Jean Santiago
March 19, 2025
A Complete Guide to Effective Security Awareness Training for Small Business in 2025
Did you know that 67% of organizations recognize a gap in their employees’ fundamental security knowledge? This highlights a critical need for security awareness training, especially for small businesses. In today’s digital landscape, cyber threats are increasingly sophisticated, and small businesses often become targets due to their vulnerabilities in cybersecurity awareness.
Fortunately, you’ve found the right resource. In this guide, we’ve teamed up with KnowBe4 to offer premier security awareness training solutions. These services are designed to boost your business’s cybersecurity savvy and ensure compliance with essential security frameworks such as SOC 2, HIPAA, and others, safeguarding your company’s digital environment.
Why You Need Security Awareness Training for Small Business

If you’re running a small business, you’re probably juggling multiple roles and working with limited resources. That often means hiring dedicated IT or cybersecurity staff isn’t realistic.
Unfortunately, this can leave your business vulnerable to cyber threats. But here’s the good news: The right security awareness training can help bridge the gap and help protect your business.
1. Reducing Human Error
The human element is one of the biggest things that can put your company at risk (which is why we’re big believers of using automated processes as much as possible.)
Employees clicking on phishing emails, falling for social engineering attacks, or mishandling sensitive data can put your entire business at risk.
Security awareness training can help. It teaches your team how to spot phishing attempts, avoid scams, and handle sensitive data responsibly. For example, instead of clicking a suspicious link, an employee might recognize the warning signs. This simple shift can save your business from expensive breaches and downtime.
2. Staying Compliant
Regulatory standards like SOC 2, ISO 27001, and the Health Insurance Portability and Accountability Act (HIPAA) often require ongoing employee training in cybersecurity.
Failing to meet these regulatory requirements can result in penalties, legal issues, and reputational damage down the road. It also increases your company’s risk.
Security awareness training for businesses helps your employees stick to compliance guidelines without overcomplicating things.
3. Building A Security-First Culture
Security awareness isn’t just about preventing attacks – it’s about changing how your team thinks about cybersecurity. When employees understand the risks of data breaches and the importance of their role in protecting the business, they become an active part of your defense strategy.
Training programs make security culture second nature. Your employees will start reporting suspicious emails without hesitation. They’ll begin double-checking permissions before sharing files. Over time, this mindset shift creates a workplace that’s more vigilant and prepared to tackle threats.
Four Components of an Effective Security Awareness Training Program
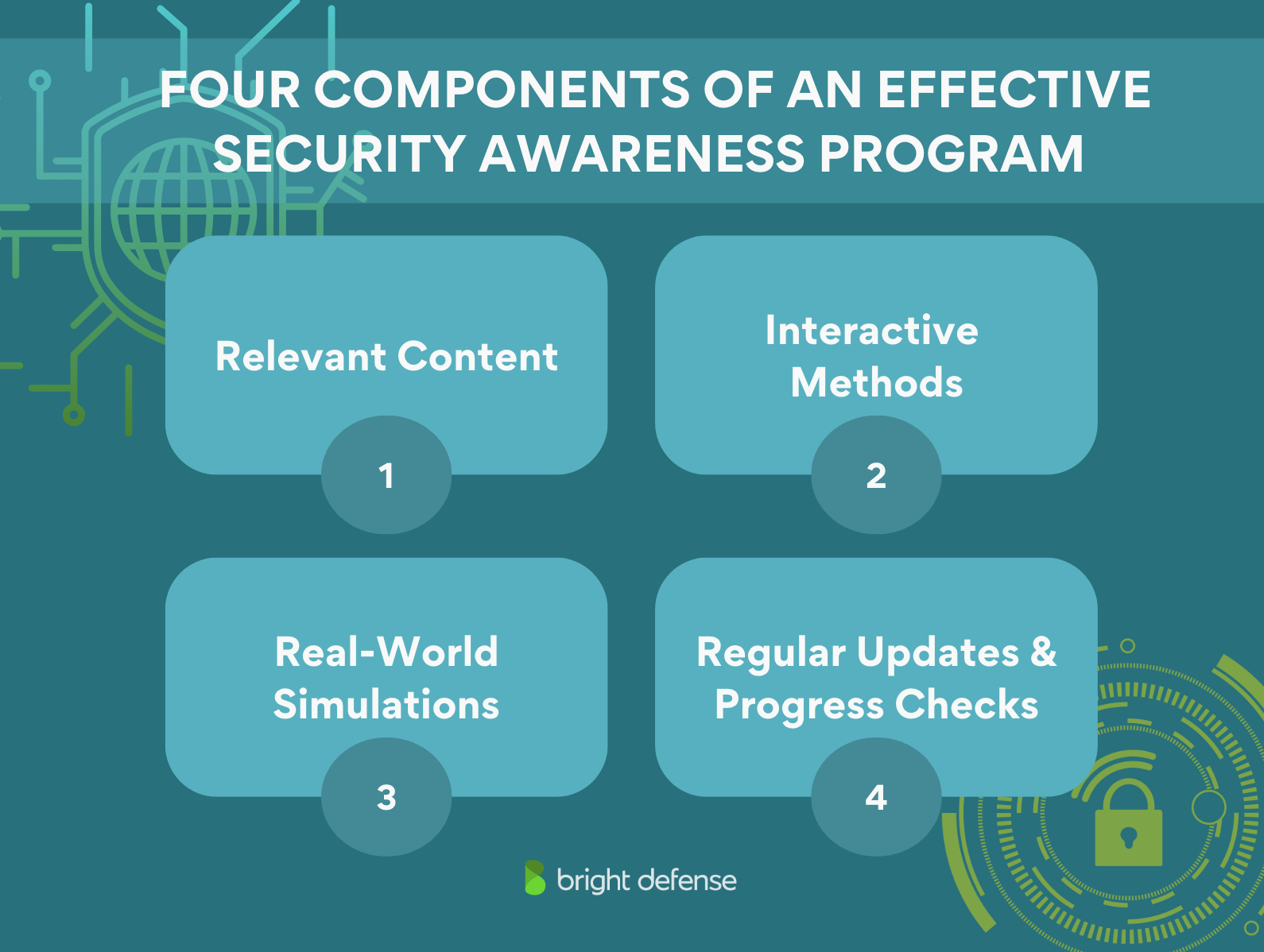
Building an effective information security awareness program takes more than just throwing information at your team. It’s about creating a thoughtful strategy that sticks.
Here are four components to get it right.
First Component: Relevant Content
The training has to cover threats your employees might actually face. Focus on practical topics like phishing, password security, ransomware, social engineering, and protecting sensitive information.
The more relatable the content, the more likely employees are to pay attention.
Second Component: Interactive Methods
No one wants to sit through a boring slideshow. Use hands-on exercises, like group activities or quick quizzes, to keep your team engaged. People learn better when they’re actively involved.
You can even run a game where employees identify security risks in a mocked-up email inbox. It’s fun, it’s practical, and it’s a lot more effective than just reading a list of tips.
Third Component: Real-World Simulations
Simulations take training to the next level. Phishing simulations or mock social engineering attacks help employees practice spotting threats in a safe environment.
For example, you can send a fake phishing email to your team. See who clicks the link and use it as a teaching moment. These exercises build confidence and prepare them for real-world attacks. It’s basically like the cybersecurity version of a fire drill.
Fourth Component: Regular Updates And Progress Checks
Cyber threats don’t stay the same, so your training shouldn’t either. Keep it fresh by adding new modules and tracking employee progress. Test your team’s awareness with a follow-up quiz and adjust based on the results. Regular assessments help you see what’s working and what needs tweaking.
5 Common Types of Cyber Threats
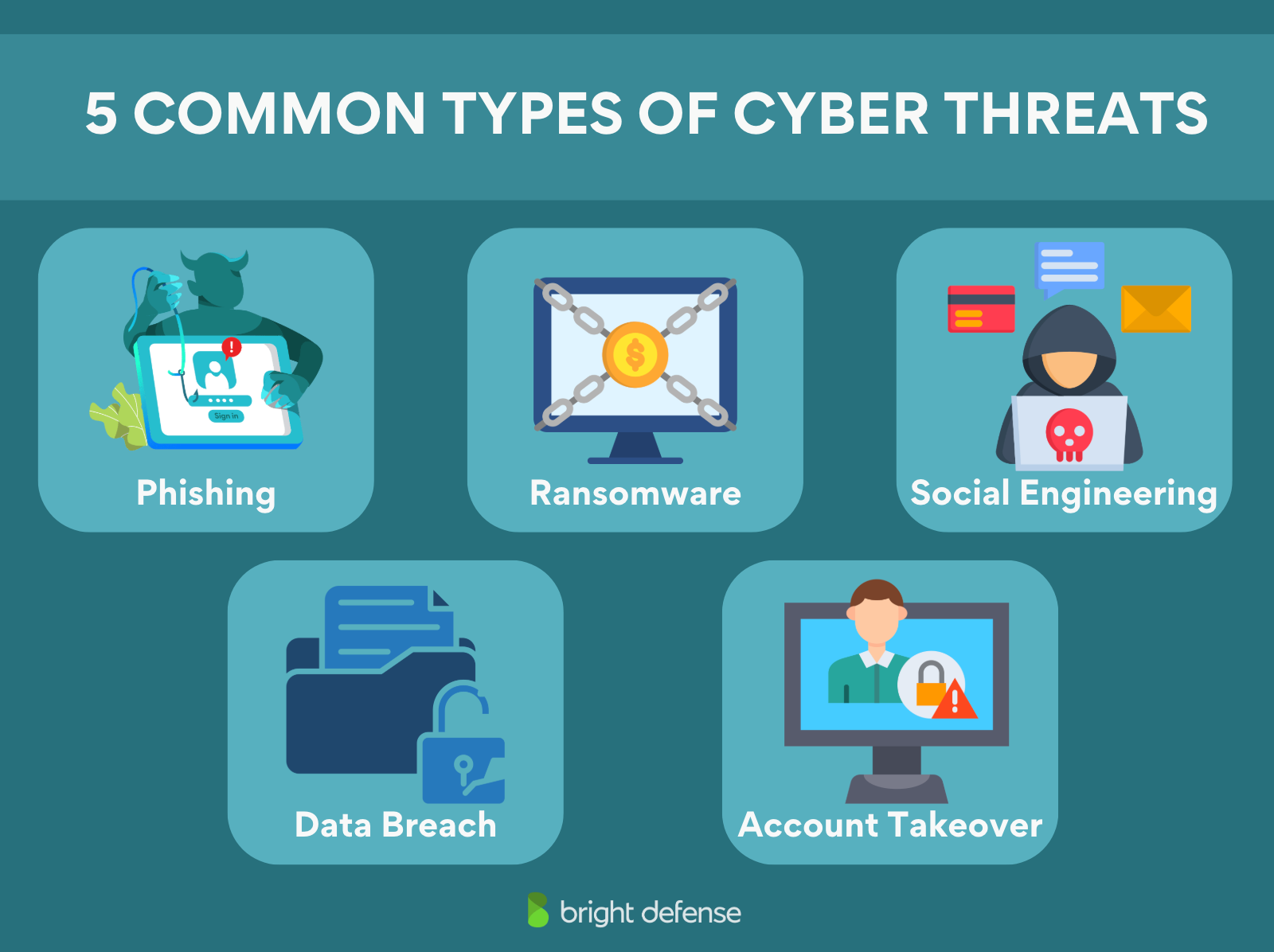
There are many types of cyber threats out there today. As a small business owner, you need to familiarize yourself with the most common types.
1. Phishing
Phishing happens when cybercriminals pretend to be trustworthy sources, like your bank or a well-known brand, to trick you into sharing personal data. This usually happens through email, but it can also occur via text messages or fake websites. Once they’ve got your credentials, they’ll be able to access accounts or steal money directly.
Considering 80% of organizations have had at least one employee fall victim to a phishing attack, it’s incredibly important that your employees are trained to avoid it.
Example: An employee receives an email that looks like it’s from you, asking them to buy gift cards for a client. The email says, “Quick, I need $500 in Amazon cards. Send me the codes ASAP!” The employee, wanting to help, buys the gift cards and shares the codes – only to find out later on that the email didn’t come from you.
2. Ransomware
Ransomware is malicious software that locks your files or systems, holding them hostage until you pay a ransom. Perhaps one of the biggest ransomware attacks ever recorded is the WannaCry ransomware attack of 2017. The attack affected hundreds of thousands of Windows devices, costing over $4 billion in damages.
Cybercriminals often target businesses, and payments are typically demanded in cryptocurrency to make it harder to trace. Even if you pay, there’s no guarantee you’ll get your data back.
Example: Your office computers suddenly display a message: “Your files are encrypted. Pay 2 Bitcoin within 72 hours, or everything will be deleted.” This attack started when an employee downloaded an attachment labeled “Invoice_123.pdf” from an unknown sender. That file installed ransomware, which locked up all important documents.
59% of organizations faced ransomware attacks in 2023, with 4,000 attacks hitting worldwide every single day.
Check point Research, 2024
3. Social Engineering
Social engineering tricks people into revealing information or taking action through psychological manipulation. Attackers play on trust, fear, or urgency to bypass technical safeguards. These schemes can happen online, on the phone, or even in person.
Example: A caller pretends to be from IT and says, “We’re updating the system. I need your login info to keep your account active.” Feeling pressured, an employee shares their credentials, giving the attacker access to the company’s internal systems.
4. Data Privacy Breaches
A data privacy breach happens when sensitive information like customer details, credit card numbers, or medical records, is accessed or exposed without permission. These incidents can damage reputations, cost you money, and even give you legal trouble.
Example: An employee accidentally uploads a file containing customer payment details to a public-facing server. Within hours, hackers download it, leading to unauthorized transactions and a PR nightmare for the company.
5. Account Takeovers
Account takeovers occur when hackers gain control of someone’s account. This could be email, banking, or even social media. Usually, they do this by stealing login details. Once inside, they can impersonate the victim, steal money, or spread malicious links.
Example: A hacker logs into a company’s social media account using credentials stolen in a previous phishing attack. They post fake promotions offering “free products” to customers who click a malicious link. The link installs malware, spreading the damage further.
How Cyber Security Awareness Training Protects You
A strong security awareness program does more than protect your systems – it turns your employees into your first line of defense. Here’s how training equips them to tackle cyber threats confidently.
- Spot phishing attempts before they cause damage. Your employees will learn to identify red flags in emails, such as suspicious links, unexpected attachments, or odd sender addresses. This makes it harder for attackers to succeed.
- Recognize social engineering tactics in action. Training helps your team understand manipulation strategies, like fake IT calls or urgent requests, so they can pause, verify, and report.
- Handle sensitive data with care. Employees learn the importance of storing, sharing, and accessing files securely, reducing the risk of accidental data breaches.
- Strengthen password habits. Teaching employees to create unique, strong passwords and set up multi-factor authentication adds layers of protection against account takeovers.
- Respond quickly and confidently to cyber threats. Awareness training equips your team with clear steps for reporting suspicious activity, minimizing damage, and getting systems back on track faster.
- Stay calm under pressure from cybercriminals. Employees become more confident in identifying scams, ignoring fake urgency, and reporting incidents, helping your business stay secure and operational.
5 Easy Steps to Develop an Effective Security Awareness Training Program
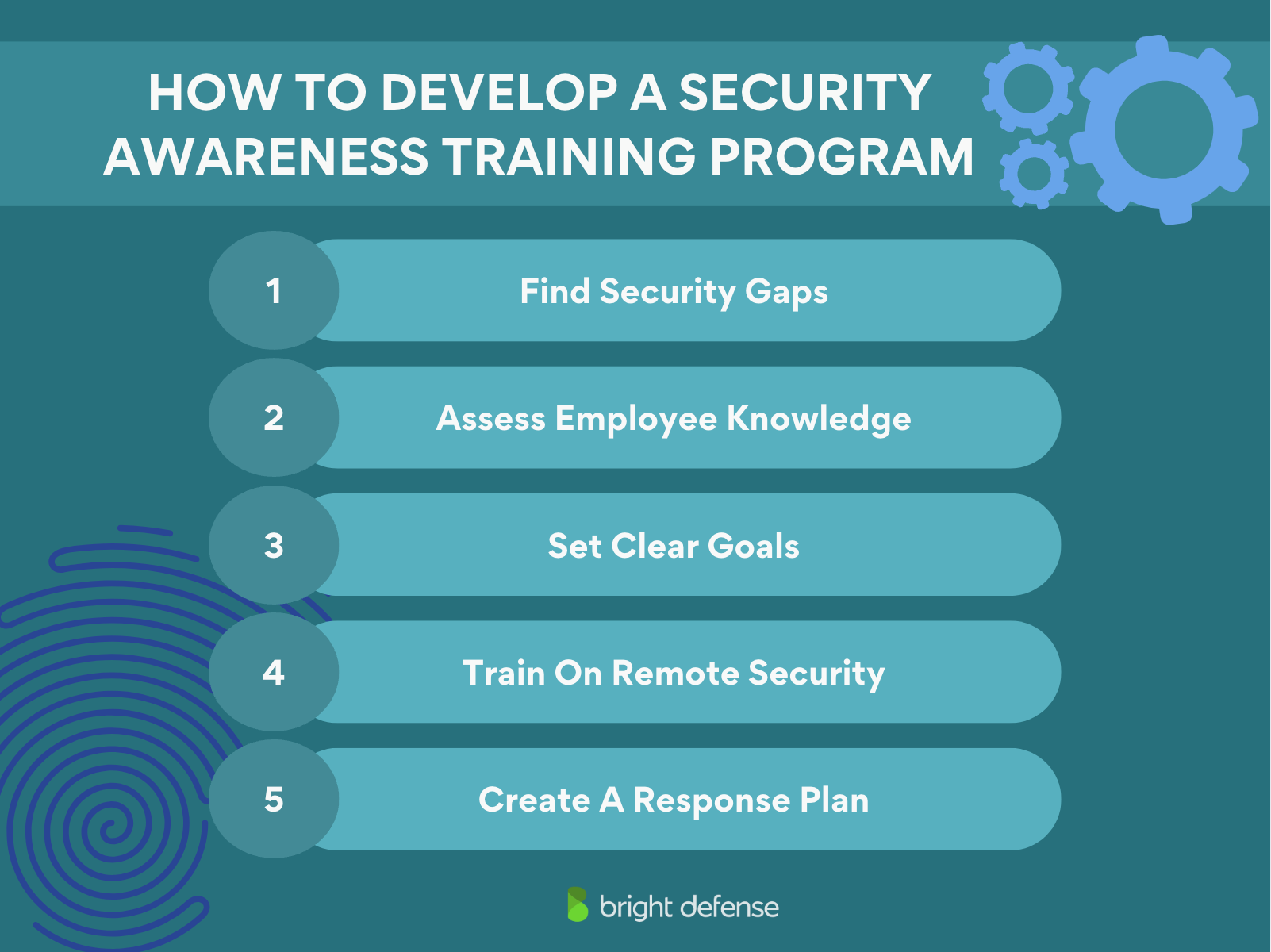
Cybersecurity doesn’t have to be overwhelming. A strong training program gives your employees the tools to handle threats and keep your business safe. Here’s how to build one in five easy steps.
Step 1: Find Security Gaps
Start by identifying where your business is most vulnerable. Look for common issues like weak passwords, missing multi-factor authentication, and poor physical security practices. A simple risk assessment can highlight areas needing improvement.
For example, are employees reusing passwords across accounts? Is sensitive data accessible without proper restrictions? Pinpointing these security gaps allows you to focus your training where it matters most.
| Pro-tip: Create a checklist of common vulnerabilities and evaluate your current systems. Share findings with your team to start building awareness early. |
Step 2: Assess Employee Knowledge
Gauge your team’s cybersecurity awareness with quick surveys or quizzes. Ask questions about phishing scams, password habits, and safe online behaviors to see where they stand.
You might discover that most employees can spot phishing attempts but don’t use password managers. Knowing this lets you customize training to address weak spots instead of covering topics they already understand.
| Pro-tip: Use tools like anonymous surveys or simulated phishing tests to get honest insights into your team’s skills. |
Step 3: Set Clear Goals
Define what you want your annual training to achieve. Do you want to reduce phishing clicks? Improve password security? Encourage faster reporting of suspicious activity? Clear goals give your training a purpose and help you track its effectiveness.
For instance, aim to cut phishing simulation failures by 20% within three months or get 100% adoption of multi-factor authentication across the team.
| Pro-tip: Break down big goals into smaller steps so you can measure progress and adjust as needed. |
Step 4: Train On Passwords And Remote Security
Password habits and remote work are two of the biggest cybersecurity challenges today. Cover topics like creating unique and complex passwords, using password managers, and enabling multi-factor authentication.
Don’t stop there – remote work adds extra risks. Teach employees to avoid public Wi-Fi or use a VPN when accessing sensitive company data. Also, include phishing-specific modules to help them recognize fake emails and protect confidential information.
| Pro-tip: Share real-world examples of breaches caused by weak passwords or insecure remote work practices to make the training relatable. |
Step 5: Create A Response Plan
Even the best training won’t stop every attack, so a clear incident response plan is a must. Employees should know exactly how to report suspicious activity, handle breaches, and recover data.
One way to do this is to give them a simple process for reporting issues, like emailing IT or using a specific tool. Teach them why regular data backups are important and how to access recovery systems.
| Pro-tip: Run practice drills to simulate incidents and test your team’s readiness. Use their feedback to improve your response process. |
7 Best Practices to Equip Employees With Proper Training
The success of your security awareness training program depends on using strategies that make it both practical and engaging.
For most organizations and small- to medium-sized businesses, here are the top practices to follow.
- Regular updates. Keep training materials fresh and aligned with the latest security threats and trends to stay relevant.
- Engaging content. Mix up formats—use videos, quizzes, infographics, and interactive exercises to keep employees interested.
- Real-world examples. Bring lessons to life with case studies or real-world scenarios employees can relate to.
- Interactive simulations. Hands-on simulations, like phishing exercises, give employees the experience they need to spot and respond to threats.
- Continuous learning. Encourage ongoing learning by offering frequent training sessions and easy access to helpful resources.
- Feedback loop. Collect employee feedback to improve and fine-tune the program based on what works and what doesn’t.
6 Training Methods and Formats for Security Awareness Training
Using different training formats keeps the program interesting and works for all learning styles. A mix of methods can be used to meet your needs as a small businesses while preparing employees to protect your organization against security threats.
- In-person training sessions. Face-to-face sessions allow for interactive learning and immediate feedback.
- Online training modules. Flexible and self-paced, these employee awareness training modules are can perfectly fit into their schedules.
- Video tutorials. Great for visual learners, videos explain complex ideas in an easy-to-digest format.
- Interactive simulations. Scenarios like phishing tests give employees a safe way to practice identifying and responding to real threats.
- Gamification. Adding game-like elements, like rewards or competitions, makes training fun and increases retention.
- Microlearning. Short, focused sessions are easier to absorb and help employees remember key concepts over time.
How to Track Progress With Measurable Results
Tracking the progress of your security awareness training program isn’t just about ticking boxes – it’s about understanding its impact on your business and making sure your team is actually learning.
A data-driven approach lets you evaluate results, identify weaknesses, and refine the program to make it better. Here’s how to do it effectively.
1. Set Clear KPIs for the Program
The first thing you have to do when starting a security training program is to define measurable key performance indicators (KPIs). These might include reducing the number of phishing simulation failures, increasing the use of multi-factor authentication, or cutting down response times to security incidents.
For example, if your initial phishing simulation had a 40% failure rate, aim to cut it to 20% within six months. Track progress against these goals and adjust the program as needed to meet them.
2. Use Dashboards and Reporting Tools
We’re lucky to be living in a world where it’s easy to access data from the tip of our fingers. These days, most –if not all – security awareness platforms come with built-in dashboards that track metrics like training completion, phishing simulation results, and overall security behavior.
Use these tools to create visual reports for leadership, showing how the program is improving security and reducing risks for the business.
3. Monitor Employee Knowledge and Awareness Levels
Regularly assess what employees know and how aware they are of security threats. Use tools like surveys, quizzes, or knowledge assessments to track progress over time.
For example, run a quick quiz after each training module to see what stuck. Follow it up with a more in-depth knowledge assessment every quarter to identify areas where employees might still be struggling, such as recognizing phishing attempts or understanding multi-factor authentication.
4. Measure Employee Behavior in Simulations
Use phishing simulations and other hands-on exercises to track how employees behave when faced with mock cyber threats. These scenarios provide real-world data on their ability to recognize and respond to risks.
For instance, if you send out a phishing email simulation, track how many employees clicked on the link, reported it, or ignored it. This shows you where the training is working and where it’s not.
5. Track Incident Reporting Rates
An increase in the number of reported suspicious activities can be a good indicator that your training is making a difference. Employees who are more aware of security risks are more likely to report phishing emails, strange file activity, or unauthorized access attempts.
One way to do this is to set up an easy-to-use reporting system, like a dedicated email address or a one-click button in your email client, to encourage employees to flag incidents. Then, monitor how frequently it’s being used.
6. Analyze Training Completion and Engagement Rates
Keep an eye on who’s completing training modules and how engaged they are with the content. Metrics like course completion rates, time spent on each module, and participation in quizzes or discussions can tell you how much value employees are getting from the program.
For example, if employees are rushing through modules or skipping quizzes, it might be a sign that the content isn’t engaging enough. Use this feedback to make adjustments, like incorporating more interactive elements or real-world examples.
Questions to Ask When Choosing a Security Awareness Training Provider
Choosing the right provider for security awareness training is a big decision since it directly affects how well your team is prepared to tackle cyber threats. To make the best choice, ask these questions.
- What experience do you have working with businesses in our industry? Providers with industry-specific experience understand the unique threats your organization faces, which means their training is more likely to cover real-world risks your team will encounter.
- How do you tailor your content to meet our specific needs? Generic training isn’t effective. Providers who customize their modules based on your team’s skill levels and the threats your business faces will deliver better results.
- What training formats do you offer? A mix of delivery methods, ike in-person sessions, online modules, and simulations, helps engage employees with different learning styles. This ups the chances that everyone benefits from the training.
- How do you keep the training materials up-to-date? Cyber threats evolve constantly, and outdated training can leave your business vulnerable. A good provider should offer regular updates to keep your team informed about the latest risks.
- What kind of ongoing support do you provide? Look for providers that offer post-training support, like refresher courses or access to resources. Ongoing assistance helps maintain your team’s security awareness long after the initial program ends.
- What tools or metrics do you use to measure training success? Providers that track metrics like phishing simulation results or training completion rates can show you clear evidence of how well the program is working and where improvements are needed.
- How does the program fit into our budget? It’s important to find a provider that balances cost with value. Ask about pricing models and compare them against the features offered to make sure you’re getting the best deal.
How KnowBe4 Enhances Security Awareness Training for Small Businesses
Knowing all of this, how can you protect yourself from cybersecurity threats?
Bright Defense might just have the answer for you.
We’ve teamed up with KnowBe4 to bring small businesses an industry-leading managed security awareness training platform. Designed to tackle cyber threats head-on, this platform offers advanced tools like phishing simulations and automated training programs to keep your team sharp and prepared.
Available through our Guardian and Defender plans, KnowBe4 Platinum is packed with features to make security awareness training for small business easy for you.
Core Features of KnowBe4 Platinum
KnowBe4’s core features are designed to cover the essentials, making your security awareness training program both practical and impactful.
- Unlimited phishing security tests. Train employees with realistic, simulated phishing attacks that adapt to evolving threats.
- Automated security awareness programs. Set up training sessions that run on autopilot, keeping everyone in the loop without extra hassle.
- Tiered training content. Offer Level I and II training to match employees’ security knowledge, from beginners to more experienced users.
- Phish Alert Button. Empower employees to report suspicious emails instantly, speeding up threat detection and response.
- Phishing reply tracking. Monitor how employees handle simulated phishing attempts and provide actionable feedback to improve skills.
- Vishing security tests. Prepare your team to recognize and handle voice phishing (vishing) attacks effectively.
Additional Features
Beyond the basics, KnowBe4 Platinum also offers advanced features that take your security program to the next level.
- Active Directory integration. Automate training assignments and user management with seamless directory service integration.
- Smart Groups. Segment employees based on behavior and risk levels for more focused and effective training.
- Social engineering indicators. Teach employees to spot subtle cues in phishing emails, boosting their ability to detect scams.
- USB drive tests. Evaluate your team’s physical security awareness with hands-on scenarios involving unknown USB devices.
- Monthly email exposure checks. Identify exposed employee email addresses online to reduce vulnerabilities before attackers exploit them.
Reporting and Analytics
Tracking progress and measuring results is easy with KnowBe4’s reporting and analytics tools, giving you valuable insights into your team’s security readiness.
- Industry benchmarking. Compare your organization’s training performance and phishing susceptibility with industry peers.
- Virtual Risk Officer™. Use advanced algorithms to assess individual user risk and develop tailored training plans.
- Advanced reporting tools. Access detailed analytics on training outcomes, employee progress, and overall security readiness.
- Reporting APIs. Integrate training data into your existing systems for comprehensive analysis and reporting.
Exclusive Benefits
And lastly, KnowBe4 Platinum doesn’t just stop at features. It offers exclusive perks to help small businesses strengthen their security posture and boost employee engagement.
- Security tips for employees. Provide your team with ongoing, actionable advice to improve daily security habits.
- Crypto-ransom guarantee. Protect your business financially in the rare event of a ransomware attack after training.
- Priority-level support. Get top-tier customer support whenever you need it, guaranteeing smooth program management.
Why Choose Bright Defense for Security Awareness Training?
Bright Defense is more than just a training provider – we’re your trusted partner in building a stronger, more resilient business.
By partnering with us here at Bright Defense, you can access KnowBe4’s powerful platform while benefiting from tailored services designed for your unique needs.
- Compliance made simple. Our training programs are aligned with industry standards like SOC 2 and ISO 27001, making it easier to meet compliance requirements while reducing risks. You’ll have the peace of mind that comes with knowing your team is trained to meet key compliance benchmarks.
- Budget-friendly pricing. At just $1.30 per user per month, our KnowBe4 Platinum subscription gives you access to premium training tools without overextending your budget. It’s a cost-effective solution that provides real value for small businesses.
- Relevant, practical content. We focus on training modules that address the specific risks your small business faces, from phishing and ransomware to password security and social engineering. Every module is designed to keep your team prepared for real-world scenarios.
- Ongoing updates and support. Cyber threats are constantly evolving, and so is our training. We provide regular updates to keep your program current, along with expert support to help you troubleshoot, customize, or improve your training experience.
- User-friendly setup. Our platform is easy to configure, requiring minimal IT resources to get up and running. From day one, you’ll have a smooth onboarding process and intuitive tools that make training management simple.
- Expert guidance at every step. With Bright Defense, you’re never alone. From initial setup to long-term program management, our team is here to help. We work with you to make sure your training program is effective, engaging, and always improving.
Getting Started with Bright Defense Security Awareness
Integrating Bright Defense into your organization is simple and effective. Here’s how to get started.
- Contact Us. Schedule a demo to discuss your specific needs and risks with our team.
- Review Options. Explore our content and delivery methods to find the best fit for your organization.
- Subscribe. Choose a plan that meets your budget and security goals.
- Customize the Platform. Tailor training modules and delivery formats to suit your team.
- Launch and Track. Roll out the program, monitor engagement, and measure results.
Improving Cybersecurity Readiness With Bright Defense
Investing in security awareness training for small business isn’t just a smart move – it’s a necessary step to protect your business. With Bright Defense and KnowBe4, you get affordable, high-quality solutions that empower your team to tackle cyber threats head-on.
Ready to take the next step? Contact us today and let Bright Defense help you build a safer, smarter, and stronger organization!
Get In Touch



