Tamzid Ahmed | Security and Compliance Writer
April 11, 2025
Vendor Risk Management – How to Stay Ahead in 2025
Businesses rely on third-party vendors for everything from software solutions to supply chain management.
While these partnerships bring efficiency and expertise, they also come with risks—data breaches, compliance issues, operational disruptions, and reputational damage can all stem from vendor-related security failures.
That’s why Vendor Risk Management (VRM) is essential. It helps businesses identify potential risks, evaluate vendor security measures, and put safeguards in place to protect sensitive information and maintain compliance.
As companies continue to expand their vendor networks in 2025, taking a proactive approach to risk management is more important than ever.
In this guide, we’ll cover what vendor risk management is, why it matters, and how to implement it effectively. Keep reading to learn the key steps for protecting your business from third-party risks.
What is Vendor Risk Management?
Vendor Risk Management (VRM) is the practice of identifying, assessing, and mitigating risks associated with third-party vendors, suppliers, service providers, or partners.
These risks can range from data security breaches and regulatory non-compliance to operational disruptions and reputational damage.
A structured VRM framework helps organizations maintain security, stability, and legal compliance while managing external relationships by integrating vendor risk management into the broader organizational risk management process.
Who is a Third Party Vendor?
A third-party vendor is any individual or company that supplies goods or services to your business without being directly employed by it. This includes manufacturers, suppliers, service providers, and contractors—whether temporary or permanent.
Managing these vendors requires assessing their access to sensitive information and ensuring they meet company standards. External staff, especially those with varying levels of cybersecurity awareness, can introduce risks.
Additionally, the IRS enforces regulations on vendor relationships, regardless of contract length.
Why is Vendor Risk Management Important?
Organizations are increasingly relying on third-party vendors to improve efficiency and focus on core competencies. However, this dependence introduces various risks that can significantly impact an organization’s operations, reputation, and financial health.
“A report indicates that 98.3% of organizations have relationships with third parties that have experienced breaches, highlighting the importance of effective VRM.“
Let’s find out what makes vendor risk management crucial in mitigating these risks:
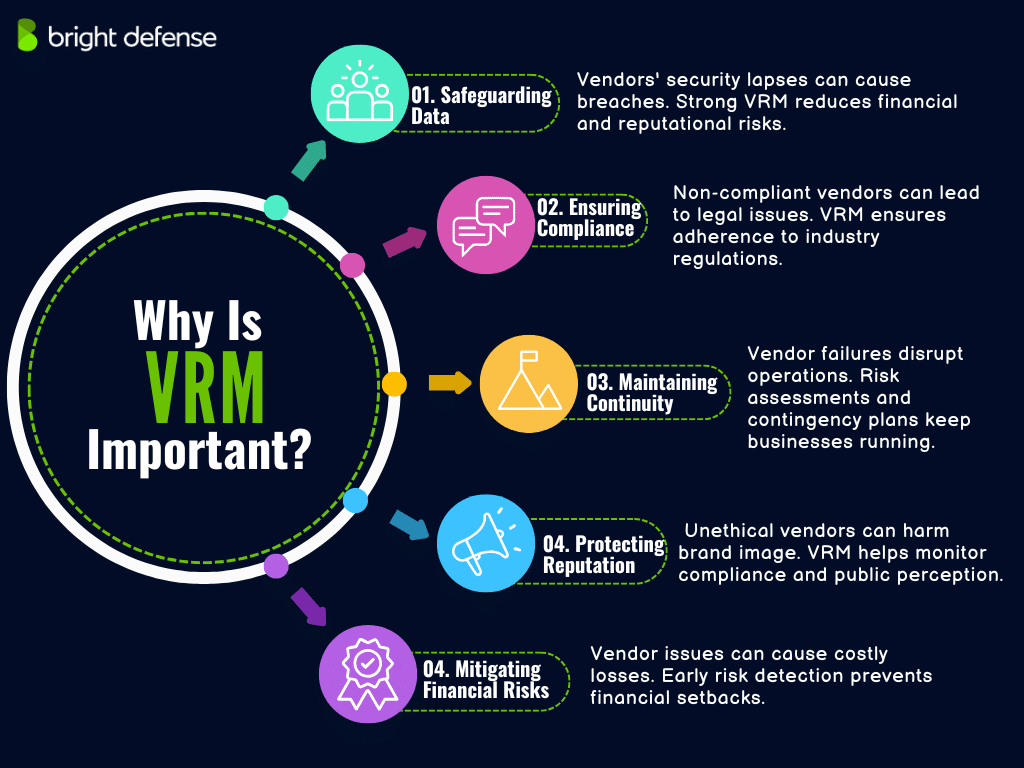
1. Safeguarding Against Data Breaches
Vendors often have access to sensitive data and critical systems. A security lapse on their part can lead to data breaches, exposing your organization to financial losses and reputational damage. Notably, 61% of organizations experienced a third-party data breach or security incident in the past year, marking a 49% increase from previous years.
2. Ensuring Regulatory Compliance
Many industries are subject to stringent regulations concerning data protection and operational practices. Non-compliance, even if due to a vendor’s actions, can result in hefty fines and legal consequences. A comprehensive VRM program helps ensure that vendors adhere to relevant laws and standards, thereby protecting your organization from potential legal issues.
Establishing a robust risk management program is essential to address critical risk areas associated with third-party relationships, including cybersecurity, compliance, and financial stability.
“A significant 83% of legal and compliance leaders identified vendor risks only after due diligence, with 31% of these risks resulting in material impacts.”
3. Maintaining Business Continuity
Operational disruptions at a vendor’s end can directly affect your organization’s ability to deliver products or services. Assessing vendors’ operational resilience and having contingency plans in place are vital components of VRM to maintain uninterrupted business operations.
4. Protecting Reputation
Associations with vendors that engage in unethical practices or suffer publicized security incidents can tarnish your organization’s reputation. A proactive VRM approach includes monitoring vendors’ compliance with ethical standards and public perception to mitigate reputational risks
5. Mitigating Financial Risks
Vendor-related issues can lead to financial losses, whether through direct costs like breach remediation and legal fees or indirect costs such as lost business opportunities. Implementing VRM practices helps identify potential financial risks early, allowing for timely mitigation strategies.
“The vendor risk management market is projected to grow from over USD 10.59 billion in 2024 to exceed USD 65.9 billion by 2037, reflecting a compound annual growth rate (CAGR) of over 15.1%.“
Key Elements of Vendor Risk Management
Effective Vendor Risk Management (VRM) minimizes security, compliance, and operational risks. These key components ensure strong oversight from onboarding to offboarding:
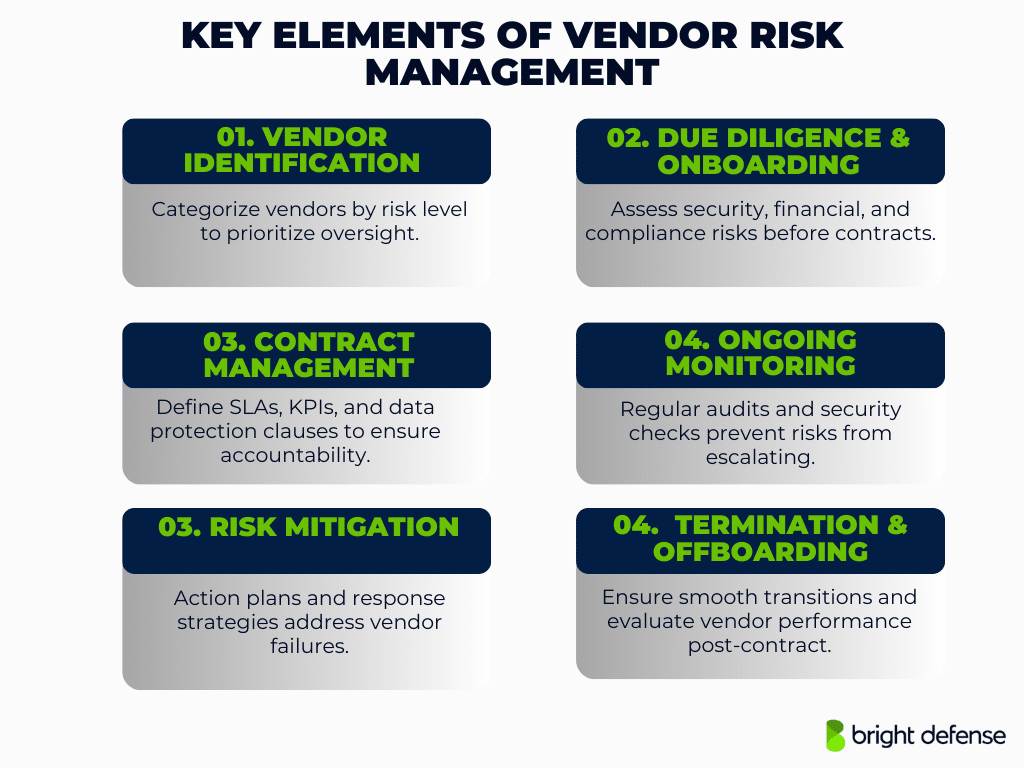
1. Vendor Identification and Classification
Organizations must identify third-party vendors and assess their importance. Vendors are categorized by risk level—high, medium, or low—to focus resources on those posing the greatest risk.
2. Due Diligence and Onboarding
Vendor onboarding involves assessing each vendor’s risk profile to identify potential cybersecurity, operational, and compliance risks. Before contracts are signed, vendors undergo security, financial, and legal assessments. Compliance checks confirm adherence to regulations like GDPR, HIPAA, and PCI DSS, ensuring vendors meet required standards.
3. Contract Management
Contracts should define SLAs, KPIs, and regulatory requirements. Data protection clauses must cover confidentiality and breach notification to safeguard sensitive information.
4. Ongoing Monitoring and Assessment
Vendor assessments, along with regular audits, track vendor performance, compliance, and financial stability. Security monitoring, whether real-time or periodic, helps detect risks before they escalate.
5. Risk Mitigation and Remediation
Organizations must have action plans to address vendor weaknesses and policy violations. Clear incident response coordination ensures quick resolution of breaches or disruptions.
6. Termination and Offboarding
When contracts end, a smooth transition prevents service disruptions. A post-contract review assesses vendor performance and improves future risk management strategies.
What are Some Third Party Risk Management Examples?
Every company that relies on third parties—from small businesses to global enterprises, faces potential vulnerabilities if those vendors fail to meet certain standards or requirements.
Below are two common examples of vendor risk scenarios and how organizations might address them:
Scenario 1: Data Security Risks from Cloud Service Providers
Imagine you’ve partnered with a cloud service provider (CSP) to store and manage sensitive customer data. Although CSPs often promise robust security measures, there can still be gaps if proper controls aren’t in place. A single misconfiguration in the vendor’s infrastructure or outdated security policies could expose your organization to data breaches or regulatory non-compliance. Identifying and monitoring risk exposure is crucial to enhance security measures and ensure compliance with regulations.
How to Address It:
- Due Diligence: Evaluate the CSP’s security certifications (e.g., ISO 27001, SOC 2) and request detailed documentation about their controls.
- Contractual Obligations: Ensure the service level agreement (SLA) includes explicit terms for data protection, breach notification timelines, and liability.
- Ongoing Monitoring: Regularly review the CSP’s security posture through audits, vulnerability assessments, and compliance checks. This proactive approach helps identify potential weaknesses before they become significant threats.
Scenario 2: Compliance Gaps with International Suppliers
A manufacturer sources components from an overseas supplier. The supplier might not follow the same labor standards, environmental regulations, or data protection laws that apply in the manufacturer’s home country. Non-compliance with these global regulations could lead to fines, legal challenges, or reputational damage—especially if unethical practices or violations come to light.
How to Address It:
- Clear Policies: Define strict requirements around labor practices, quality controls, and environmental standards in vendor contracts.
- Regular Audits: Conduct periodic site visits or employ third-party auditors to verify compliance with agreed-upon standards.
- Corrective Action Plans: If any violations are discovered, establish a clear timeline and process for remediation. Continuously track the vendor’s improvements to ensure long-term adherence.
7 Types of Vendor Risks
When working with third-party vendors, risks don’t just come from missed deadlines or poor service quality. Vendors can expose your business to legal liabilities, financial losses, reputational damage, and even cybersecurity threats. Understanding these risks is essential for protecting your company and maintaining smooth operations.
Below are seven key vendor risks every organization should be aware of and strategies to mitigate them:
1. Legal Risk
Legal risk occurs when a vendor’s actions—or lack of compliance—result in legal liabilities for your organization. This could be due to a breach of contract, violation of industry regulations, or failure to uphold regulatory requirements (such as GDPR, HIPAA, or other relevant legislation).
Key Considerations:
- Contractual Non-Compliance: If a vendor doesn’t fulfill contract terms (e.g., delivering poor-quality products or missing deadlines), you may face breach of contract disputes.
- Regulatory Violations: Non-adherence to data privacy laws or employment regulations can lead to fines and government sanctions.
- Intellectual Property (IP) Issues: Using or reproducing unauthorized content or software through a vendor can invite lawsuits.
Mitigation Strategies:
- Draft clear, comprehensive contracts with defined service levels and liability clauses.
- Conduct thorough due diligence on vendors’ regulatory track records.
- Maintain an open channel for legal updates and ensure vendors stay informed about new laws.
2. Reputational Risk
Reputational risk arises when a vendor’s actions harm public perception of your brand, highlighting the importance of managing third party vendor risk. This can include unethical labor practices, data breaches, or negative media coverage due to unethical or illegal vendor behavior.
Key Considerations:
- Customer Trust: If your supplier is caught engaging in unethical practices, your brand’s credibility can suffer, leading to lost customers.
- Media Scrutiny: News outlets or social media may quickly draw attention to scandals—amplifying negative impact.
- Industry Relationships: You may face backlash or loss of business partnerships if associated with dubious vendors.
Mitigation Strategies:
- Perform extensive background checks on vendors, including their leadership and ESG (Environmental, Social, Governance) track records.
- Create a crisis communication plan to address potential negative publicity swiftly and transparently.
- Encourage strong corporate values in vendor agreements and monitor vendor compliance with ethical standards.
3. Financial Risk
Financial risk involves the potential monetary losses that may occur if a vendor becomes unable to fulfill obligations or if hidden costs arise due to unexpected circumstances like currency fluctuations or supply chain disruptions.
Key Considerations:
- Vendor Solvency: If a vendor goes bankrupt, you could lose critical supplies or services, disrupting operations.
- Hidden Costs: Exchange rates, shipping fees, or unforeseen tariffs can inflate costs.
- Fraud or Overbilling: Weak financial controls at the vendor’s end can lead to billing inaccuracies or even fraudulent activities.
Mitigation Strategies:
- Conduct credit checks and request financial statements to gauge a vendor’s stability.
- Establish clear payment terms and monitor invoices for discrepancies.
- Diversify your supplier base to avoid relying on a single high-risk vendor.
4. Cyber Risk
Cyber risk involves threats to information security and data privacy. If a vendor with access to your systems or customer data is breached, your organization could face regulatory fines, reputational damage, or operational shutdowns.
Therefore, it is crucial to manage vendor risk by identifying, assessing, and mitigating potential risks associated with suppliers to minimize their impact on business operations.
Key Considerations:
- Data Breaches: Unauthorized access to sensitive information can harm both customer trust and compliance status.
- System Vulnerabilities: Weak security protocols at the vendor’s end could be exploited to access your networks.
- Malware and Ransomware: Attacks on vendor systems can quickly spread to your own infrastructure.
Mitigation Strategies:
- Require robust cybersecurity controls (e.g., SOC 2 reports, ISO 27001 certifications).
- Use third-party risk assessment tools to continuously monitor for security vulnerabilities.
- Develop an incident response plan, detailing how to respond if a vendor-related cyber issue arises.
5. Environmental Risk
Environmental risk pertains to potential negative impacts on the environment from a vendor’s operations. These might include pollution, resource depletion, or non-compliance with environmental regulations.
Key Considerations:
- Regulatory Fines: If a vendor’s environmental practices break local or international laws, you could face legal consequences as a client.
- Customer Backlash: Consumers increasingly prefer brands that prioritize sustainability. Partnering with environmentally irresponsible suppliers can harm brand perception.
- Supply Chain Disruptions: Environmental infractions can shut down vendor facilities, delaying deliveries.
Mitigation Strategies:
- Include sustainability clauses in vendor contracts, specifying waste management, emissions, and energy use policies.
- Conduct on-site audits or request environmental compliance certifications (e.g., ISO 14001).
- Work with vendors to implement greener practices and reduce carbon footprints.
6. Political Risk
Political risk arises from changes in a country’s political environment or government policies that can affect a vendor’s ability to operate.
This is especially relevant when outsourcing to or sourcing materials from regions with political instability or frequent regulatory changes.
Key Considerations:
- Policy Shifts: Sudden tariff increases, embargoes, or import/export restrictions can inflate costs or block access to critical materials.
- Civil Unrest: Strikes, protests, or governmental changes can delay production or disrupt transportation channels.
- Sanctions: Working with vendors in sanctioned regions could violate international laws.
Mitigation Strategies:
- Diversify supplier locations to reduce dependence on politically volatile regions.
- Stay informed on geopolitical developments and adjust supply chain strategies accordingly.
- Secure trade insurance or apply risk-sharing contracts to cushion financial impacts.
7. Fourth-Party Risk
Fourth-party risk refers to the risks posed by a vendor’s own subcontractors or suppliers. Even if your direct vendor meets all compliance and security standards, their partners might not. This “chain effect” can cascade issues back to your organization.
Supplier risk management is crucial in evaluating and mitigating these risks to safeguard against potential threats such as data breaches, regulatory violations, and supply chain disruptions.
Key Considerations:
- Lack of Transparency: Vendors might not disclose who they subcontract with or the nature of their own supplier relationships.
- Supply Chain Gaps: If a critical fourth-party fails, it can disrupt your vendor’s services.
- Complex Liability: When data breaches or compliance failures originate with a fourth-party, determining liability becomes more challenging.
Mitigation Strategies:
- Require vendors to maintain the same risk management and compliance standards with their subcontractors.
- Ask for regular updates on the vendor’s partner network and any newly added subcontractors.
- Use third-party risk assessment platforms to monitor not only your vendor but also their extended supply chain.
How to Address a Vendor Breach
When a vendor breach hits, quick action is key. A third-party security failure can expose sensitive data, disrupt operations, and damage trust. Instead of scrambling, having a clear response plan ensures you contain the damage and protect your business.
Here’s how to handle a vendor breach effectively, from identifying the issue to mitigating future risks:
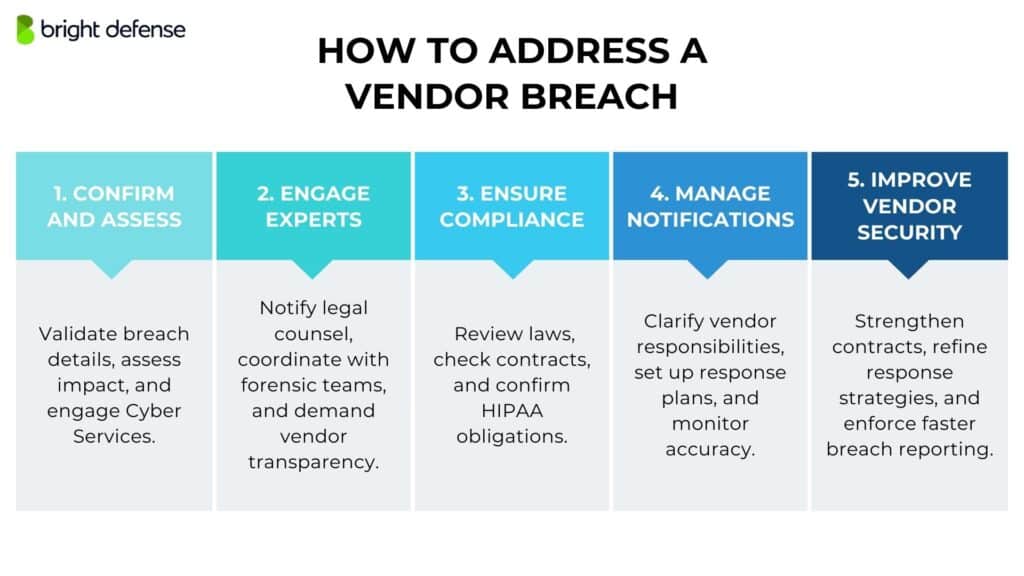
Step 1. Confirm and Assess the Breach
Once your organization learns about a potential vendor breach—whether through direct notification from the vendor, public disclosure, or internal security monitoring—the first step is to validate the information. This means:
- Reviewing the vendor’s communication for details about the breach’s scope, affected data, and possible risks.
- Determining if your data is involved by checking contractual obligations and data-sharing agreements.
- Engaging Cyber Services immediately for expert guidance on the next steps, including response strategies and containment efforts.
Step 2. Engage Legal and Forensic Experts
Since your organization may have limited control over the investigation, it’s crucial to:
- Notify breach counsel to review legal requirements, particularly regarding notification laws.
- Coordinate with forensic investigators who are already working on the breach to expedite access to findings.
- Push for timely vendor communication if they delay sharing information, ensuring your organization isn’t left in the dark.
Step 3. Identify Legal and Compliance Responsibilities
The responsibility for notifying affected individuals typically falls on your organization as the data owner. To avoid legal pitfalls:
- Review state breach notification laws to determine if a formal notice is required.
- Check vendor contracts for clauses specifying who is responsible for notifications and remediation efforts.
- Ensure HIPAA compliance if healthcare data is involved—without a Business Associate Agreement (BAA), penalties can be severe.
- Avoid rushed or incomplete notifications that could attract regulatory scrutiny or lawsuits.
Step 4. Coordinate the Notification Process
Depending on vendor policies, your organization might receive only a list of affected individuals rather than full notification assistance. To manage this effectively:
- Confirm what the vendor will handle—some may take responsibility for sending notifications, while others leave it entirely to your team.
- Engage Cyber Services to help set up notification plans, call centers, and credit monitoring if necessary.
- Monitor vendor-led notifications to ensure accuracy and maintain your organization’s reputation.
Step 5. Strengthen Future Vendor Management
A breach offers lessons for improving security and vendor oversight:
- Review vendor security practices and consider stricter requirements in future contracts.
- Assess incident response protocols to refine internal and external communication strategies.
- Mandate stronger reporting timelines for vendors to notify your organization about breaches sooner.
What to Include in Your Vendor Risk Management Framework
A solid framework goes beyond just signing contracts. It involves continuous monitoring, clear security expectations, and proactive risk assessments to ensure vendors meet compliance and security standards.
Below are the essential components every business should include to strengthen vendor security and reduce exposure to third-party risks:
1. Clear Guidelines in Vendor Contracts
Defining precise terms in third-party vendor contracts is essential. Agreements should explicitly state the nature of the partnership, data handling protocols, and security expectations.
They must specify the type of data processed, access permissions, and the measures in place to safeguard sensitive information.
Both parties should fully grasp their responsibilities and adhere to agreed-upon standards. Setting expectations for compliance audits and outlining response measures for breaches reinforces accountability.
Periodic contract reviews help keep terms relevant to changing security requirements.
2. Assessment of Your Vendor’s Security Posture
Before working with a vendor, it’s critical to evaluate their cybersecurity practices. This assessment should cover:
- Their policies,
- Their incident response strategies
- Their technical infrastructure
- Their adherence to security standards
Organizations should conduct risk evaluations, review past security incidents, and analyze vendor cybersecurity frameworks. Understanding a vendor’s security approach helps identify weaknesses that could affect your organization.
Ongoing evaluations, security questionnaires, and penetration testing enhance oversight, ensuring vendors consistently meet security obligations. Setting minimum security requirements for vendors further reduces potential risks.
3. Regulation Compliance
Vendors need to follow industry regulations and security standards that apply to your business.
Compliance with frameworks like ISO 28000 for supply chain security or ISO/IEC 27005 for risk management isn’t optional—it’s a must.
Regular audits, documented proof of compliance, and a structured system for spotting violations help keep risks in check. Keeping an eye on vendors and enforcing contract terms helps avoid legal trouble as regulations change.
4. Continuous Monitoring
Continuous monitoring is a proactive approach that involves real-time assessment of third-party vendors’ activities, performance, and compliance status. Unlike periodic evaluations, continuous monitoring enables organizations to promptly detect and address emerging risks within vendor relationships.
This process encompasses the use of automated tools and technologies to gather data from various sources, ensuring that information remains current and relevant. Continuous security scanning, risk scoring, and anomaly detection further help prevent security lapses.
Regularly reviewing security metrics and vendor reports ensures alignment with risk management goals.
5. Incident Response Collaboration
A joint incident response plan with vendors keeps security threats from turning into bigger problems. Clear communication, defined roles, and step-by-step procedures make it easier to contain and resolve issues quickly.
The plan should cover notification protocols, containment, and recovery actions. Regular simulations help both sides stay prepared for real incidents. A solid response plan limits downtime, reduces damage, and speeds up recovery. Reviewing past incidents also helps strengthen future responses.
6. Data Encryption and Access Controls
Requiring strong data encryption and strict access controls is key to protecting sensitive information shared with vendors. Encryption keeps data secure, whether stored or transmitted, blocking unauthorized access.
Vendors should follow encryption standards like AES-256 and TLS 1.2+ while using multi-factor authentication and least-privilege access models.
Regular audits of encryption practices and access logs help confirm compliance. Enforcing zero-trust policies and monitoring user permissions add another layer of security.
7. Regular Training and Awareness
Regular cybersecurity training for both your team and vendors helps keep everyone prepared for evolving threats. Training should cover:
- Phishing detection
- Social engineering risks
- Secure password habits
- Incident reporting
Security workshops, simulated attacks, and compliance refreshers keep vendors alert and accountable.
Requiring proof of completed training ensures they take it seriously. Since cyber threats never stop changing, ongoing education is key to keeping vendor networks secure.
Vendor Risk Management Best Practices in 2025
Staying ahead of vendor risks in 2025 requires more than just routine assessments. Cyber threats, regulatory shifts, and supply chain vulnerabilities continue to evolve, making it essential to tighten security measures and enforce stronger compliance.
Here’s what businesses need to prioritize to keep third-party risks under control this year:
1. Comprehensive Vendor Risk Assessments
Conducting thorough evaluations of potential vendors is essential to identifying risks related to cybersecurity, operational stability, financial health, and compliance. Utilizing standardized assessment questionnaires helps gather consistent and reliable information.
2. Continuous Monitoring
Implementing real-time monitoring systems allows organizations to track vendors’ security postures and compliance statuses. A proactive approach helps detect and mitigate emerging risks before they escalate.
3. Integration of AI and Automation
Leveraging artificial intelligence and machine learning enhances risk assessments, improves decision-making, and detects potential issues more efficiently. AI-driven systems analyze vast datasets to identify patterns indicative of emerging risks, strengthening an organization’s VRM strategy.
4. Holistic Risk Management Approach
Aligning vendor risk management with an organization’s overall risk tolerance and business objectives ensures that VRM strategies are consistent with corporate goals and risk appetite.
5. Robust Incident Response and Business Continuity Planning
Developing and maintaining comprehensive response plans helps organizations react swiftly to security incidents involving vendors. These plans should outline steps to minimize negative impacts, assess residual risks, and ensure business continuity.
6. Vendor Inventory Management
Maintaining an up-to-date inventory of all third-party relationships, categorized by risk levels, allows organizations to allocate resources effectively and focus on high-risk vendors.
7. Regulatory Compliance
Ensuring that vendors comply with relevant regulations, such as GDPR and HIPAA, helps organizations mitigate legal risks. Regular audits and assessments verify compliance and reduce the likelihood of regulatory violations.
Final Thoughts
In wrapping up, think of Vendor Risk Management (VRM) as not just a necessity but a strategic ace up your sleeve. For businesses ready to turn potential vulnerabilities into opportunities for resilience and growth, a dynamic VRM approach is key.
Don’t let vendor risks blindside you—let them be a chance to strengthen your defenses and sharpen your competitive edge. Curious about transforming your risk management strategy?
Reach out to Bright Defense, where our experts are ready to tailor a VRM solution that not only protects but propels your business forward. Let’s redefine what it means to manage risk together. Connect with us today!
FAQs
Vendor Risk Management (VRM) is the process of identifying, assessing, and mitigating risks posed by third-party vendors. It helps organizations protect their operations, finances, and data security by ensuring vendors comply with regulations and best practices.
Effective VRM involves ongoing monitoring and risk assessments to prevent potential disruptions.
The first step in the vendor risk assessment process is identifying potential vendor risks, including financial, operational, compliance, and security threats.
Next, organizations establish risk evaluation criteria to maintain consistency. Assessing the vendor’s products or services follows, ensuring they align with business needs. Involving experts from IT, legal, and finance helps gain a well-rounded perspective.
All vendors should be assessed, regardless of their size or service type. After evaluation, vendors are classified into risk levels—low, medium, or high.
A tailored risk management plan is then developed based on these classifications.
Staying updated on industry regulations ensures compliance and reduces legal risks. Lastly, organizations should perform regular vendor reassessments to identify new risks and maintain security.
Mitigating vendor risk starts with thorough due diligence before onboarding a vendor. Strong contracts with clear compliance and security terms help set expectations.
Continuous monitoring ensures vendors meet performance and security requirements, reducing potential threats. Maintaining open communication with vendors allows businesses to quickly address emerging risks.
Additionally, having contingency plans, including backup vendors and response strategies, helps organizations stay prepared for potential vendor failures or breaches.
Risk management begins by identifying potential threats that could impact business operations. Once identified, risks are analyzed to determine their likelihood and severity.
After analysis, risks are prioritized, with the most critical ones receiving immediate attention.
To mitigate risks, businesses implement preventive measures or contingency plans to reduce their impact.
Finally, ongoing monitoring and regular risk reassessments ensure risk management strategies remain effective and adaptable to changing circumstances.
Get In Touch



