically mean someone currently controls your account. It indicates exposure that could be used for phishing, credential stuffing, or account takeover attempts.
Usually, no. Deleting an email can disrupt access to many accounts and does not erase data that has already leaked. A better response is to change passwords, especially reused ones, enable multi-factor authentication, review recovery settings, and monitor for fraud. Creating a new email may make sense only if targeting is persistent and you can safely migrate accounts.
Several companies have disclosed data breaches recently, reflecting ongoing cyber risk across industries. Aflac reported a breach affecting millions of customers, with notifications updated in late 2025. Coupang disclosed unauthorized access to customer data, prompting regulatory scrutiny and lawsuits. Financial firms Prosper Marketplace and 700Credit also reported incidents impacting large numbers of records. Nissan confirmed customer data exposure linked to a third-party vendor breach. In addition, universities, healthcare providers, and retailers have continued to report breaches, underscoring persistent threats, especially from supply-chain vulnerabilities and credential compromise.
You can test whether your phone is compromised by using reputable mobile security apps and basic hygiene checks. Trusted options include Norton, Bitdefender, Malwarebytes, and Kaspersky, all of which offer strong malware detection, phishing protection, and risky-app alerts. Always download from official app stores, keep your OS updated, review app permissions, and enable multi-factor authentication.
Removing personal information from the web requires a mix of manual actions and specialized services. Data brokers collect and resell details such as names, addresses, phone numbers, and profiles, which are difficult to track individually. Services like DeleteMe handle this by continuously identifying data brokers and submitting opt-out requests on your behalf, with ongoing monitoring. Similar reputable alternatives include OneRep, Kanary, and Privacy Bee. You should also manually remove old accounts, adjust social media privacy settings, and opt out of people-search sites. While removal is not permanent, these services significantly reduce exposure and help limit future data misuse.
Often, yes. Senders can use tracking pixels that report when an email is opened, along with timing and device signals when images load. Some systems also use read receipts, which may require your approval depending on settings. To reduce tracking, disable remote image loading or use privacy features in your email client.
Not with an email address alone. However, it can be used for phishing, password-reset attempts, or account takeover if your email inbox is compromised or you reuse passwords. Protect your email with MFA, use unique passwords for email and banking, and enable bank alerts for logins, transfers, and new payees.
Common red flags include unexpected attachments or links, especially invoices, documents, ZIP files, or macro-enabled files; urgent or threatening language pushing immediate action; and sender or domain mismatches, or requests for passwords or sensitive personal information via email.
You are usually fine. Most compromises require clicking a link, opening an attachment, or entering credentials. Opening an email may still confirm your address is active or trigger tracking pixels if images load. Close the message, avoid suspicious unsubscribe links, mark it as spam, and run a malware scan if you opened an attachment
Get In Touch



