
John Minnix
March 19, 2025
What is a POAM?
Cybersecurity compliance can feel overwhelming for many small and medium businesses. A Plan of Actions and Milestones, or POAM, can be a useful tool for streamlining and simplifying the compliance process.
A POAM outlines the current status of an organization’s compliance efforts. It serves as a strategic guide for identifying, prioritizing, and addressing vulnerabilities within information systems. This article explores the role of POAMs in cybersecurity and compliance programs.
Key Takeaways
- POAM simplifies compliance for small and medium businesses and aligns security efforts with frameworks like SOC 2, ISO 27001, CMMC, HIPAA, and PCI DSS.
- Prioritizing security risks with a POAM reduces breach likelihood by 60% and ensures vulnerabilities receive timely mitigation.
- Accountability improves compliance efficiency by 40%, as POAMs assign clear responsibilities for risk management.
- A 90+ day delay in mitigation increases breach risk by 35%, emphasizing the need for prompt action.
- Automation tools (e.g., Drata, JumpCloud) improve compliance tracking and provide real-time monitoring of security postures.
- POAMs are mandatory for government contractors, especially those handling Controlled Unclassified Information (CUI).
- Regular updates (quarterly or as needed) keep cybersecurity measures effective and responsive to evolving threats.
- Security training cuts human error breaches by 50%, reinforcing employee awareness as a critical cybersecurity component.
- Beyond compliance, POAMs build customer trust, protect against financial losses, and make audits more efficient.
Let’s get started!

POAM Overview
A Plan of Actions and Milestones (POAM) is crucial for any organization looking to enhance its cybersecurity compliance posture. Businesses use a systematically structured POAM to guide them through the necessary steps for securing their systems.
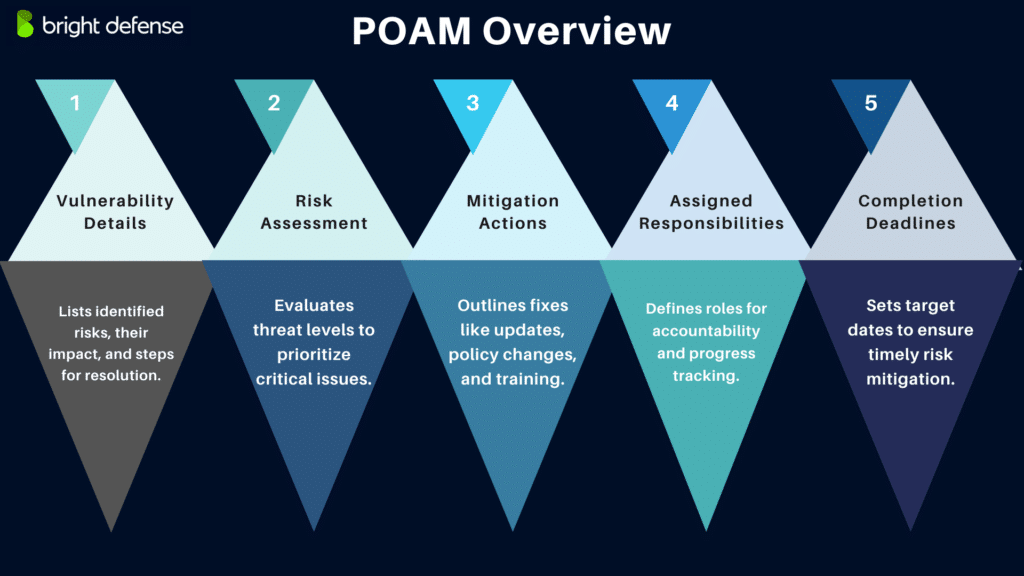
The key components of a POAM include:
- Description of Vulnerabilities: Each POAM starts with a detailed account of identified vulnerabilities. It provides insights into the discovery of each vulnerability, detailing their potential impacts on operations and the relevant details that assist in their resolution. It also outlines tasks that need completion to address vulnerabilities, specifying the required resources, milestones, and scheduled completion dates.
- Risk Assessment Results: This section assesses the risks associated with each identified vulnerability, evaluating the likelihood and impact of potential security breaches. Such assessments help to prioritize vulnerabilities, ensuring that resources are allocated first to mitigate the most critical threats.
- Proposed Mitigation Actions: For every identified risk, the POAM outlines specific remediation steps, such as software updates, configuration changes, policy adjustments, or security training for staff. These actions are tailored to effectively address each vulnerability, considering its nature and severity.
- Assignment of Responsibilities: This critical component details the responsibilities assigned to team members or departments within the organization. Clear roles ensure accountability and facilitate the tracking of progress of mitigation efforts.
- Target Dates for Completion: The POAM sets realistic scheduled completion dates for each action based on the urgency of the mitigation required. These deadlines are crucial for minimizing the window of opportunity for potential attacks and ensuring swift and effective remediation.

The Strategic Importance of a POAM in Cybersecurity Compliance
A POAM is instrumental in maintaining compliance with various regulatory frameworks and enhancing overall business operations. Some of the advantages include:
- Enhanced Communication and Coordination: A POAM fosters an environment of clear communication and coordination among all stakeholders involved. This includes internal teams, management, and external auditors. An effective POAM aligns everyone on the status of security measures and ensures they understand their roles in the mitigation process. Effective communication helps prevent overlaps in efforts and gaps in security coverage, making the compliance process more efficient.
- Link to Broader Business Objectives: Beyond compliance, a POAM is integral to achieving broader business objectives. These include enhancing customer trust, protecting brand reputation, and preventing financial losses from security breaches. By methodically addressing vulnerabilities and documenting remediation efforts, organizations can demonstrate their commitment to security. This supports stability and growth.
- Adaptability and Continuous Improvement: The dynamic nature of cybersecurity threats requires that a POAM be regularly updated and flexible enough to adapt to new vulnerabilities or changes in compliance regulations. This adaptability is crucial for maintaining an effective defense against emerging threats and ensuring continuous compliance as standards evolve.
Additionally, a POAM is essential for meeting the compliance requirements of government agencies. This especially true for contractors and subcontractors working with the Department of Defense.
POAM Checklist
Below is a step-by-step guide for implementing your POAM, including recommended tools and best practices:
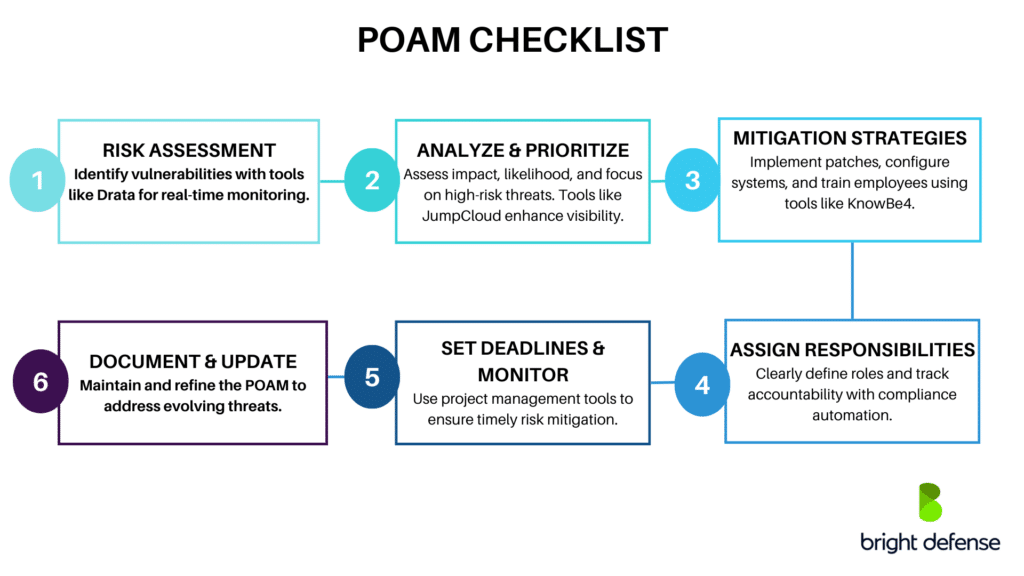
Step 1: Conduct a Thorough Risk Assessment
Begin by conducting an initial assessment to identify potential vulnerabilities within your systems. If you need assistance with your risk assessment, Bright Defense’s vCISO services can help.
Additionally, consider compliance automation tools. Tools like Drata continuously monitor and collect data across your environment, ensuring you have up-to-date information to assess risks effectively. This is ideal for businesses maintaining compliance with standards like SOC 2, ISO 27001, or HIPAA.
Step 2: Analyze and Prioritize Risks
After identifying vulnerabilities, assess each for its potential impact and the likelihood of exploitation. You can discover these weaknesses through internal vulnerability assessments, assessments by external parties, or during active breach events (hopefully not!). It’s crucial to document how each vulnerability was discovered and detected. Prioritize the vulnerabilities based on this assessment, focusing on those that pose the highest risk to your operations.
Tools like JumpCloud can help. JumpCloud provides extensive visibility into user activities and device security posture. This helps prioritize vulnerabilities based on potential business impact.
Step 3: Develop Mitigation Strategies
For each prioritized vulnerability, develop clear, actionable mitigation strategies. This could involve applying software patches, changing system configurations, or enhancing employee training programs. Use insights from risk assessment tools to shape your strategies, ensuring that each action specifically and effectively addresses the identified vulnerabilities. Enhancing employee training with tools like KnowBe4, which offers security awareness training to educate employees about various cyber threats, is also valuable.
Step 4: Assign Responsibilities
Clearly assign responsibilities for each mitigation action to specific team members or departments. Ensure that each individual understands their responsibilities and the importance of their role in the cybersecurity strategy. Compliance automation can help track and manage these assignments by documenting all compliance measures and providing a trail of accountability.
Step 5: Set Deadlines and Monitor Progress
Establish realistic deadlines for each action item based on its priority. Use project management tools or integrated features in your risk assessment tools to actively monitor progress against these deadlines, ensuring that all actions are completed on time. Regular check-ins and updates are crucial to adjust plans as necessary.
Step 6: Document and Update the POAM Regularly
Maintain a detailed record of all actions taken and their outcomes. Regularly update the POAM to reflect new information, completed tasks, and evolving threats. The POAM should document the required resources for each action, ensuring that all necessary remediation steps are clearly outlined. Additionally, regular security assessments contribute to the updates of the POAM, identifying new vulnerabilities and guiding the prioritization of tasks. This living document should serve as a central component of your cybersecurity strategy, helping to ensure continuous improvement.
Tips on Prioritizing Actions Based on Risk Assessment:
- Focus on Impact and Probability: Allocate resources first to risks that could have the most severe consequences or are most likely to occur.
- Consider Business Impact: Prioritize mitigation actions that protect the most critical business operations and data.
- Regulatory Requirements: Ensure compliance-related vulnerabilities are promptly addressed to avoid penalties.

How To Ensure Compliance with a POAM?
Ensuring compliance with a POAM involves several critical steps:
- Strict Adherence to Timelines: Follow the defined timelines for each task meticulously. Delays in completing tasks can lead to vulnerabilities being exposed for longer than necessary. It’s crucial to address security deficiencies within these timelines to mitigate risks effectively.
- Regular Audits and Reviews: Regularly conduct audits to ensure that all actions are carried out as planned and are effective in mitigating risks. Reviews should also check for completeness and accuracy of the POAM documentation.
- Training and Awareness: Educate all involved personnel about their roles in the POAM and the importance of security practices. Continuous training ensures that the team remains proficient in handling security issues.
- Resource Allocation: Allocate adequate resources—both personnel and technology—to effectively implement the POAM. Lack of resources is a common reason for non-compliance.
- Management Involvement: Encourage active involvement from management to reinforce the importance of the POAM and to ensure it receives the necessary attention and resources.
How to Write a POA&M (Plan of Action & Milestones)
A Plan of Action & Milestones (POA&M) is a structured document used to track and manage security weaknesses, compliance gaps, or risks in an organization. It outlines the problem, steps for remediation, responsible parties, and timelines. POA&Ms are commonly used in cybersecurity, government compliance, and risk management.
Step 1: Identify the Weakness or Issue
Start by clearly stating the security vulnerability or compliance gap. This should include:
- Description of the issue (e.g., missing security patches, outdated software, policy non-compliance)
- Source of identification (e.g., audit, penetration test, vulnerability scan)
- Risk level (e.g., high, medium, low)
Step 2: Assign Responsibility
Identify the person or team responsible for addressing the issue. This ensures accountability and avoids confusion.
Step 3: Define Corrective Actions
List the specific steps required to remediate the issue. Be clear and concise. For example:
- Update system software to the latest version
- Implement multi-factor authentication (MFA)
- Revise company security policy to include new compliance standards
Step 4: Set Milestones and Deadlines
Break down corrective actions into milestones with due dates. This allows for progress tracking. Example:
- Milestone 1: Install security updates (Due: March 1, 2025)
- Milestone 2: Conduct system audit to verify patch installation (Due: March 15, 2025)
Step 5: Identify Required Resources
Determine any tools, budget, or personnel needed to complete the corrective actions. If funding or approvals are required, document that in the plan.
Step 6: Track Progress and Update the POA&M
Regularly update the POA&M with the status of each action:
- Open: Issue is identified but not yet addressed
- In Progress: Remediation is underway
- Completed: The corrective action is finished and verified
- Deferred: Action is postponed due to valid reasons (e.g., awaiting funding)
Step 7: Document Any Residual Risks
If the issue cannot be fully resolved, document any remaining risks and mitigations. This helps decision-makers understand the impact and plan accordingly.
Final Thoughts
The implementation of a Plan of Actions and Milestones (POAM) is crucial in achieving and maintaining compliance. By assessing and addressing vulnerabilities, a POAM helps secure an organization’s data assets and infrastructure from emerging threats. It also demonstrates a commitment to proactive security management.
We encourage all businesses, particularly small and medium-sized enterprises, to adopt this practice as a core component of their broader cybersecurity measures. Integrating a POAM into your cybersecurity strategy helps in complying with legal and regulatory requirements. It also builds trust with clients and stakeholders by showing a dedication to maintaining robust security protocols.
Stay Secure with Bright Defense!
If you are looking to improve your cybersecurity posture, Bright Defense can help. Our team of CISSP and CISA-certified security experts will develop and execute a plan of action to meet compliance frameworks, including SOC 2, ISO 27001, CMMC, and HIPAA. Our monthly engagement model combines our vCISO expertise with compliance automation to simplify and streamline your compliance journey.
Bright Defense also offer risk assessments, business continuity planning, penetration tests, endpoint protection, and managed security awareness training. Contact us today to get started!
Sample POAM Template
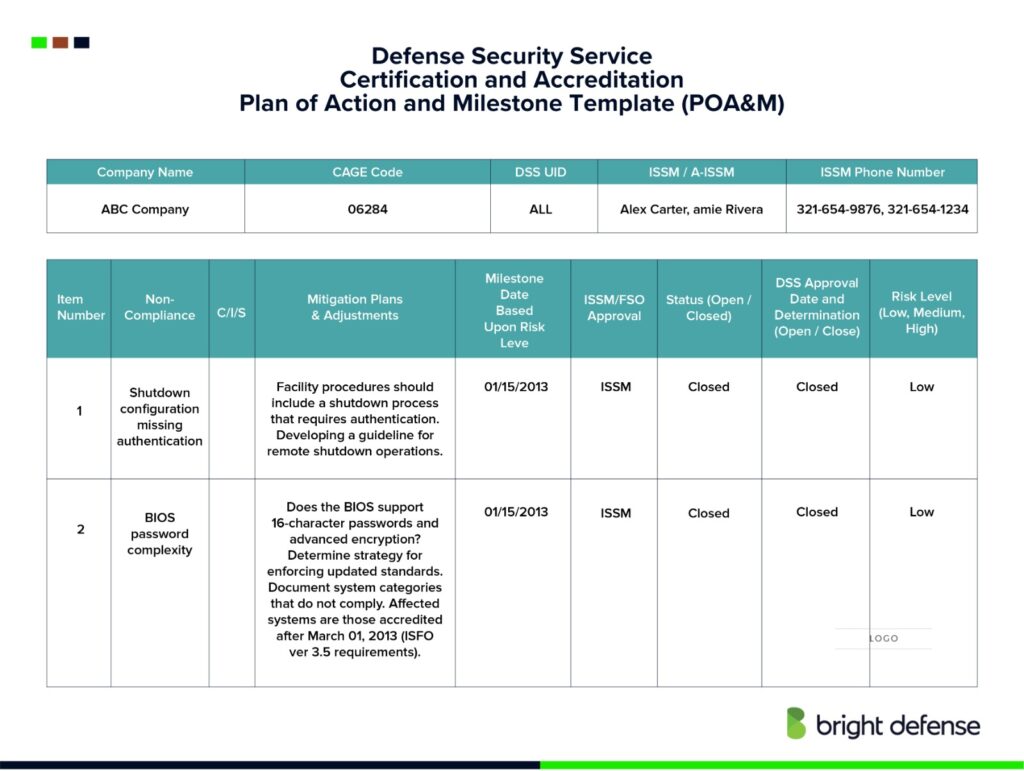
1. Document Header
- Organization Name:
- Document Creation Date:
- Last Updated Date:
- POAM ID Number:
2. Vulnerability Identification
- Vulnerability ID: (Unique identifier for tracking)
- Description: (Detailed description of the vulnerability, often highlighting system weaknesses that need to be addressed such as audit records not being exported correctly, data being improperly encrypted, or weak passwords being permitted on hardware.)
- Source of Identification: (How the vulnerability was discovered, e.g., audit, routine scan, incident response)
- System/Component Affected: (Specific system or component where the vulnerability exists)
3. Risk Assessment
- Impact Level: (High/Medium/Low – Impact of the vulnerability on the organization if exploited)
- Likelihood of Occurrence: (High/Medium/Low – Probability of the vulnerability being exploited)
- Risk Rating: (Overall risk rating derived from impact and likelihood)
4. Mitigation Strategy
- Planned Actions: (Specific actions to mitigate the vulnerability, which may involve updating or implementing new system controls as per NIST guidance to address identified system weaknesses.)
- Resources Required: (Human, technological, and financial resources necessary to implement the actions)
- Responsible Person/Team: (Names or roles of individuals or teams responsible for implementing the actions)
5. Implementation Timeline
- Start Date: (When the mitigation actions will begin)
- Target End Date: (Deadline for completing the mitigation actions)
- Milestones: (Key stages of the mitigation process and their expected completion dates)
6. Progress Tracking
- Status Updates: (Regular updates on the progress of the mitigation actions)
- Challenges/Issues: (Any challenges or issues encountered during the implementation)
- Revised Actions: (Adjustments to the planned actions if necessary)
7. Final Review and Closure
- Outcome: (Results of the mitigation efforts upon completion)
- Effectiveness Review: (Evaluation of the effectiveness of the actions taken)
- Closure Date: (Date when the vulnerability is considered fully addressed and the POAM is closed)
8. Approval
- Prepared By: (Name and signature of the person who prepared the POAM)
- Reviewed By: (Name and signature of the person who reviewed the POAM)
- Approved By: (Name and signature of the person who approved the POAM)

Frequently Asked Questions (FAQ)
What is the definition of POAM?
A Plan of Actions and Milestones (POAM full form) is a document that outlines specific steps an organization intends to take to address and mitigate security vulnerabilities within its systems. It serves as a roadmap for implementing security improvements and is crucial for tracking progress toward compliance with cybersecurity standards.
How often should a POAM be updated?
You should regularly update a POAM to reflect the progress of mitigation actions, the emergence of new vulnerabilities, changes in business processes, or shifts in compliance requirements. We typically recommend updating a POAM quarterly. However, the frequency can increase depending on the dynamic nature of the organization’s environment and the severity of the vulnerabilities. Regular updates ensure that the POAM remains relevant and that the organization can adapt to new threats and changes effectively.
What is a System Security Plan (SSP)?
A System Security Plan (SSP) is a formal document that details the security controls in place for an organization’s system. It describes the system environment, system responsibilities, and the security policies and controls designed to protect the system.
How does a POAM relate to Cybersecurity Maturity Model Certification (CMMC) compliance?
For organizations seeking CMMC (Cybersecurity Maturity Model Certification) compliance, a POAM helps document corrective actions for meeting the required security controls and practices. It is especially crucial for DoD contractors who must meet specific cybersecurity requirements to maintain eligibility for government contracts.
Why are POAMs important for government contracts?
POAMs are critical for government contracts because they demonstrate an organization’s commitment to meeting the stringent security requirements mandated by federal agencies. Handling Controlled Unclassified Information (CUI) often requires them. They are crucial for ensuring the protection of sensitive government data. Additionally, POAMs help ensure the protection of sensitive information, addressing the needs of DoD contractors to safeguard data beyond classified levels, in compliance with the highest cybersecurity standards governed by CMMC Level 3, including DFARS 252.204-7012 rules and measures against APTs.
What should be included in a corrective action plan?
A corrective action plan within a POAM should include a detailed account of vulnerabilities, the measures planned to address these vulnerabilities, timelines for implementing these measures, and the assignment of responsibilities to ensure accountability. Additionally, third-party assessment organizations (3PAO) play a crucial role in evaluating the effectiveness of these corrective actions, particularly in verifying mitigation efforts and certifying compliance with standards such as CMMC.
How should organizations document their progress in a POAM?
Organizations should document their progress by updating the POAM with completed tasks, newly identified vulnerabilities, and revisions to the mitigation strategies as necessary. This ongoing documentation helps maintain operational transparency and compliance with security requirements.
What resources are necessary for implementing a POAM?
Implementing a POAM typically requires both human and technological resources. Human resources involve personnel responsible for executing tasks and overseeing the process, while technological resources may include security tools and systems for monitoring and enforcing security controls.
What is the role of milestones in a POAM?
Milestones in a POAM indicate key points of achievement within the plan. They gauge progress toward the ultimate goal of mitigating all identified vulnerabilities and play a crucial role in ensuring that corrective actions are completed on schedule.
Get In Touch



