
Tamzid Ahmed | Security and Compliance Writer
April 11, 2025
Risks and Mitigation of Insider Threats: 8 Key Defenses for 2025
Your biggest security risk isn’t the hacker in a hoodie with their face obscured. It’s the people you trust: your staff.
Damian Garcia, Head of GRC Consultancy at IT Governance.
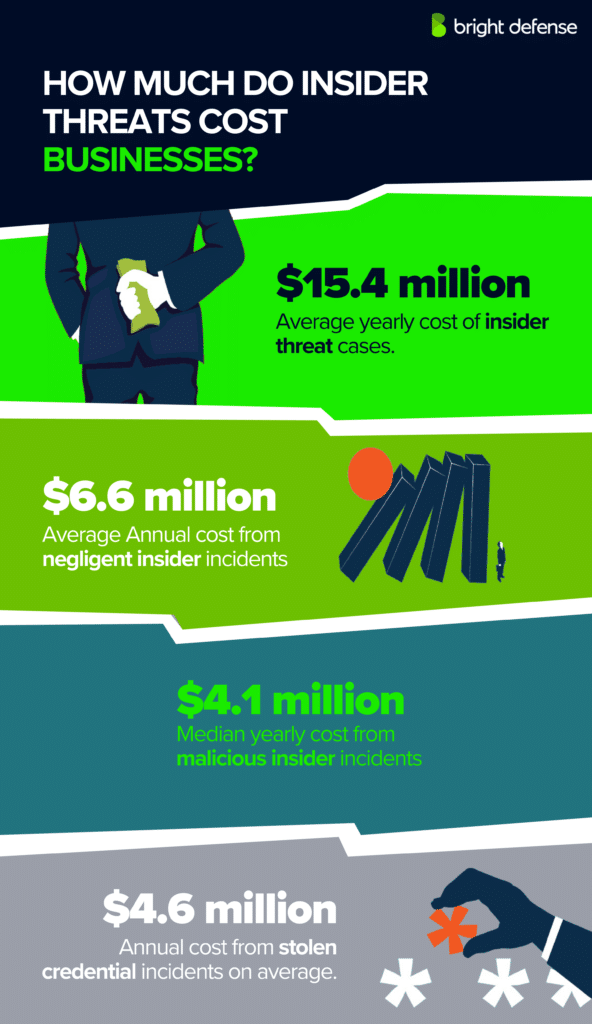
Insider threats aren’t just an IT problem anymore, they’re a growing business risk. A staggering 83% of organizations reported at least one insider-related security breach in the past year, and nearly half saw an increase in frequency. The kicker? Mitigating these threats now costs businesses an average of $16.2 million annually, a 40% spike since 2019.
With remote work, cloud-based operations, and evolving cyber threats, 2025 brings new challenges in securing sensitive data from the inside out. Whether it’s a careless employee, a disgruntled worker, or a well-meaning insider making a critical mistake, the risks are real.
Implementing a comprehensive insider threat mitigation program is essential to protect organizations from both deliberate and accidental data breaches.
So, what can you do? In this guide, we’ll break down 10 actionable ways to strengthen your insider threat mitigation strategy.
Let’s dive right in!
A Few Key Stats
- Insider threats, including potential insider threats, have increased by 47% since 2018.
- The average annual cost of insider threats is $11.5 million, with a 31% increase since 2018.
- It takes an average of 197 days to identify a data breach and another 77 days to recover.
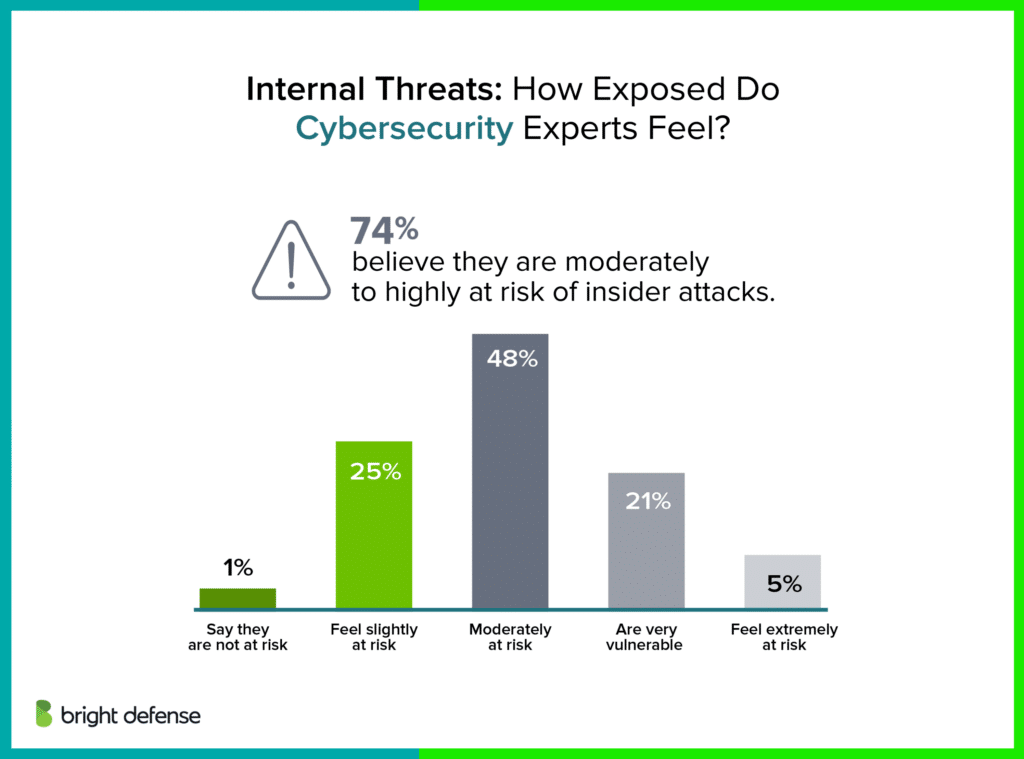
What is an Insider Threat?
An insider threat refers to a security risk that originates from within an organization. This could be an employee, contractor, or third-party vendor who, intentionally or unintentionally, compromises sensitive information, systems, or operations.
Imagine a finance employee at a company who accidentally clicks on a phishing email, thinking it’s a routine request from their manager.
The email contains a malicious link that compromises their login credentials, giving hackers access to valuable data and sensitive financial records.
Even though the employee had no malicious intent, their mistake led to a data breach, exposing customer data, payment details, and costing the company millions in fines and reputational damage.
This is a classic case of a negligent insider threat, where human element and error create a significant risk to the organization’s security posture, highlighting the importance of addressing unintentional insider threats.
Benefits of Insider Threat Mitigation
Proactively addressing insider threats protects businesses from security risks, financial losses, and compliance violations.
Here are some of the key benefits of a strong mitigation program:
- Prevents Costly Data Breaches – Stops unauthorized access controls and data loss prevention solutions, reducing financial and reputational damage.
- Ensures Regulatory Compliance – Helps meet GDPR, HIPAA, and other security policies, avoiding legal penalties.
- Maintains Smooth Business Operations – Prevents security incidents from disrupting workflows and productivity.
- Reduces Financial Losses – Minimizes the costs of breaches, fraud, and operational downtime.
- Promotes a Security-First Culture – Encourages employee education, awareness, and proactive threat detection.
- Enhances Insider Threat Prevention – Implements best practices and advanced software solutions to monitor and address potential insider threats effectively.
5 Types of Insider Threats
Not all security threats come from outside your organization. In fact, some of the most damaging breaches happen from within—whether intentionally or by accident.
These threats can lead to the theft of intellectual property, including proprietary information and trade secrets, causing significant harm to the organization.
Insider threats come in many forms, from employees who deliberately steal data to those who unknowingly expose sensitive information through careless mistakes.
Let’s break down the five major types of insider threats and how they put organizations at risk:

1. Malicious Insider Threats
These individuals exploit their privileged access to steal trade secrets, compromise critical systems, or sabotage operations. Their motives can range from personal gain and revenge to corporate espionage.
A 2022 study by the Ponemon Institute found that 26% of insider threat incidents stem from malicious activity. While poor company policies and disgruntled employees are often blamed, research shows financial gain is the primary driver. In fact, 81% of malicious insiders act with profit in mind.
“Data breaches caused by malicious insider threats are the most costly, averaging $4.99 million per incident.”
IBM
Example: A former IT administrator, upset about being laid off, deletes crucial files and installs a backdoor to maintain secret authorized access after leaving the company.
2. Negligent Insider Threats
These threats come from current employees who unintentionally weaken an organization’s security by ignoring protocols, mishandling critical data, or using poor cybersecurity practices. Even without bad intentions, their actions can lead to costly breaches.
Contrary to the belief that insider threat types are mostly caused by external threat actors with malicious intent, negligence is actually the biggest factor.
It accounts for more than half of all insider threat incidents. Phishing remains one of the most common negligence-related threats, with 38%of employees falling victim to these attacks.
“Phishing is a major problem because there really is no patch for human stupidity.”
Mike Danseglio, Cybersecurity Expert
Example: A manager forgets to lock their computer before stepping away in a public space, allowing unauthorized individuals to view sensitive information and potentially cause a data breach.

3. Compromised Insider Threats
A compromised insider is an employee whose account, device, or credentials have been taken over by an attacker through phishing, malware, or social engineering—often without their knowledge.
These incidents are among the most costly insider threats, averaging $804,997 per breach, according to the Ponemon Institute.
Many stem from negligence, like the 2021 Robinhood breach, where a scammer used voice phishing (vishing) to steal customer support credentials, exposing 5 million email addresses and 2 million names.
With hackers refining their tactics, compromised insiders remain a serious and expensive risk.
Example: A hacker sends a phishing email to an employee at a financial firm, tricking them into entering their login details on a fake website.
The hacker then uses these stolen credentials to access the company’s internal systems, transfer funds, or steal sensitive data, all while appearing as the legitimate employee.
“There are two types of companies: those that have been hacked, and those who don’t know they have been hacked.”
John Chambers, Former CEO of Cisco
4. Accidental Insider Threats
Accidental insider threats occur when employees inadvertently share, send, or store data in ways that make it vulnerable, often due to human error, miscommunication, or misunderstanding of security policies. In these cases, employees are unaware that their actions pose a threat.
Negligent insiders, on the other hand, understand security policies but choose to ignore them out of carelessness or convenience.
Example: A marketing employee uploads a confidential pricing strategy document to a public file-sharing platform, thinking it is restricted to internal users.
5. Third-Party Insiders
Businesses often grant access to contractors, vendors, or external service providers, but if these third parties have weak security practices or bad actors among them, they can become a major risk. 98% of organizations have at least one third-party vendor that has suffered a data breach.
Example: A cloud service provider experiences a security breach, exposing a company’s sensitive customer data that was stored on their platform.
Consequences of Insider Threats
Insider threats can lead to data breaches, financial losses, and reputational damage. Ignoring the risks can have serious consequences. Without proper security measures, organizations are vulnerable to significant risks posed by insider threats.
Here’s what’s at stake:
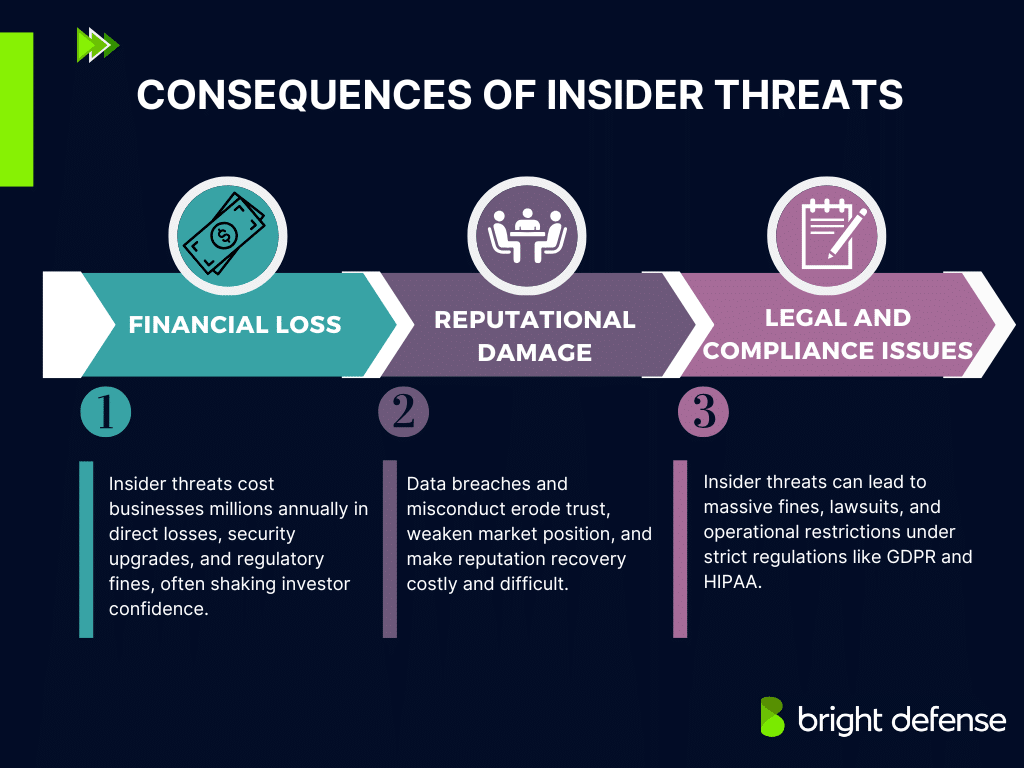
1. Financial Loss
Insider threats cause massive financial damage, whether intentional or accidental. Organizations lose an average of $11.5 million annually to insider threats, with each malicious attack costing around $701,500.
Beyond direct losses, companies face expenses for incident response, forensic investigations, security upgrades, and regulatory fines under laws like GDPR and SOX. For publicly traded companies, insider threats can also shake investor confidence and drive down stock prices.
The financial impact isn’t just immediate—it disrupts operations and long-term revenue, making insider threats a major risk for any business.
2. Reputational Damage
Reputational damage from insider threats is rising fast, with attacks aimed at harming a company’s image jumping from 8% to 37%. Leaks, data breaches, and internal misconduct can quickly erode public trust and brand credibility.
Customer trust is often the first to go. Data breaches push consumers toward safer alternatives, and once lost, trust is costly and difficult to regain.
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
Stephane Nappo, Cybersecurity Expert
The fallout doesn’t stop there—market position weakens, stock prices drop, and investors become wary. A damaged reputation can shake financial stability, making recovery an uphill battle.
Restoring trust takes time and resources, which is why proactive security and strong internal risk management are crucial.
3. Legal and Compliance Issues
Insider threats can trigger serious legal and compliance issues. Regulations like GDPR, HIPAA, and SOX require strict data security, and a single breach can mean massive fines, lawsuits, and operational restrictions.
GDPR penalties alone can reach €20 million or 4% of global turnover—whichever is higher. Between 2018 and 2024, the average GDPR fine was €2.1 million, with Meta facing a record €1.2 billion penalty in 2023 for improper data processing.
Beyond fines, legal battles drain time and resources while damaging credibility. Breaches involving customer or employee data can spark class-action lawsuits, regulatory scrutiny, and lost business partnerships.
For industries like finance and healthcare, insider threats can result in revoked licenses and restricted operations. Enforcing strong access controls, monitoring systems, and legal safeguards is crucial for staying compliant and avoiding costly setbacks.
Indicators of Insider Threats
Recognizing early warning signs is crucial to preventing insider threats. Unusual behavior, unauthorized access, and data misuse can signal potential risks.
Here are key indicators to watch for:
1. Behavioral Changes
Drastic changes in an employee’s behavior can signal an insider threat. Signs include secrecy, defensiveness, mood swings, or withdrawal from colleagues.
Someone who was once engaged but is now disengaged may be experiencing stress or dissatisfaction that could lead to security risks.
Employees working odd hours without explanation or expressing new grievances should be monitored. With insider threats responsible for 60% of data breaches, keeping an eye on behavioral shifts is critical.
2. Unusual System Access
Accessing systems at odd hours or from unknown locations could indicate malicious intent. Employees may try to bypass security, escalate permissions, or access sensitive data outside their role.
Attempts to reach restricted files or use shared credentials without authorization should be flagged. Monitoring logins and permission changes can detect risks before they escalate.
3. Unexpected Data Transfers
A sudden surge in file downloads, email attachments, or external drive usage is a red flag. Employees trying to steal data often transfer files to personal cloud storage, USB drives, or external emails.
Tracking file movements and setting alerts for unusual transfers can help detect threats. A strong data loss prevention (DLP) strategy can reduce insider security breaches.
4. Frequent Policy Violations
Many employees bypass security policies, with 65% admitting to doing so for convenience. Common violations include using personal Wi-Fi hotspots, sharing passwords, and forwarding corporate emails to personal accounts.
These shortcuts increase cybersecurity risks, as 74% of data breaches involve human errors like credential theft and misuse.
A proactive approach to the risks and mitigation of insider threats includes enforcing security training and strict compliance measures.
5. Privileged Access Abuse
The abuse of privileged credentials is a top security risk, contributing to 74% of data breaches. Employees with elevated access may intentionally or accidentally misuse their permissions to access sensitive data. Strong privileged access management (PAM) solutions can help prevent unauthorized access.
6. Third-Party Risks
Third-party vendors increase an organization’s attack surface, with 61% of companies experiencing a third-party breach in the past year, a 49% rise. Additionally, 73% have faced disruptions from vendor-related incidents. Weak security practices among vendors can open the door to cybercriminals.
7. Unauthorized Physical Access
Unauthorized access to high-security areas is a serious threat, whether from employees or outsiders. Studies show that over 90% of organizations have experienced access control failures. The most common weak points include tailgating, piggybacking, unattended open doors, and insufficient surveillance.
8 Strategies for Mitigating Insider Threats
Insider threats are hard to spot, but proactive measures can reduce risks. Strong access controls, monitoring, and employee training help prevent security breaches.
Here are 8 key strategies to strengthen your defenses.
1. Employee Awareness Training
Employee training is a key defense against insider threats. 50% of employees admit to security mistakes, highlighting the need for mandatory onboarding and regular refreshers.
Phishing tests with instant feedback improve awareness, while role-based training covers job-specific risks. Clear reporting channels encourage vigilance. Companies that prioritize engaging, gamified training can reduce insider threats by up to 70%.
Special Tips:
- Use real-world case studies to highlight the impact of insider threats.
- Conduct phishing simulations to test employee awareness.
- Reinforce training with short, frequent refreshers rather than one-time sessions.
2. Access Control Measures
Restricting access to sensitive data and systems is key to reducing insider threats. Use role-based access control (RBAC) to ensure employees only have permissions necessary for their tasks.
As remote work expands, securing access is tougher, 36% of companies struggle with rapid tech changes, and 31% face remote security challenges.
Regularly review and update access rights, especially when roles change or employees leave. Implement multi-factor authentication (MFA) to add an extra layer of security.
Special Tips:
- Enforce the principle of least privilege (PoLP) to limit unnecessary access.
- Use logging and monitoring tools to track access attempts.
- Automate access revocation for departing employees.
3. User Activity Monitoring
Tracking and analyzing user behavior helps detect suspicious activities before they escalate into security threats. Use monitoring tools to log access, file modifications, and unusual login patterns.
Set up alerts for anomalies, such as unauthorized data transfers or access outside regular working hours. Balance monitoring with privacy concerns to maintain trust among employees.
While monitoring is necessary, it must comply with privacy laws like GDPR and HIPAA. Transparent policies and ethical tracking ensure security without overstepping privacy boundaries.
Special Tips:
- Implement real-time alerts for high-risk activities.
- Use AI-driven behavior analytics to identify unusual patterns.
- Regularly review logs to spot trends and potential risks.
4. Regular Security Audits
Conducting routine security audits helps identify vulnerabilities and ensure compliance with security policies. These audits should review access controls, data protection measures, and employee adherence to security protocols. Use both automated scanning tools and manual assessments to get a comprehensive view of potential risks.
Special Tips:
- Perform both scheduled and surprise audits for better insights.
- Involve third-party auditors for an unbiased evaluation.
- Document findings and take immediate action on identified risks.
5. Open Communication
Creating a security-conscious culture starts with open communication. Employees should feel safe reporting security concerns without fear of retaliation. A clear, non-punitive reporting system allows early detection of potential threats.
Regular security training with real-world examples helps employees understand risks rather than just follow rules. Leadership transparency about security issues fosters a sense of shared responsibility.
Special Tips:
- Implement anonymous reporting channels for security concerns.
- Hold regular discussions on security policies to ensure practicality.
- Encourage employees to provide feedback on potential vulnerabilities
6. Insider Threat Program
A structured insider threat program helps organizations detect, prevent, and respond to security risks from within. This program should integrate access control, activity monitoring, and employee training to minimize threats.
It should also involve collaboration between HR, IT, and security teams to identify behavioral red flags early. Clear policies and swift action on suspicious activity strengthen overall security.
Special Tips:
- Define clear protocols for identifying and handling insider threats.
- Use behavior analytics to detect anomalies in user activity.
- Regularly update the program to adapt to evolving threats.
7. Zero Trust Security
Zero Trust operates on the principle that no user or device is automatically trusted, requiring continuous verification for every access request. It enforces strict access controls, multi-factor authentication, and micro-segmentation to minimize security risks.
Access policies adapt in real-time based on risk indicators like unusual login locations or abnormal activity patterns. This approach prevents unauthorized lateral movement within the network, reducing the potential impact of insider threats.
Special Tips:
- Implement least privilege access to limit unnecessary permissions.
- Use continuous authentication to verify user identity beyond initial login.
- Monitor real-time activity for potential security risks and automate response actions.
8. Monitoring and Detection Tools
Proactive monitoring tools help detect unusual activity before it turns into a security incident. Privileged Access Management (PAM) controls and tracks high-level accounts to prevent unauthorized changes. Data Loss Prevention (DLP) solutions monitor and restrict sensitive data transfers to prevent leaks.
User Behavior Analytics (UBA) uses machine learning to flag suspicious actions, like off-hours file access or excessive downloads. Together, these tools create a strong, multilayered defense against insider threats.
Special Tips:
- Use real-time alerts to detect abnormal user behavior early.
- Regularly review PAM logs to spot potential misuse of privileged accounts.
- Set automated rules in DLP to block unauthorized data transfers.
Final Thoughts
Insider threats remain a growing risk, but with the right strategies, businesses can minimize their impact. Strengthening access controls, monitoring user activity, and fostering a security-conscious culture through training and open communication are key steps.
Implementing advanced tools like Zero Trust Security and behavior analytics further reduces vulnerabilities.
As threats evolve, staying proactive with regular audits and adapting security policies will be crucial in 2025. A well-rounded approach ensures that insider threats are identified early and mitigated effectively.
FAQs
Mitigating insider threats involves implementing strategies such as establishing an insider threat program, conducting regular risk assessments, enforcing strict access controls, monitoring user activities, and providing security awareness training.
Mitigation of internal threats refers to the proactive measures and strategies organizations employ to identify, assess, and reduce risks posed by individuals within the organization who might misuse their access to harm systems or data.
Threats can be mitigated by implementing a combination of technical controls, such as data loss prevention tools and activity monitoring, alongside administrative measures like regular employee training, strict access management, and fostering a culture of security awareness.
The three primary motivations for insider threats are financial gain, where individuals exploit access for monetary benefits; revenge or disgruntlement, stemming from perceived wrongs within the organization; and espionage, where insiders steal sensitive information to benefit another entity or nation.
Get In Touch



