Jean Santiago
February 17, 2025
Secure by Design 2025 Guide: Building Systems Against Cyber Threats
Secure by design focuses on building security into every stage of development. Cyber threats are more advanced than ever, targeting vulnerabilities in systems with alarming speed. Reactive measures aren’t cutting it anymore.
That’s why security-by-design principles are becoming a must for companies looking to stay ahead. But what does secure by design actually involve?
In this article, we’ll break down the concept, explore real-world threats it can prevent, and provide practical strategies you can apply to strengthen your organization’s security posture. Let’s get started.
What Is Secure by Design and Why Does It Matter?
Secure by design is all about building security into every stage of development, from planning to release.
It’s not an afterthought. You don’t wait until a breach happens to react.
Instead, you spot vulnerabilities early, so attackers don’t get the chance. After all, cyberattacks are hitting harder than ever. In 2024, organizations faced an average of 1,876 attacks a week – marking a 75% increase from the same period in 2023.
So, if you’re still patching things after deployment and hoping for the best, you’re putting your systems at serious risk. It’s time to rethink how we build secure systems – and one of that’s the goal of secure by design.
Secure by Design vs. Security Features
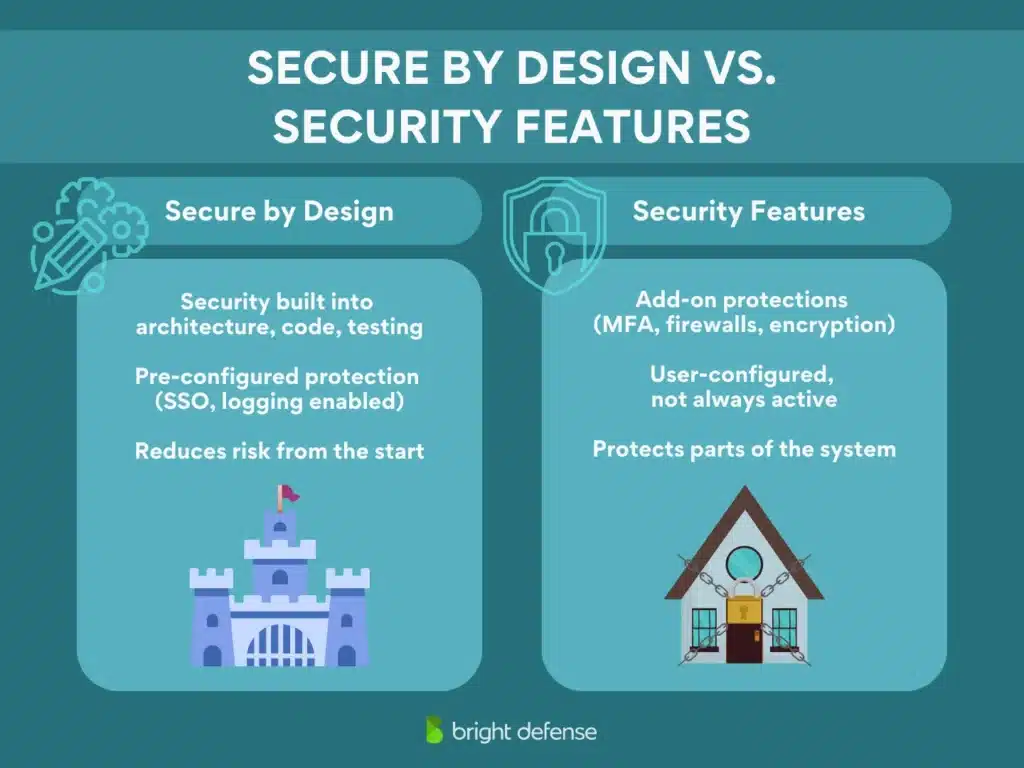
One thing we better clear up now: secure by design and security features aren’t the same thing.
A security feature, like multi-factor authentication (MFA), helps protect your system, but having features alone doesn’t mean you’re secure by design.
Secure by design takes it further. It bakes security into the system itself. Every part of the development process – architecture, coding, testing – has security built into it from the ground up.
Think of it like this. A product built with secure-by-design principles comes out of the box with things like SSO and event logging already enabled. You don’t need to tweak or configure anything to get a baseline level of protection. It’s designed to prevent errors and reduce risk from the start.
5 Real-World Examples of Cyber Threats That Exploit Poor Security
Cyberattacks aren’t just hypothetical – they’re happening constantly, and weak system design often plays a major role.
Let’s look at five real-world incidents where poor security decisions had serious consequences.
1. Colonial Pipeline Ransomware Attack (2021)
A single compromised password shut down the biggest fuel pipeline in the US. Hackers used poor remote access security to lock up critical systems, causing fuel shortages along the East Coast.
2. Optus Data Breach (2022)
Millions of Optus customers in Australia had their data exposed because of a poorly secured API. Weak design choices opened the door for attackers to extract sensitive personal information.
3. SolarWinds Supply Chain Attack (2020)
Hackers tampered with a software update for SolarWinds, infecting thousands of organizations, including US government agencies. Weak supply chain security made this attack possible.
4. Target POS Malware Attack (2013)
Target’s payment system was breached after attackers got in through a third-party vendor. Poor network segmentation allowed the attackers to move through systems and steal credit card details from over 40 million people.
5. NHS WannaCry Ransomware Attack (2017)
The UK’s National Health Service got hit hard by ransomware that exploited outdated Windows systems. Hospitals had to cancel surgeries and divert patients while trying to recover their systems.
3 Common Myths About Security Controls and Secure Systems
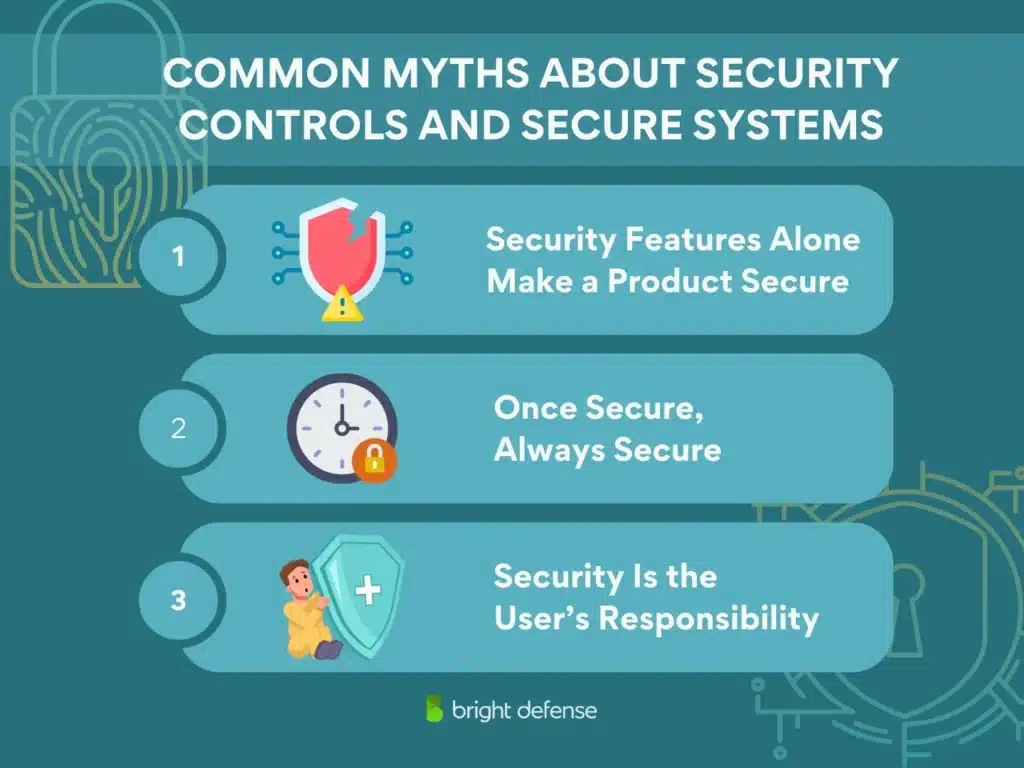
A lot of misconceptions still surround security. Some of these myths can lead to risky shortcuts and weak protection. Here are the most common myths and why they’re dangerous.
Myth 1: Security Features Alone Make a Product Secure
Many assume that adding security features – like encryption or multi-factor authentication – is enough to protect their systems. It’s not.
If the underlying system is poorly designed, attackers can still find ways around these features. For example, if access controls aren’t properly integrated into the system’s architecture, someone with the right permissions can bypass security entirely.
Security features work best when part of a secure-by-design approach, where vulnerabilities are reduced at every stage of development.
Myth 2: Once Secure, Always Secure
Some people think security is a one-and-done deal. But the truth is, security isn’t static. Threats change, attackers get smarter, and new vulnerabilities pop up all the time.
Systems that don’t undergo regular security testing and updates quickly become outdated and easy targets for cybercriminals. Continuous monitoring, security awareness training, and constant improvements are essential to maintaining security over time.
Myth 3: Security Is the User’s Responsibility
A common misconception is that users should handle security by applying patches, configuring settings, and running security tools. This mindset shifts too much responsibility onto customers, who may not have the expertise or time to manage these tasks properly.
Secure-by-design principles challenge this idea by putting the responsibility back on technology providers. Products should come secure out of the box – no complex setup or additional tools required.
This way, users get a solid baseline of protection without extra effort.
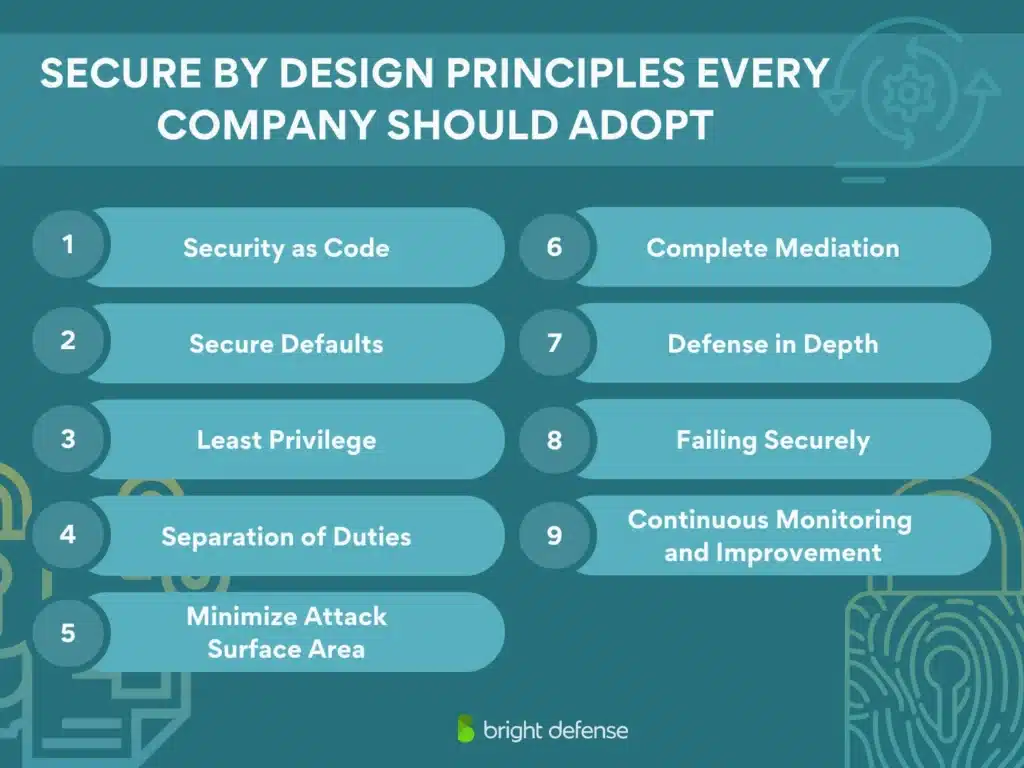
9 Secure by Design Principles Every Company Should Adopt
To truly embrace secure by design, you’ve got to integrate security into every step of development. It’s not enough to tack on a few security features at the end and call it a day.
Below are core principles that build resilient systems. These will protect your company and users from costly breaches and meet compliance standards at the same time.
1. Security as Code
Manual security processes are slow, inconsistent, and error-prone.
That’s where Security as Code (SaC) comes in. SaC automates security tasks through scripts and predefined code templates. This includes vulnerability scans, policy enforcement, and remediation workflows.
Tools like DevSecOps pipelines can automate security checks within your repositories (think GitHub or AWS), so you catch and fix issues as they appear – without slowing development. They also speed up audits and reduce human error, making it easier to prove continuous compliance.
2. Secure Defaults
Most users stick with default settings, so those defaults better be secure. Secure defaults mean pre-configured options that minimize risk right out of the box. For example, multi-factor authentication (MFA) might be required from the start, or a system might block all unnecessary ports by default.
The goal? Users shouldn’t need to make security tweaks on their own to stay safe. Companies like WordPress learned this the hard way after early versions with weak default settings caused mass exploits.
This is especially important when staying compliant with certain frameworks. For example, HIPAA emphasizes safeguarding patient data, which includes using secure configurations to prevent accidental data exposure.
3. Least Privilege
This one’s simple: users, apps, and services should only get the access they absolutely need. Nothing more.
That’s because the more access someone or something has, the bigger the damage if that access is abused or compromised. It’s also why access control is a core requirement in frameworks like SOC 2, ISO 27001, and HIPAA.
With the principle of least privilege, you assign roles and permissions carefully, then audit them regularly to cut down on unnecessary access. Automating this process helps prevent privilege creep, where permissions build up over time without anyone noticing.
Over 30,000 new vulnerabilities were disclosed in the past year, marking a 17% increase from the previous year.
Skybox Security, 2024
4. Separation of Duties
You don’t want any single person or system to have too much control. Separation of duties (SoD) means splitting responsibilities to reduce the risk of insider threats or errors.
In secure design, this means splitting responsibilities among different roles – development, testing, deployment – so no one person controls everything.
So, the developer writing code shouldn’t be able to deploy it to production. That step should involve someone else entirely. This principle applies across your entire organization. Automated approval workflows also create audit trails that can satisfy compliance requirements during inspections.
5. Minimize Attack Surface Area
The more points of entry a system has, the more ways an attacker can get in. Minimizing your attack surface means reducing these entry points. You can do this by limiting exposed services, closing unused ports, and removing outdated features.
For instance, if your app doesn’t need certain API endpoints or services running, shut them down. Every unnecessary feature is a potential vulnerability just waiting to be exploited.
6. Complete Mediation
Access checks should happen every single time someone tries to use a system resource. No shortcuts. This principle – complete mediation – prevents unauthorized access from slipping through cracks in the security policy.
Even if a user authenticates at the main gateway, each service or component they interact with should verify their permissions independently.
In practice, this could mean shutting down outdated services or using least-access policies for APIs to protect sensitive data.
7. Defense in Depth
No security measure is perfect. Defense in depth acknowledges that by layering multiple security controls to protect your system.
If one layer fails – like a firewall – other measures like intrusion detection systems or access controls are still there to block the attack.
This strategy forces attackers to jump through multiple hoops, making breaches harder and costlier to pull off. For compliance, this principle helps maintain security logs that track every access request, creating evidence auditors often require.
The annual cost of cybercrime is projected to exceed $23 trillion by 2027, rising from $8.4 trillion in 2022.
US Department of state, 2024
8. Failing Securely
No single control is foolproof, which is why defense in depth matters for compliance. When things go wrong (and they will), your system should always default to a secure state.
This is called failing securely. It means error messages don’t leak sensitive data, failed logins don’t reveal what part of the credentials was wrong, and the system doesn’t fall back to insecure behaviors during failures.
For example, a login error shouldn’t say, “Incorrect password for username [email protected].” Instead, it should just say, “Authentication failed.”
9. Continuous Monitoring and Improvement
Security isn’t set-it-and-forget-it. Continuous monitoring tracks system performance, identifies anomalies, and keeps your security measures current. This helps businesses catch vulnerabilities early and respond before they escalate.
Regular vulnerability assessments, automated logging, and incident response plans also provide the evidence auditors need to verify that your security controls are always operational.
Again, it’s all about staying proactive, not reactive.
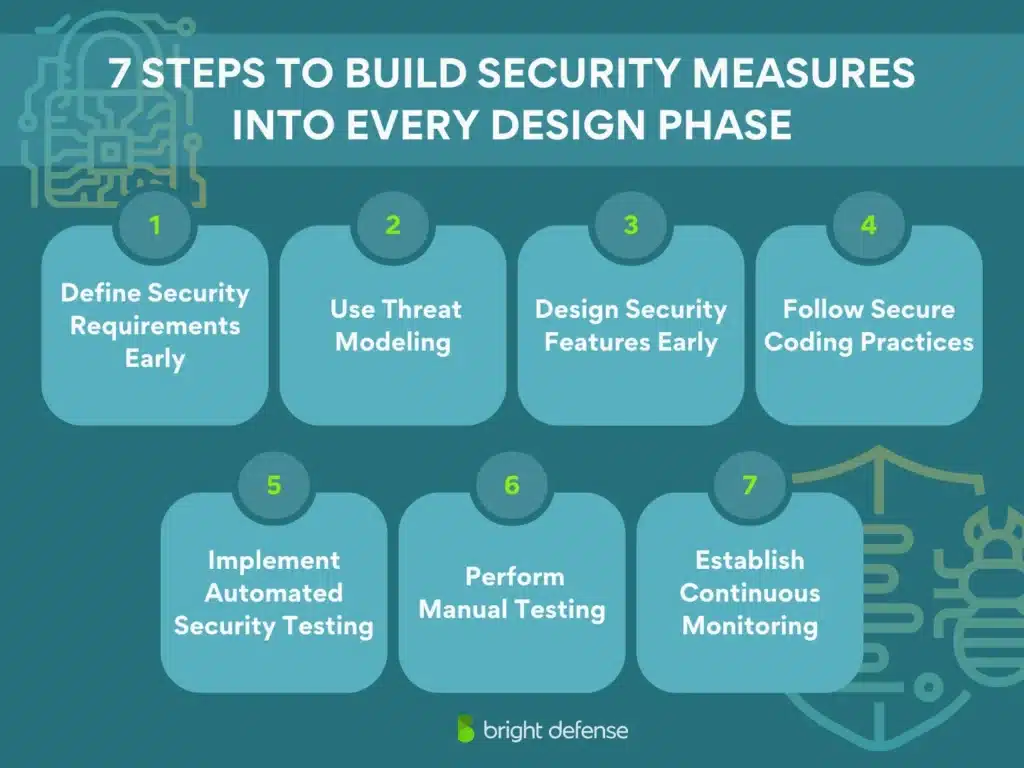
7 Steps to Build Security Measures Into Every Design Phase
If security is tacked on after development, you’re setting your system up for failure – and compliance nightmares. Secure by design fixes this by embedding security at every stage of the development lifecycle. Let’s walk through the steps to get it right.
Step 1: Define Security Requirements Early
Don’t wait until testing to think about security.
During the planning phase, clearly define your security requirements. For compliance frameworks like HIPAA and SOC 2, this might include access control policies, encryption protocols, and audit logging.
Collaborate with stakeholders to align security needs with business goals. You can also consult with us here at Bright Defense to find the best strategy for your compliance needs.
Step 2: Use Threat Modeling
Once you’ve set your requirements, map out potential attack paths using threat modeling. Identify which parts of your system are most at risk – sensitive data, API endpoints, external integrations – and determine how attackers might exploit them.
Tailoring the model to your system helps prioritize security features that provide the most protection. Make sure to update the threat model regularly to stay ahead of evolving threats.
Step 3: Design Security Features Early
Your system’s architecture should include security by default. For example:
- Enable encryption for sensitive data at rest and in transit.
- Build role-based access control (RBAC) to restrict who can access certain resources.
- Disable unnecessary services or features that could increase your attack surface.
These early design choices prevent security gaps that are harder and costlier to fix later.
Step 4: Follow Secure Coding Practices
Secure code is your first line of defense. Developers should focus on avoiding common vulnerabilities, such as those in the OWASP Top 10. Here’s how to tackle some of the most common risks.
- Validate input to avoid injection attacks. Attackers exploit unvalidated input to run unauthorized commands. Use parameterized queries or prepared statements to block attacks like SQL injection.
- Avoid hard-coded secrets. Storing API keys and credentials in your code increases security risks. Keep them in a secure vault or key management system.
- Use secure libraries. Vulnerable or outdated libraries create easy attack points. Regularly update your dependencies and ensure they follow security best practices.
- Handle authentication and authorization properly. Implement multi-factor authentication (MFA) and role-based access control (RBAC). Limit user permissions to only what’s necessary.
- Implement strong error handling. Error messages should not reveal sensitive information. Return generic responses like “Authentication failed” to prevent attackers from gathering system details.
Step 5: Implement Automated Security Testing
Testing isn’t just for the final product – it should happen continuously. Use tools to automate different types of tests:
- Static Application Security Testing (SAST). SAST analyzes code before it’s run. It helps detect vulnerabilities like hard-coded secrets, unvalidated input, and unsafe API usage early.
- Dynamic Application Security Testing (DAST). It simulates real-world attacks, checking how the app behaves under different scenarios. DAST tools help identify issues like broken authentication, misconfigured access controls, and injection vulnerabilities.
- Dependency scanning. It identifies security vulnerabilities in third-party libraries and frameworks that your application relies on. This reduces the risk of attackers exploiting known flaws in your software’s supply chain.
- Penetration testing. Pen tests go a step further by having security experts actively try to break into your system. This simulates what an attacker might do and reveals complex vulnerabilities that automated tools might miss.
Step 6: Perform Manual Testing (Penetration Testing)
Automation covers a lot, but not everything. Penetration testing simulates real-world attacks to uncover complex vulnerabilities.
Experienced security testers look for flaws in business logic, privilege escalation, and configuration weaknesses. This step is particularly important before launching new systems or handling highly sensitive data.
Step 7: Establish Continuous Monitoring
Software security doesn’t stop after deployment. Compliance frameworks require ongoing monitoring to detect and respond to incidents.
Set up logging, alerts, and regular vulnerability scans. Use a Security Information and Event Management (SIEM) system to track suspicious activity.
Continuous monitoring provides the evidence needed for compliance audits, while also protecting your systems from evolving threats.
How Secure by Design Improves the Software Development Process
Integrating security considerations throughout development isn’t just about preventing attacks—it transforms how teams build and maintain software.
- Prevents costly fixes later. Addressing security early reduces expensive rework and last-minute patches before or after deployment.
- Enhances compliance readiness. Security measures like access control, logging, and vulnerability management align with requirements for frameworks like SOC 2 and HIPAA.
- Reduces attack surface and risks. With security embedded into design and architecture, there are fewer weak points for attackers to exploit.
- Boosts development efficiency. Automated security testing and early threat modeling minimize interruptions during development, streamlining the process.
- Increases system reliability. Secure systems are more resilient to attacks, errors, and failures, reducing downtime and security incidents.
- Improves stakeholder trust. Products built securely from the start demonstrate a commitment to protecting users’ data and privacy, strengthening customer confidence.
Common Security Risks and How to Handle Them
Security risks can sneak in during early stages of development if you’re not paying close attention. Many of these risks are preventable but often overlooked, which puts companies at risk of both breaches and compliance failures.
Let’s explore the most common cyber security risks and how to deal with them effectively.
Top Security Risks Companies Overlook During the Design Phase
Failing to address security early can leave gaps attackers love to exploit. Here are some of the top risks that get ignored during the design process.
- Insider threats. Employees or contractors with access to sensitive systems can unintentionally or intentionally cause damage. Strong role-based access control (RBAC), regular security training, and activity monitoring help reduce this risk.
- Zero-day vulnerabilities. These are hidden flaws that attackers exploit before technology manufacturers can patch them. Regular vulnerability scans and penetration testing give you a fighting chance by catching other exploitable areas before attackers do.
- Inadequate access controls. Inconsistent or overly broad security protocols can create huge security holes. Implement least privilege and enforce periodic permission reviews to limit unnecessary access.
- Weak third-party security. Third-party software manufacturers may introduce vulnerabilities through insecure dependencies. Compliance frameworks like NIST and CIS emphasize vendor audits and tailored threat models to reduce this risk.
- Misconfigured infrastructure. Poorly configured cyber and physical infrastructure can lead to breaches. Automation tools that validate your system configurations against CIS benchmarks help prevent these errors.
How a Robust Vulnerability Management Program Minimizes Risk
A robust vulnerability management program does more than just patch software; it’s a continuous process that builds resilience against both known and emerging threats.
Here’s how you can create and maintain an effective program.
- Map out your digital assets. Identify your most critical applications, infrastructure, and third-party services. Use a tailored threat model to prioritize which assets need the highest protection.
- Schedule regular vulnerability scans. Use automated tools to detect misconfigurations, outdated libraries, and access control issues. This is a key step in complying with frameworks like CMMC and CIS.
- Perform penetration testing. Go beyond automation. Have experts simulate real-world attacks with web app pen testing or general penetration testing. This uncovers deeper issues, such as business logic flaws.
- Track and assign ownership of risks. Implement a GRC (Governance, Risk, and Compliance) framework to manage risk assignments across your organizational structure. This framework helps centralize audits and track progress for compliance needs.
- Develop a risk-based mitigation plan. Prioritize fixes based on the impact and likelihood of each vulnerability being exploited. Compliance frameworks often expect clear documentation of risk management strategies.
- Monitor continuously. Set up automated alerts to detect new threats and system changes. Continuous monitoring reduces the time attackers have to exploit vulnerabilities and demonstrates risk management to auditors.
- Iterate and improve. Use incident reviews and test results to refine your vulnerability management process. Regular updates to your tailored threat model help development teams stay ahead of potential threats.
Why Partner with BrightDefense
Reactive security is a losing battle. Fixing issues after a breach can lead to compliance violations, downtime, and loss of trust.
Proactive measures, like partnering with a company that specializes in continuous compliance, build long-term protection and minimize risk.
At Bright Defense, we provide tailored solutions that improve your security posture and help you comply with industry standards.
What We Can Do for You
- Continuous Cybersecurity Compliance. We handle all the security headaches tied to compliance frameworks like SOC 2, HIPAA, CMMC, PCI DSS, and ISO 27001. Our service evolves with your needs.
- Penetration Testing and Vulnerability Scanning. Automated vulnerability scans and web app pen tests help identify risks early. We give you the insight you need before attackers do.
- Virtual Chief Information Security Officer (vCISO). Get access to seasoned security experts without hiring a full-time CISO. We guide your development teams through risk management, security planning, and compliance strategies.
- Security Awareness Training. Through our partnership with KnowBe4, we deliver managed security training and phishing simulations to reduce the risk of human error, which causes 95% of breaches.
- Risk Assessments and Policy Development. We evaluate your security posture, prioritize risks, and implement security policies designed to protect your business. This includes business continuity planning and remediation efforts.
- Compliance Automation. Our tools give you real-time visibility into your compliance status and security incidents. No more scrambling before audits – everything is tracked and reported automatically.
Applying Secure-by-Design Principles with Bright Defense
Protecting your business doesn’t have to feel like an uphill battle. With Bright Defense, you’ll stay ahead of cyber threats, keep auditors happy, and build trust with your customers.
Ready to secure your future? Contact Bright Defense today and let’s get started!
Get In Touch



