Tamzid Ahmed | Security and Compliance Writer
April 18, 2025
What is an Authority to Operate (ATO)?
ATO (Authority to Operate) is an official approval that a system meets all necessary security standards and can handle sensitive information without posing unacceptable security and privacy risks.
In simpler terms, it gives the official go-ahead that your information system has an acceptable security posture and meets the strict security requirements federal agencies demand.
If you’re dealing with federal government contracts, cloud service deployments, or compliance-heavy industries, getting an Authority to Operate (ATO) is mandatory. Without it, your system stays grounded.
In this blog, we’ll break down what an ATO really means, why it plays a critical role in cyber and network security, and what it takes to earn one. Whether you’re working through FedRAMP, the NIST Risk Management Framework, or DoD systems, this is the clarity you need.
What is an Authority to Operate (ATO)?
An Authority to Operate (ATO) is an official authorization granted to a system, allowing it to be used within a specific environment, typically in federal agencies or other regulated sectors.
This official management decision confirms that the system has implemented the required security controls and meets the standards of risk management framework protocols. It ensures the system is secure enough to handle sensitive information without introducing unacceptable security and privacy risks.
Example: Let’s say Amazon Web Services (AWS) wants to offer its cloud services to U.S. federal agencies. Before any agency can use AWS to store or process government data, AWS must go through a FedRAMP (Federal Risk and Authorization Management Program) authorization process.
This process involves:
- A full Security Assessment Report (SAR)
- Documentation of all relevant security controls and identified risks
- Independent testing by a Third-Party Assessment Organization (3PAO)
- Defined continuous monitoring requirements
Once AWS proves that its services meet all required security standards, it can receive an ATO from a federal agency (like the Department of Homeland Security).
This ATO confirms that AWS has an acceptable system security posture and is officially approved to operate within that agency’s information systems, handling sensitive data safely.
Without the ATO, AWS wouldn’t be allowed to serve federal clients under FedRAMP. That’s how critical the ATO process is. It acts as the gatekeeper between any system and the secure, regulated environments it’s trying to access.
The ATO Application Process
The federal government uses the Authority to Operate (ATO) process to rigorously evaluate information systems. Security teams build this process around the NIST Risk Management Framework (RMF) to confirm the system can securely process, store, or transmit sensitive information.
Here’s a detailed breakdown of each step involved:
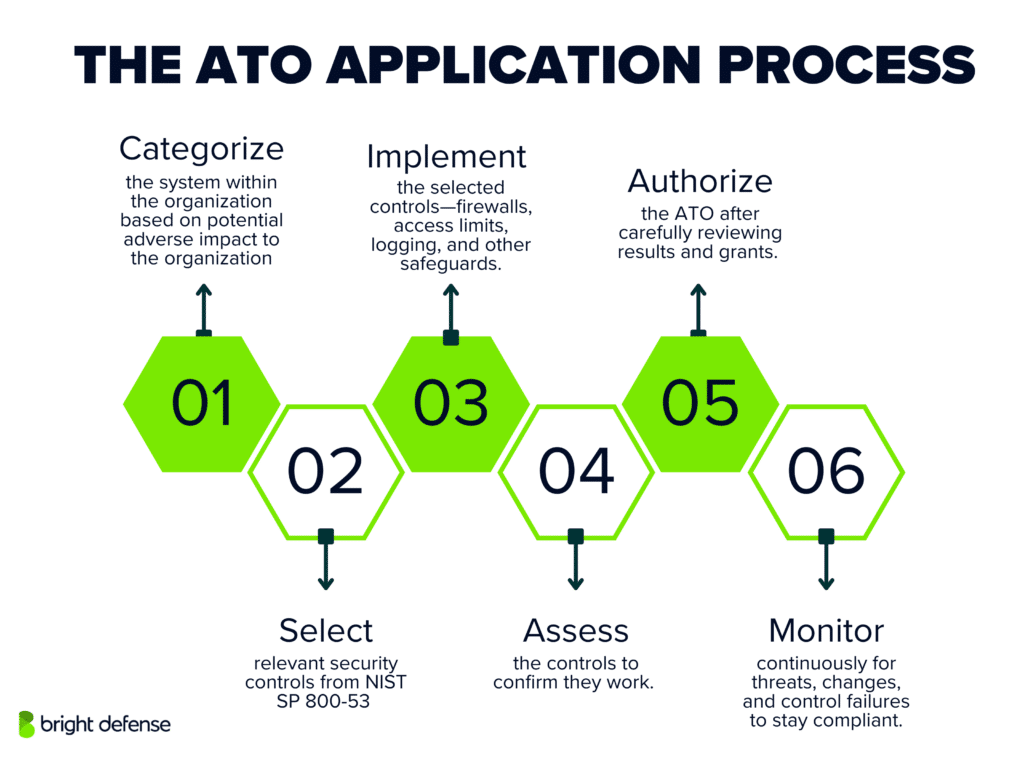
Step 1: System Categorization
The ATO process begins with system categorization based on the sensitivity of the information systems involved. This classification follows FIPS 199 guidelines, which evaluate three critical components: confidentiality, integrity, and availability.
Each factor is rated as low, moderate, or high impact, depending on the potential damage a breach could cause to agency operations, agency assets, or individuals. This step lays the foundation for determining the appropriate security requirements and aligning the system with the broader risk management framework used by federal agencies.
Step 2: Select Security Controls
Once the system is categorized, the appropriate baseline security controls are selected using NIST SP 800-53. These controls cover various areas such as access control, incident response, audit logging, and configuration management.
However, security teams don’t apply these controls blindly. They adjust them to fit the system’s architecture and operational needs. They also identify which controls they inherit from other systems, like cloud infrastructure, and then focus on implementing the remaining ones themselves.
Step 3: Implement Security Controls
With the security controls selected, they are now implemented within the system. This includes technical measures like
- Firewalls
- Encryption
- Access restrictions
- Multi-factor authentication
- Administrative safeguards like security policies and training programs
Documentation is key here. The team describes how they implement each control in the System Security Plan (SSP) and develops supporting materials like network diagrams and data flow charts to present a complete picture of the security architecture.. Additionally, it is crucial to identify and provide the necessary documentation required at various stages to ensure compliance and successful authorization processes.
Step 4: Assess Security Controls
After implementation, the controls must undergo a comprehensive evaluation to ensure they work as expected. A security assessment is carried out, often by a third-party assessment organization (3PAO), using predefined methods outlined in a Security Assessment Plan (SAP).
The evaluation includes penetration testing, vulnerability scans, and interviews with system stakeholders. Results are compiled into a Security Assessment Report (SAR), and any weaknesses are documented in a Plan of Action and Milestones (POA&M), which outlines how and when those issues will be addressed.
Step 5: Authorization Decision
The organization submits all documentation, the SSP, SAR, and POA&M, to the Authorizing Official (AO), who decides whether the system’s operational risk is acceptable. If the AO finds the security posture and risk mitigation strategy adequate, they issue an ATO.
In some cases, when residual risks remain but are manageable short term, the AO grants a Conditional ATO with specific actions to complete within a set timeline. The AO explicitly accepts these residual risks based on thorough assessments and implemented security controls.
Step 6: Continuous Monitoring
An ATO isn’t a one-time event. Once a system is authorized, continuous monitoring kicks in to ensure that the security controls remain effective over time. This includes regular vulnerability scans, log analysis, patch management, and reassessment of risk as the system or its environment changes.
Documentation is updated as needed, and significant changes to the system may trigger a reauthorization process. The goal is to stay ahead of threats and maintain compliance with evolving security requirements.
It is crucial to keep the current ATO updated and renewed as it nears expiration to ensure ongoing compliance and security.
What Happens After Authorization?
Getting an ATO doesn’t mean the job’s done, it just means the system is officially allowed to operate under current conditions. What follows is an ongoing responsibility to keep that system secure and compliant.
Ongoing authorization (OA) is crucial here, as it shifts from a reactive evaluation model to continuous monitoring, reducing the burden on project teams by providing real-time data on security posture and allowing for automated risk assessment.
Right after authorization, your team shifts into maintenance mode, but not the “set-it-and-forget-it” kind. You’re now expected to actively monitor the system’s health, track any new vulnerabilities, and respond to emerging threats in real time. Think of it like running a security checkpoint that never closes.
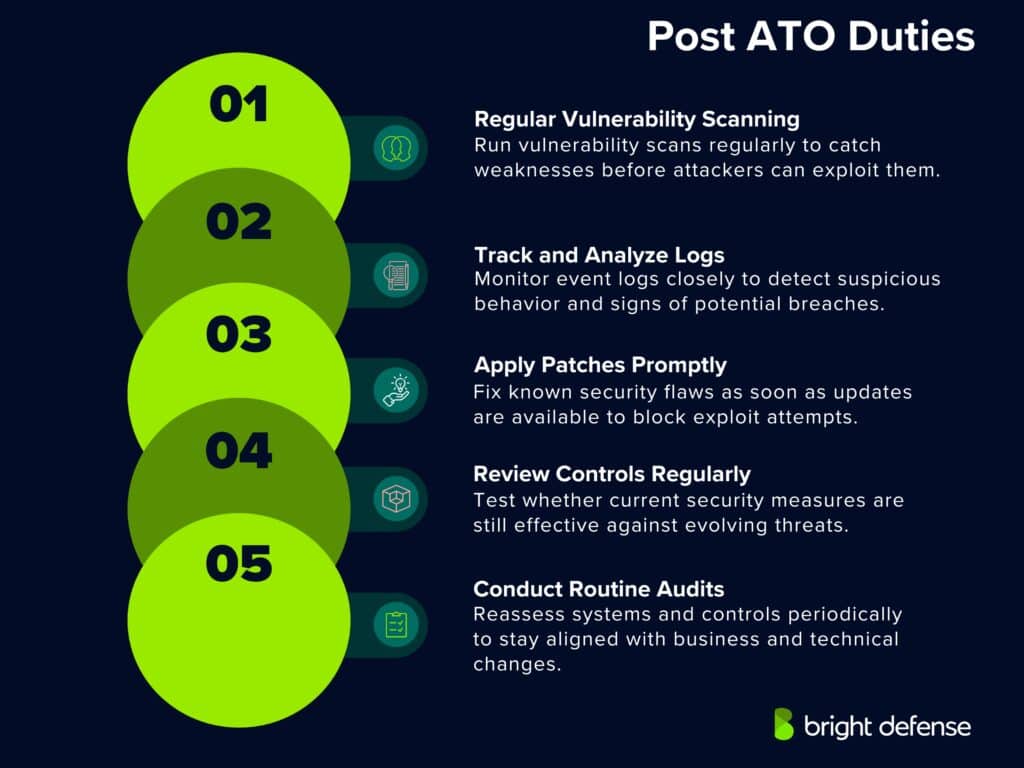
Key post-authorization tasks include:
- Ongoing vulnerability scans to catch weaknesses before attackers do
- Event logging and analysis to detect suspicious behavior or potential breaches
- Patch and update management to fix known flaws as soon as possible
- Control effectiveness reviews to verify whether the originally implemented measures are still doing their job
- Periodic reassessments and audits to keep everything in check as business or technical conditions evolve
If major changes occur, like a shift in the hosting environment, a redesign of the network, or a new set of integrations, you may have to update the System Security Plan and potentially seek reauthorization.
In short, after authorization, the focus shifts from proving the system is secure to proving it stays secure. If you slack on the continuous monitoring, that ATO can be pulled, and you’re back to square one.
ATO Review and Certification
The ATO review and certification is the final checkpoint before a system goes live. At this stage, the Authorizing Official (AO) thoroughly evaluates all documentation, including the System Security Plan (SSP), Security Assessment Report (SAR), and the Plan of Action and Milestones (POA&M).
The AO reviews the system’s overall security posture, assesses the residual risks, and considers the mitigation strategies in place. If everything meets the standards and the risks fall within acceptable limits, the AO grants the Authority to Operate.
In some cases, when manageable risks remain unresolved, the AO may issue a Conditional ATO with strict remediation deadlines. Without this approval, the system cannot legally operate in a federal environment.
Importance of ATO in Cybersecurity
An Authority to Operate isn’t just a stamp of approval, it’s a critical checkpoint in cybersecurity. It confirms that a system can be trusted to handle sensitive information without exposing the organization to unnecessary risk.
Here’s why ATO holds real weight in any security-focused environment:
1. Confirms Security Readiness
Agencies don’t hand out an ATO casually. It shows the team has applied, tested, and documented every critical security control. They’ve run the system through a structured evaluation without skipping anything.
Instead of relying on assumptions or shortcuts, they examine everything from encryption protocols to access restrictions and confirm each one works as intended. This review helps them weed out weak points.
2. Protects Against Cyber Threats
Cyber threats don’t wait for approval. An ATO makes sure your system isn’t caught flat-footed. It involves firewalls, threat detection tools, access control, and incident response plans working together.
These aren’t added for show; they’re part of a bigger picture to prevent breaches, contain attacks, and recover fast. Without this protection in place, adversaries can exploit vulnerabilities, leaving the door wide open for attackers.
3. Meets Federal Compliance Requirements
If you’re working with government data, you’re not operating legally without an ATO. Compliance with FISMA, NIST RMF, or FedRAMP isn’t just policy, it’s enforced. These frameworks require documented evidence that your system is secure, and the ATO is the stamp that proves it. No ATO means no authority to operate, period.
The National Institute of Standards and Technology (NIST) plays a crucial role in establishing these security frameworks and controls, ensuring organizations meet federal regulations.
4. Keeps Risk Management Active
Security isn’t static. Threats change, systems evolve, and new vulnerabilities show up daily. The ATO process forces you to keep security in motion.
This means reassessments, real-time monitoring, threat analysis, and system updates stay on your radar to address evolving threats. A system that was secure six months ago can’t be trusted today unless it’s been kept in check.
5. Holds People Accountable
Getting an Authority to Operate (ATO) is a process that involves people taking ownership of their responsibilities. The system owner, information system security officer, security team, developers, executives, and the project team all contribute to the system’s security posture.
This shared responsibility prevents gaps in oversight and reduces the likelihood of security incidents. Everyone understands their role in meeting the required security measures and following the authorization process.
6. Builds Operational Confidence
An approved ATO shows that a system’s security posture has been thoroughly evaluated and documented, ensuring that all required security controls are met and the system can be trusted. Other federal agencies, partners, and users can use the system with confidence that it can handle sensitive information safely.
This improves collaboration and integration across systems and reduces friction during mission-focused tasks. Without the proper authorization, the system may be excluded from essential operations.
What is denial of authorization to operate?
Denial of authorization to operate means the system did not meet the required security standards. As a result, the Authorizing Official issues a formal decision to withhold the Authority to Operate.
The system is not allowed to function within federal environments until identified security issues are resolved, relevant documentation is updated, and a new security assessment report is submitted.
What is an ATO contract?
An ATO contract is a formal agreement in which a vendor agrees to complete all steps of the ATO process. This includes implementing required security controls, submitting the authorization package, and undergoing independent assessment.
The contract defines deadlines, roles such as the system owner and information system security officer, and outlines all security requirements needed to support federal agency operations.
Final Thoughts
An Authority to Operate is the foundation of trust in any federal IT system. It confirms that the system is secure, compliant, and capable of protecting sensitive information without introducing unnecessary security and privacy risks.
Whether the goal is FedRAMP, the NIST Risk Management Framework, or Department of Defense compliance, obtaining an ATO shows that the system aligns with required security standards.
System authorization is a critical part of the ATO process, where a senior agency official reviews and approves the system’s security controls and risks.
Once granted, the responsibility shifts to ongoing management. Maintaining the ATO involves continuous monitoring, addressing emerging threats, and ensuring all relevant security controls remain effective.
Without a valid ATO, the system cannot legally operate within federal agencies or process data in regulated environments.
FAQs
ATO stands for Authority to Operate. It is formal authorization granted by a federal agency or the Joint Authorization Board under FedRAMP.
This approval allows a system or service, often a cloud-based product, to operate within federal environments.
It confirms that the system has implemented all required security controls and meets the standards outlined in the risk management framework.
FedRAMP is the Federal Risk and Authorization Management Program. It provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products used by federal agencies.
A federal agency or authorizing official makes the final decision to issue an ATO, confirming that a system meets FedRAMP security requirements and is approved to operate.
A cybersecurity risk assessment is the process of identifying potential cyber threats, evaluating how likely they are to exploit network vulnerabilities, and determining the possible impact on information systems.
This process helps organizations manage risk by identifying weaknesses in their security posture and applying the necessary security measures before attackers can gain access to sensitive information.
Get In Touch